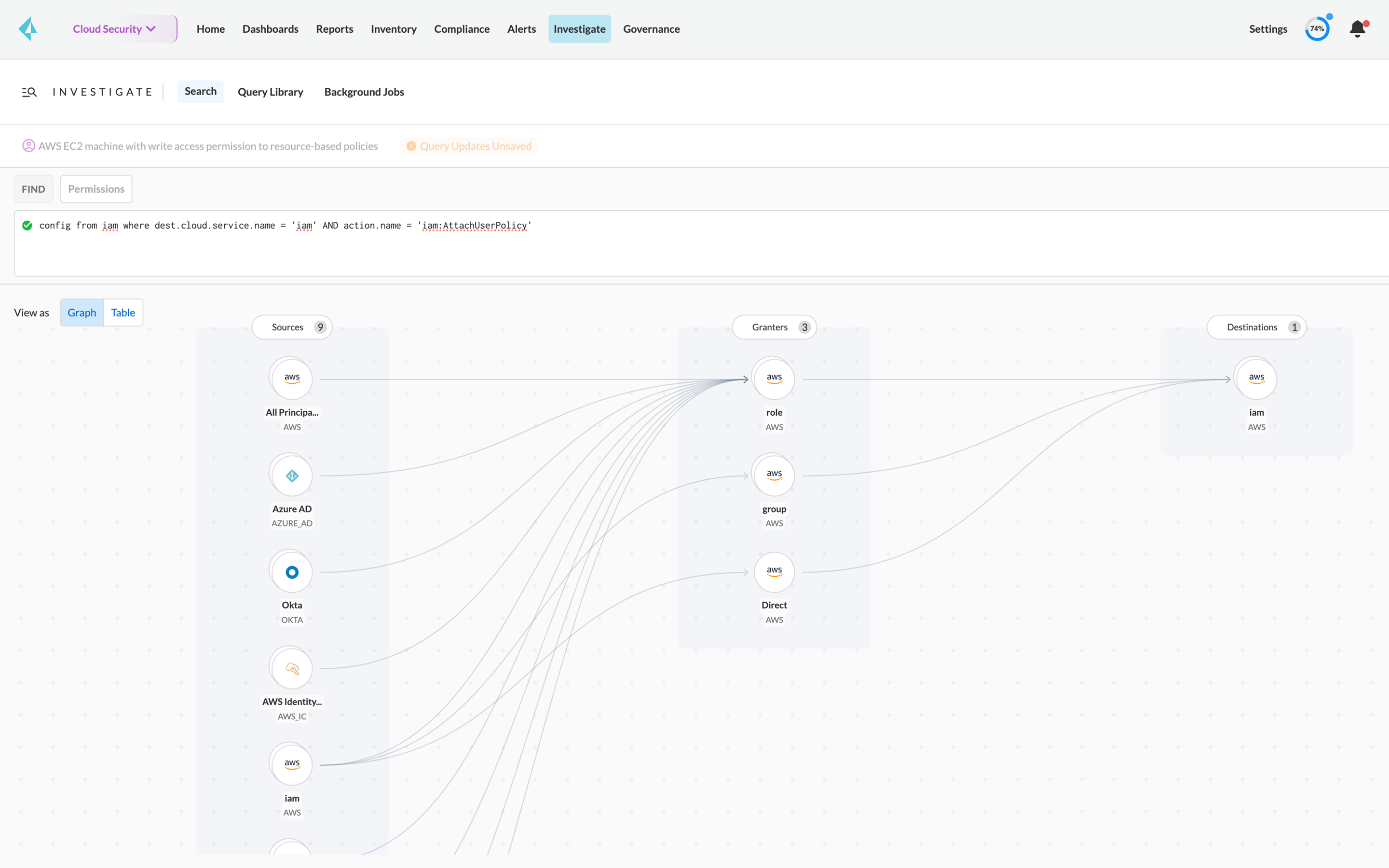
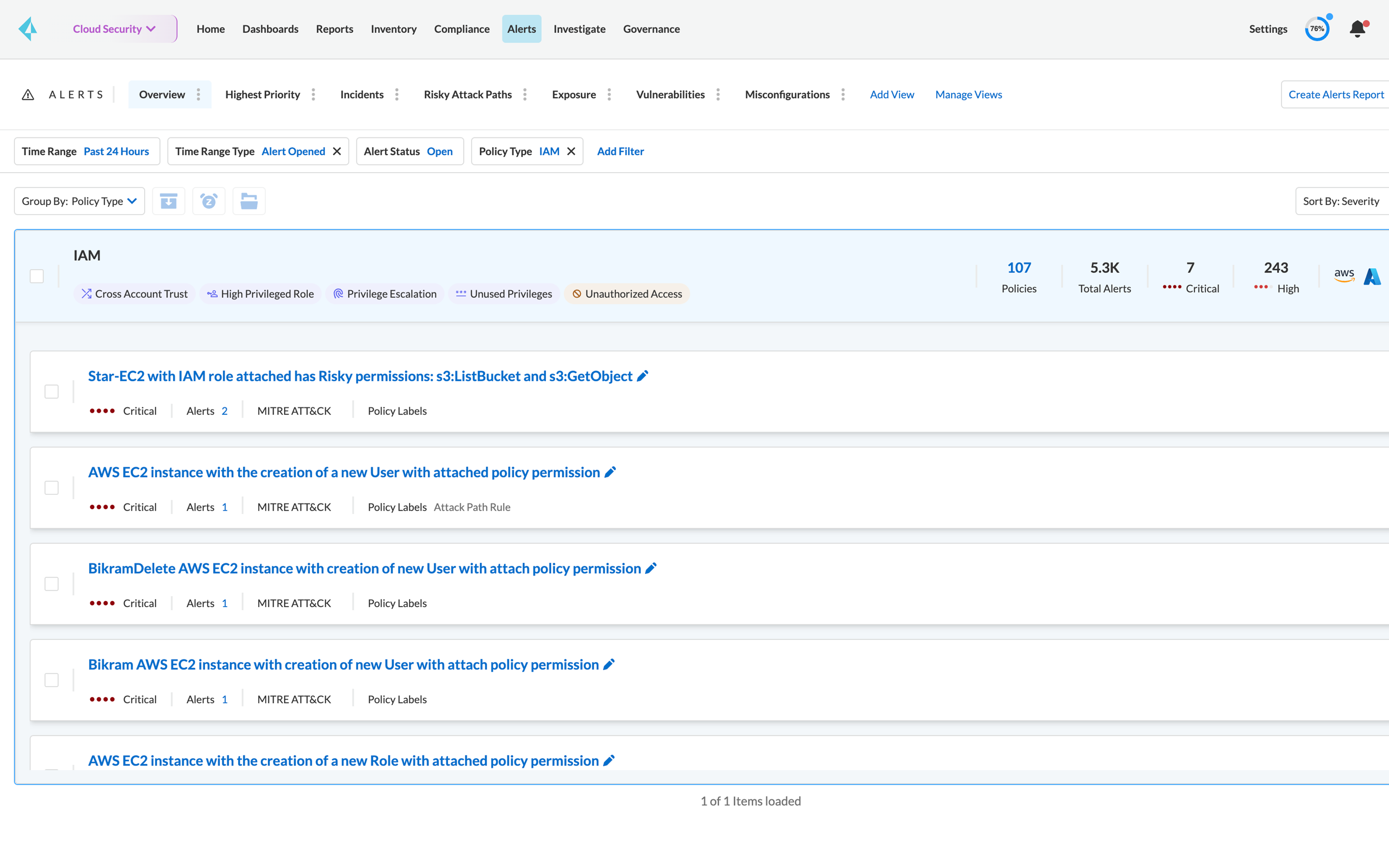
Net-effective permissions
Gain comprehensive visibility into who can take what actions on which resources. CIEM is purpose-built to directly solve the challenges of managing permissions across AWS, Azure, and GCP. Prisma Cloud automatically calculates users' effective permissions across cloud service providers, detects overly permissive access, and suggests corrections to reach least privilege.
Manage multicloud entitlements from a single solution
Gain integrated multicloud capabilities delivered from Prisma Cloud that extend everything we do for Cloud Security Posture Management (CSPM) to cloud identities.
Implement pre-built policies
Leverage specialized out-of-the-box policies to detect risky permissions and remove unwanted access to cloud resources.
Audit permissions for internal compliance
Quickly audit cloud permissions with related user data, service data and cloud accounts.