Find stealthy threats fast
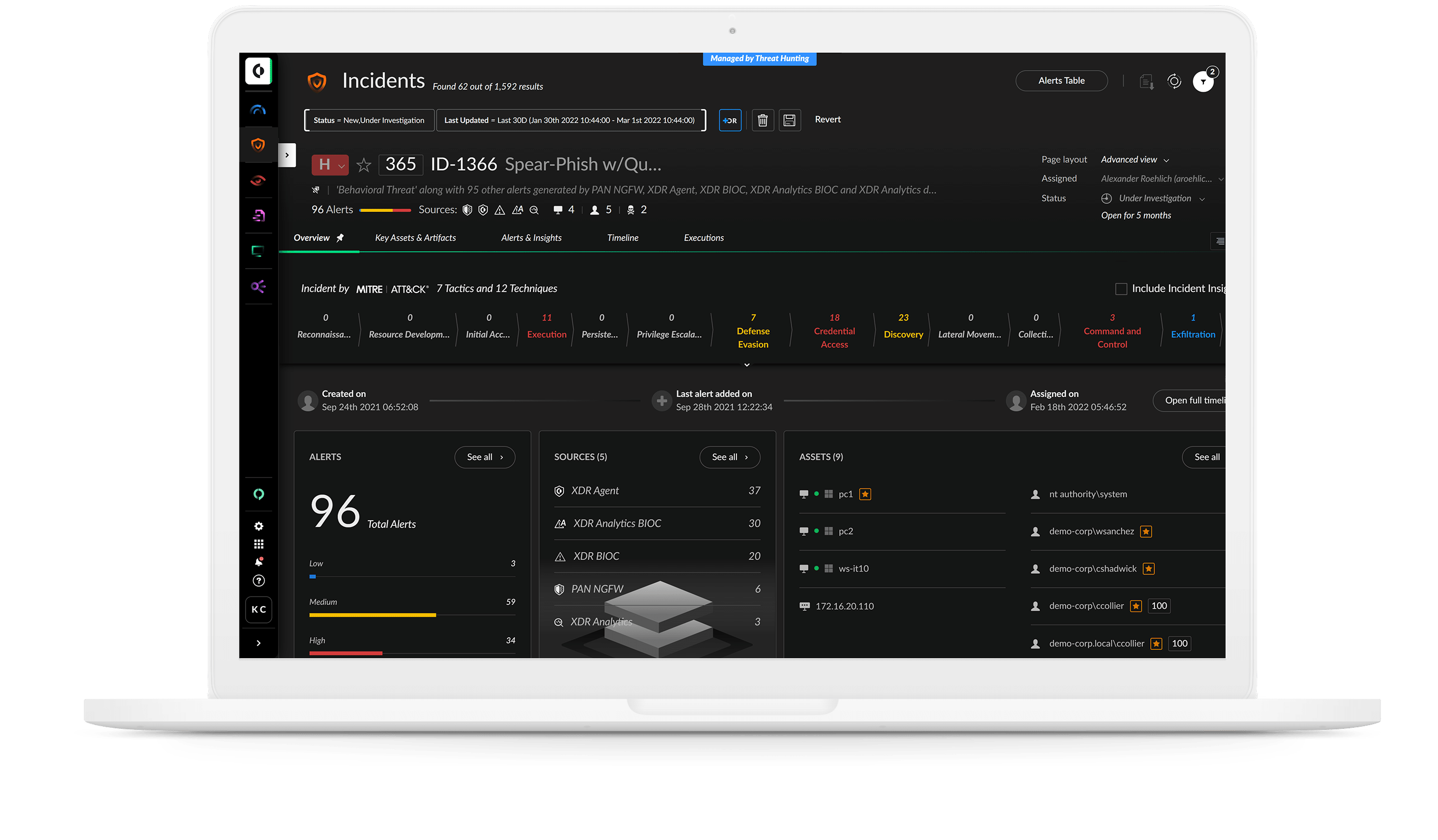
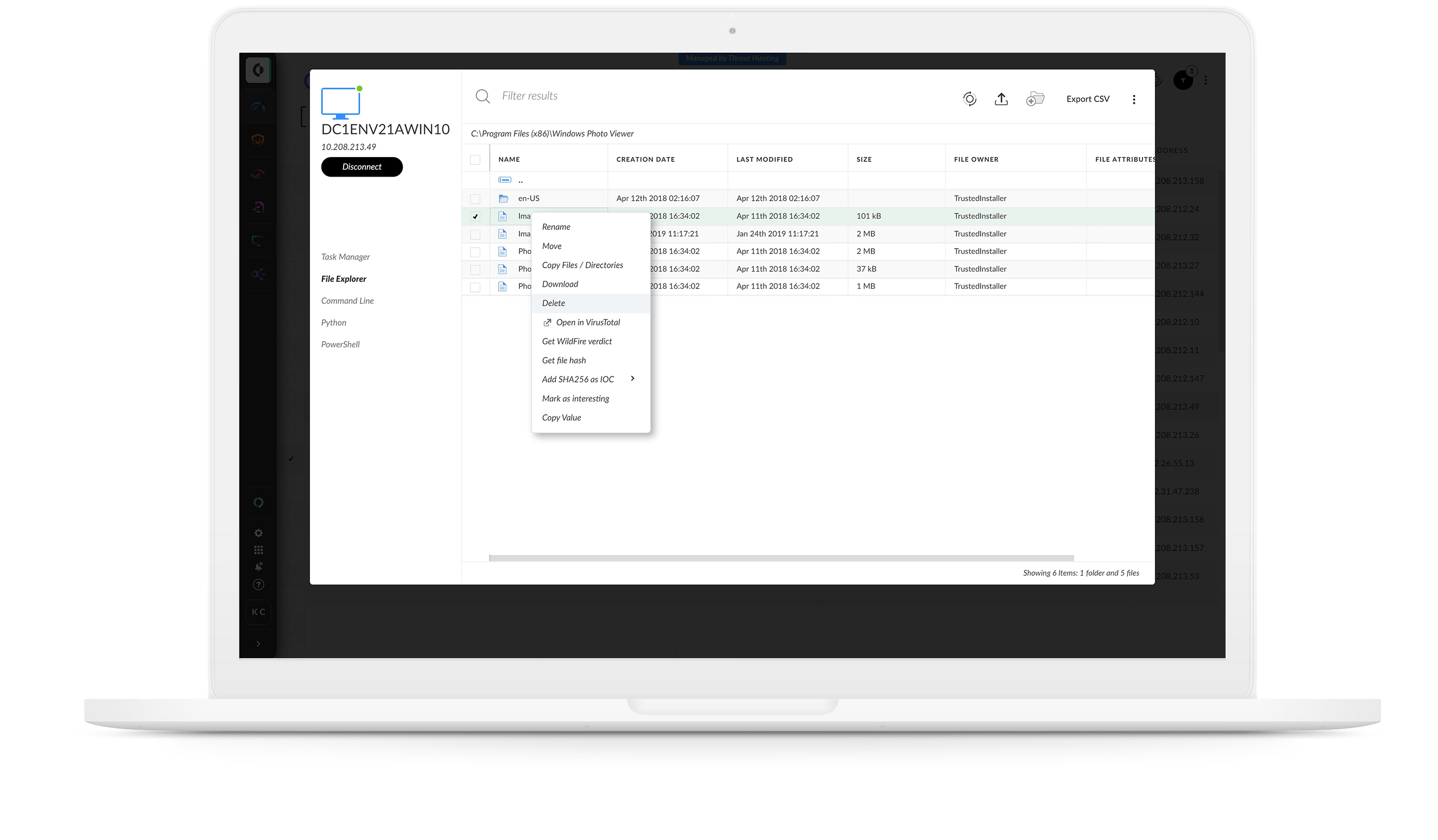
