Network Security Posture Management
Prisma Cloud offers end-to-end visibility of cloud networks across Amazon Web Services (AWS), Microsoft Azure and Google Compute Platform (GCP) deployments.
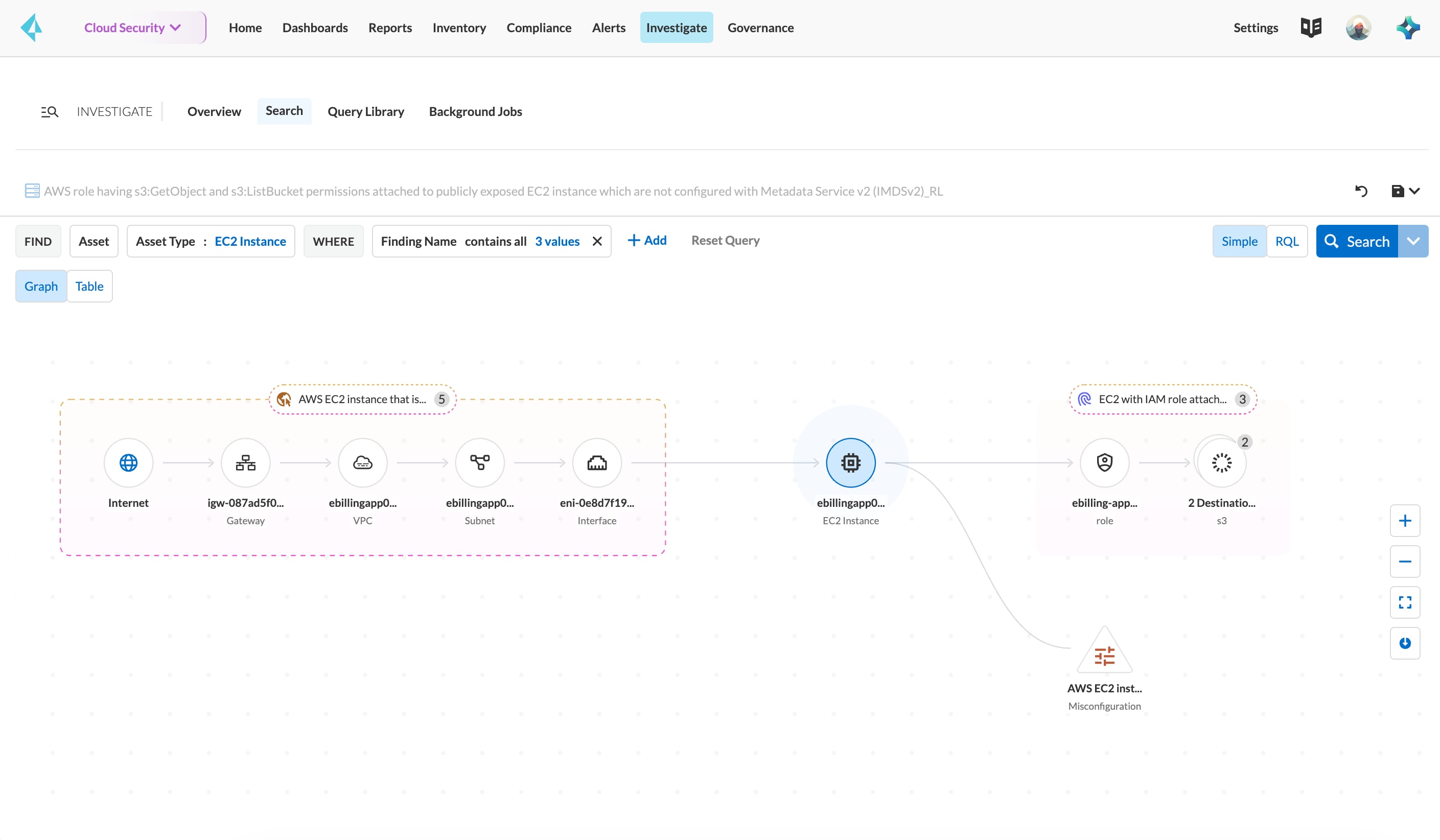
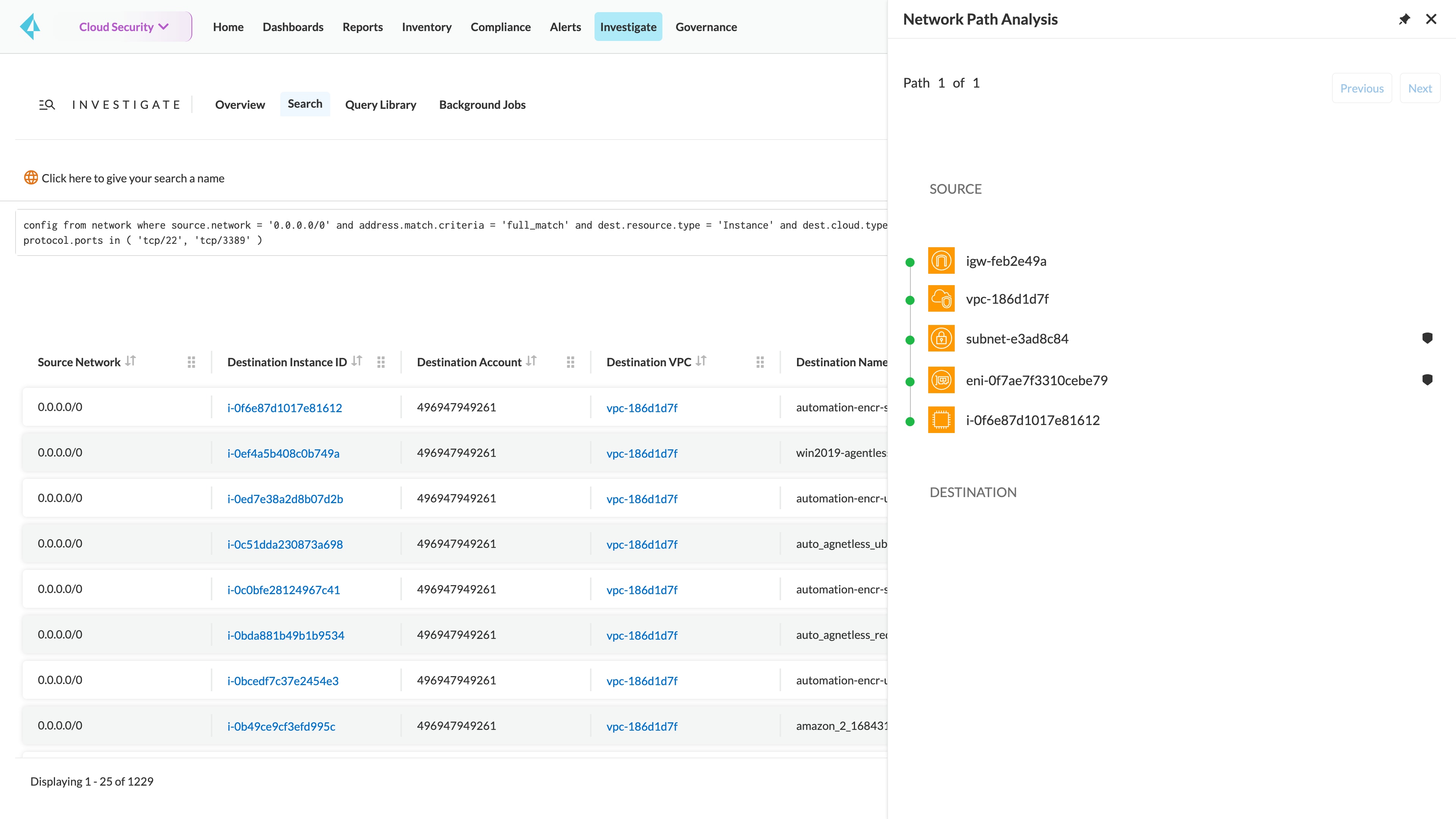
Network configuration and asset visibility
Know about the assets and network configurations deployed across multicloud environments.
Configuration change monitoring
Unlike scanning technologies that take infrequent snapshots, Prisma Cloud continuously monitors environments, enabling security teams to track network misconfigurations, when they happened and who changed them.
Flow mapping
Visualize any network communication across your clouds. Prisma Cloud collects cloud provider network flow logs and builds a map of communications, including traffic to and from untrusted sources or malicious IP addresses.
Remediation guidance
Reduce cross-collaboration friction and increase remediation efficiency. Prisma Cloud delivers step-by-step remediation instructions, providing context for the teams who are responsible for network misconfigurations.