Palo Alto Networks CEO Nikesh Arora told CNBC on Friday that every business and federal agency needs to take stock of their network security in the wake of the suspected Russian massive cyberattack.
The security executive's comments follow the revelation that federal agencies, reportedly including the one overseeing the nation's nuclear weapons stockpile, were victims of a sophisticated cyberattack. Some experts believe Russia was behind the breach, which began months ago, although the official government investigation is ongoing and no determinations have been announced.
"We've got to make sure we're secure. Before we try to go ahead and try to do anything else, ... every organization, every agency has to go through and make sure that they are not impacted," Arora said on "Squawk on the Street." "If they have an iota of doubt on the fact that they may be impacted, they've got to make sure they secure their infrastructure. They also have to be prepared for this if it happens again. I don't think it's the last one we're going to see."
The hackers gained access to networks through a piece of enterprise network management software from Austin, Texas-based SolarWinds called Orion, according to the Cybersecurity and Infrastructure Security Agency. Up to 18,000 customers using SolarWinds Orin downloaded a software update that had malicious code inserted by hackers, according to Reuters. The news organization also reported Microsoft was hacked as part of the operation.
"CISA has determined that this threat poses a grave risk to the Federal Government and state, local, tribal, and territorial governments as well as critical infrastructure entities and other private sector organizations," the U.S. cybersecurity agency said Thursday.
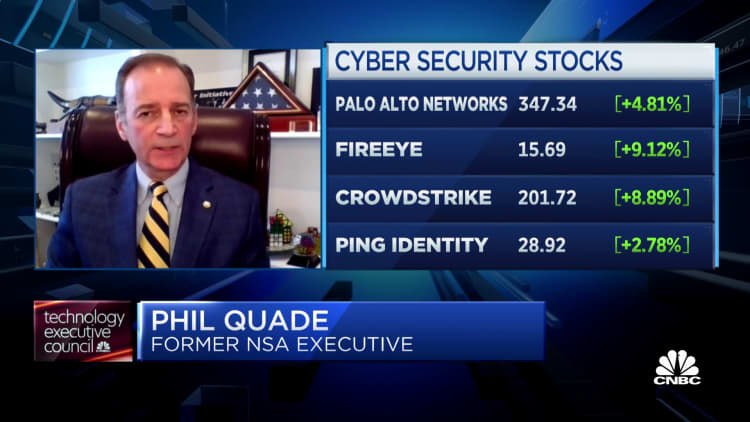
Understanding the consequences of the breach — what information the hackers were able to obtain — will likely come first from individual companies that were affected, according to Phil Quade, chief information security officer at cybersecurity firm Fortinet.
"They'll need to do some deep analysis of their systems looking for whether they .. simply had a tool placed on target, meaning were they exploited, or did they have data that was taken from their repositories and will be used at a later time?" Quade said later on "Squawk on the Street."
"That damage assessment will come a lot sooner likely than a government assessment of who is behind it definitely and what they took," said Quade, who prior to joining Sunnyvale, California-based Fortinet worked at the National Security Agency, which is part of the Department of Defense.