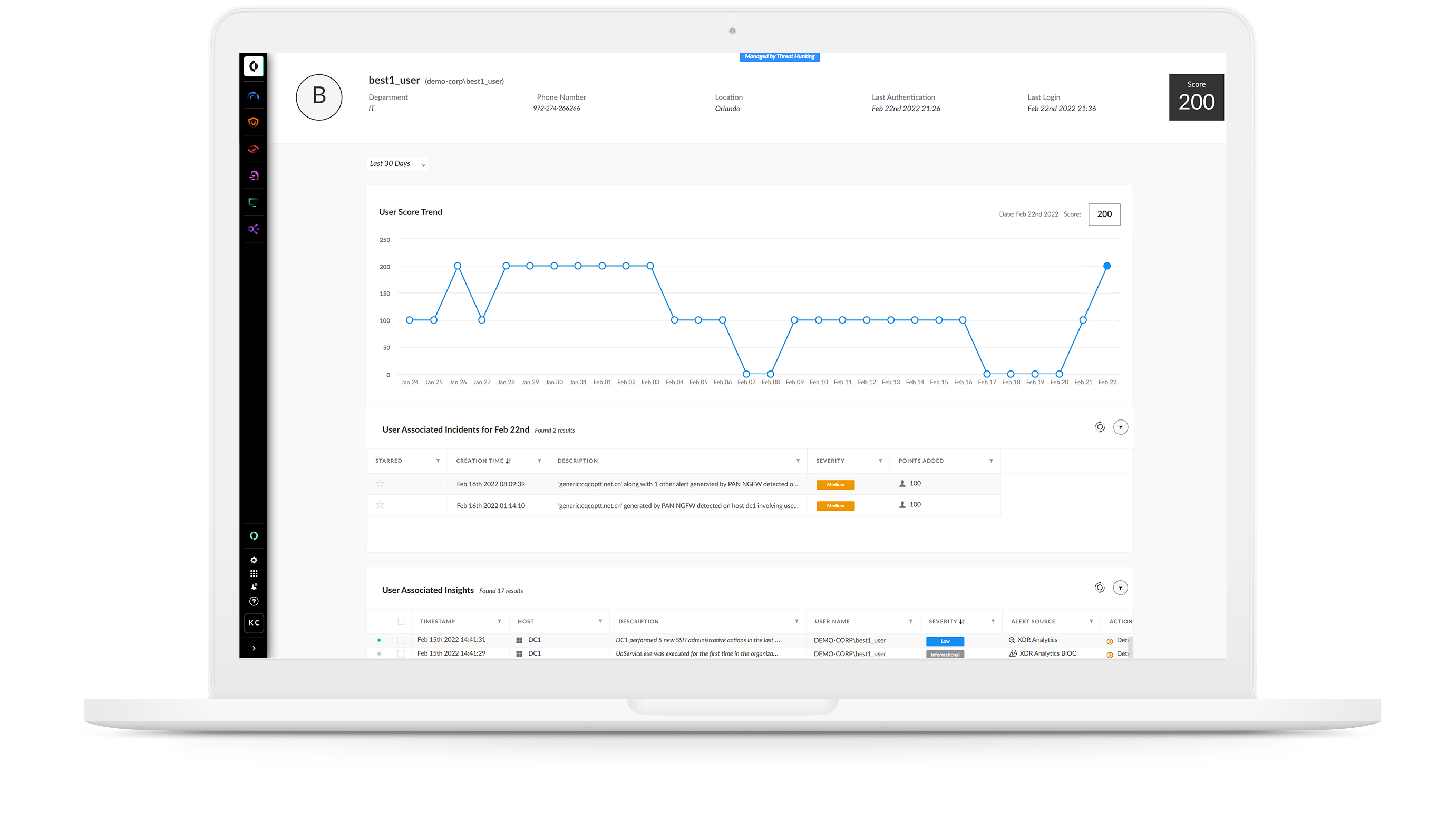
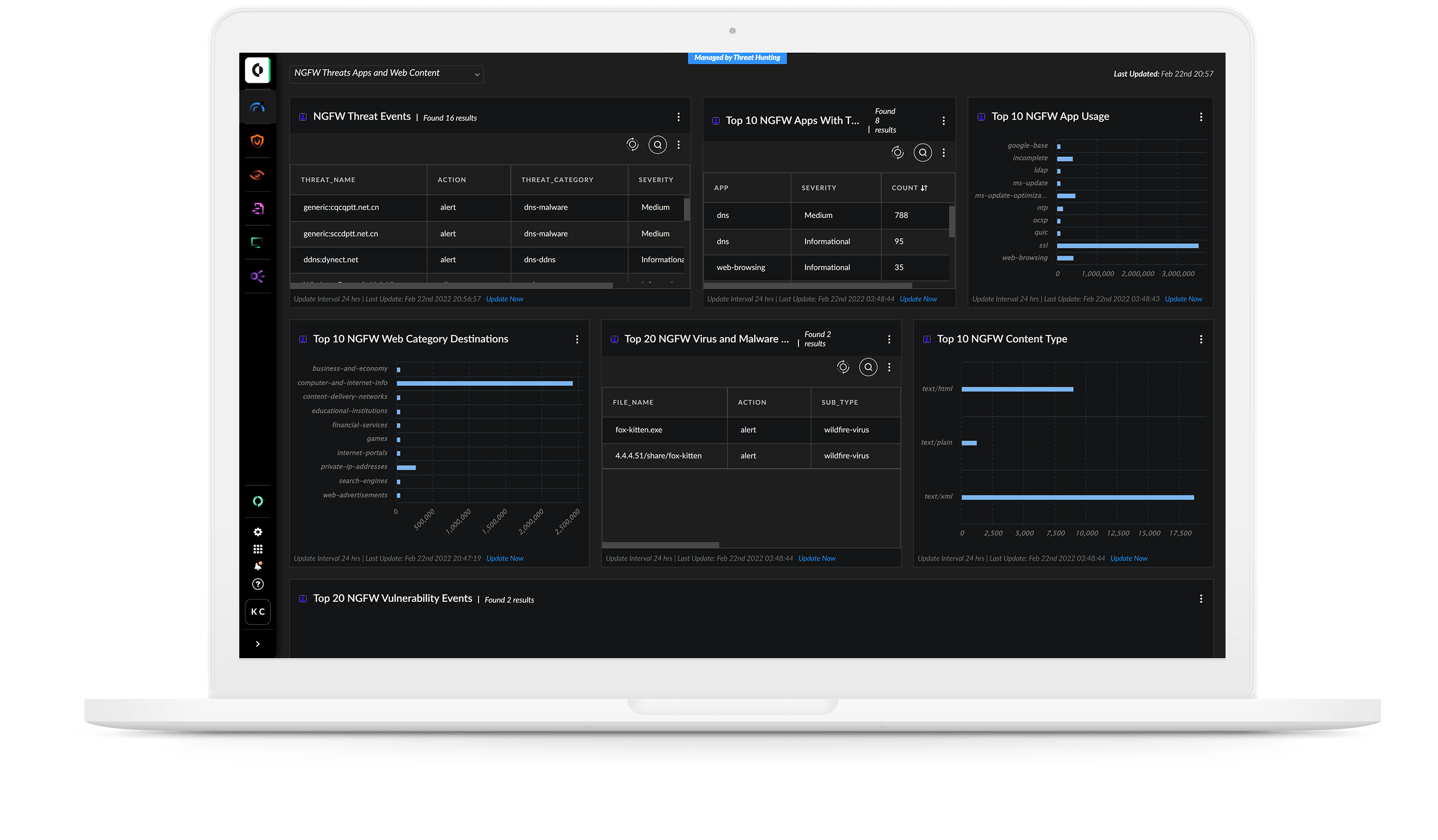
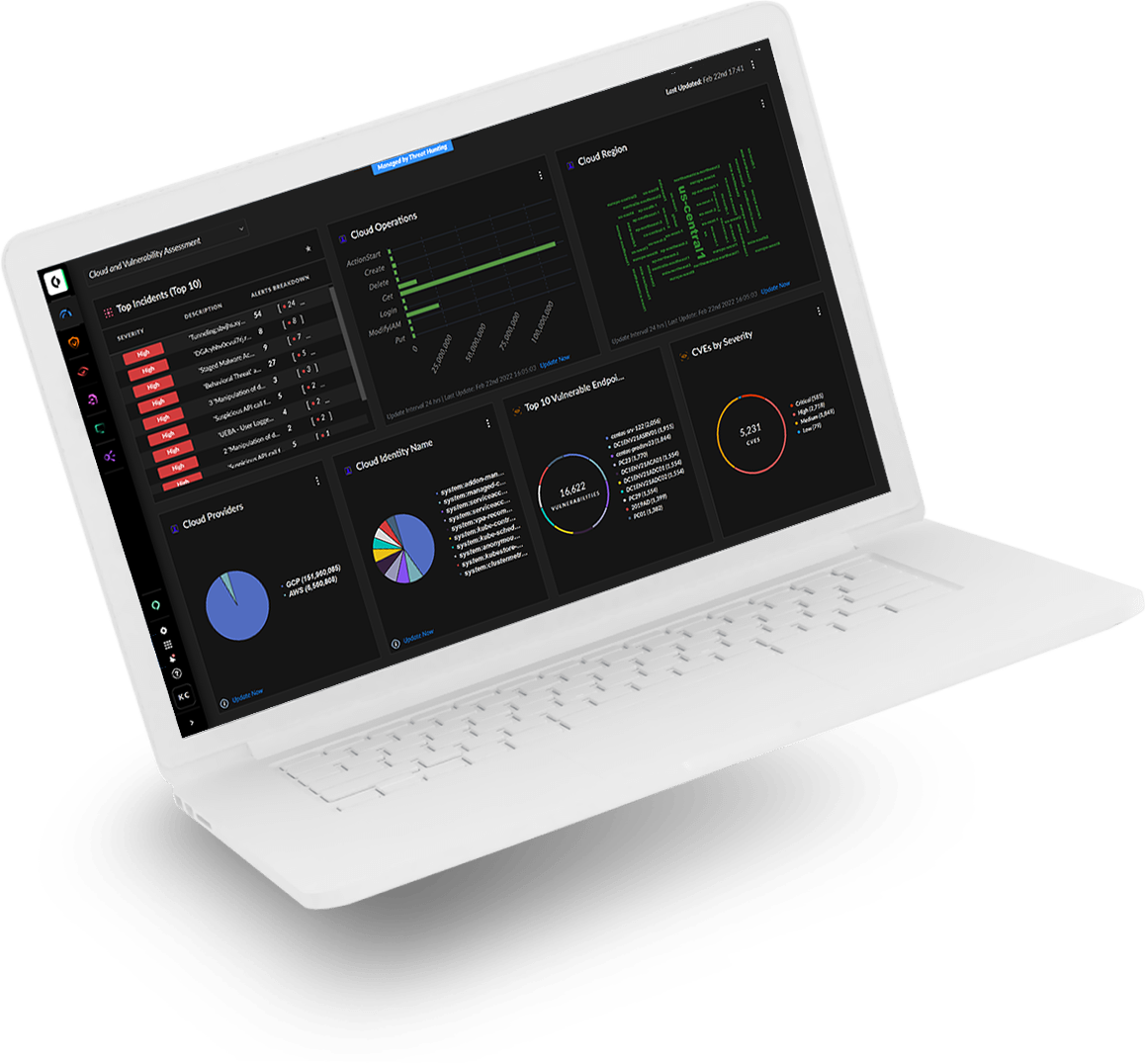
If you can’t see a threat, you can’t fight it. Detect attacks anywhere in your environment by applying analytics and machine learning to comprehensive data from across your organization. Behavior analytics identify anomalies and pinpoint stealthy and unknown threats with unmatched accuracy.
ML-driven analytics:
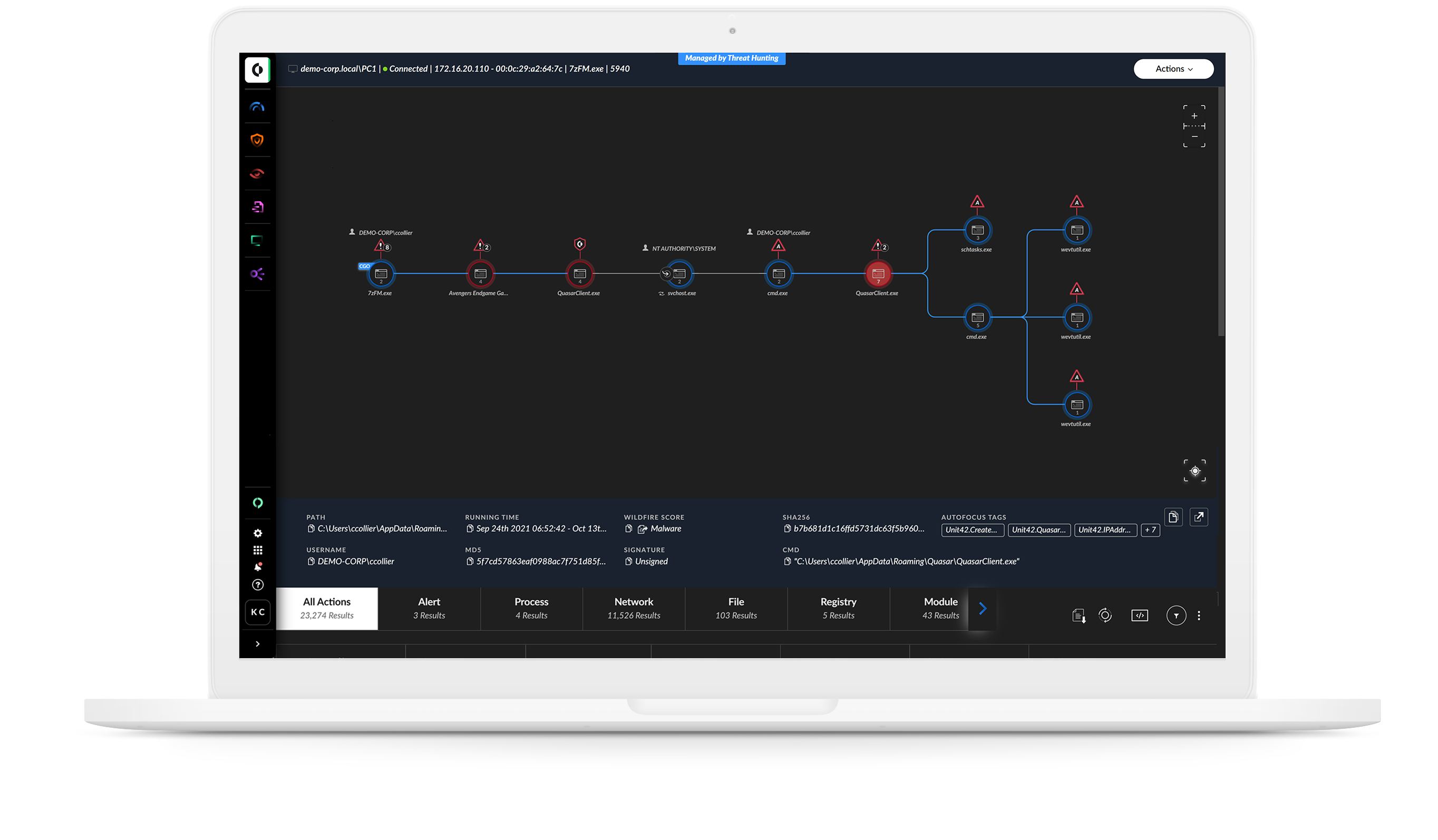
Detect malware, command and control, lateral movement and exfiltration by profiling behavior and spotting changes in behavior indicative of attack.
Out-of-the-box rules:
Instantly start detecting attacks with 400+ pre-defined rules. MITRE ATT&CK tags reveal attack techniques, while custom correlation rules offer advanced detection across data sources.