A gas station franchise discovered that a threat actor was modifying its point-of-sale (POS) credit card readers, harvesting bank details as customers swiped to pay. The retailer quickly identified the skimming device and called in Unit 42® to investigate. Using advanced forensic analysis, the expert team helped the client better understand the full nature and impact of the attack, enabling a more focused response.
An attack on credit—and credibility
A global gas station retailer with hundreds of pumps across hundreds of locations routinely ran thousands of card transactions each day. In the process of reviewing video surveillance at one store, a team member noticed an individual place a credit card skimmer on top of a card reader while the cashier was otherwise occupied. Location managers quickly pulled the POS device to stop fraudulent activity.
Company leaders realized that the incident posed a threat to both customer privacy and the company’s brand, trust, and reputation. Wanting to better understand the scope and potential repercussions of the incident, they called on the Palo Alto Networks Unit 42 Digital Forensics and Incident Response team.
Digital forensics experts build a custom device to analyze the skimmer
The client shipped the skimming device to Unit 42’s forensic lab, where an experienced team got to work dismantling it and examining every component. The digital forensics team noted a tamper-evident sticker on its outer surface, presumably taken from an authorized card reader—a tactic frequently used by threat actors to make fraudulent devices look legitimate.
A skimmer can hold information from up to 3,000 cards, but because the gas station staff identified and removed the device so quickly, it only affected a small number of their customers. To avoid notifying all customers—thereby causing undue panic and reputational damage—the retailer needed to understand which credit cards had been compromised. Unit 42 set out to extract the data captured by the device in order to discover: How many of all the cards scanned at this location were actually compromised by this credit card skimmer? How many customers were impacted? Which banks should be notified?To do that, Unit 42 constructed a custom device called a jig to connect with the wireless Bluetooth module built into the skimmer. The custom jig used spring-loaded pins that could reach the connection points in the Bluetooth module and access its functionality. Once it captured the module’s full configuration and data log, Unit 42 found evidence that an outside device had wirelessly connected to the module—likely the threat actor pulling card info.
To determine what data had been affected, Unit 42 carefully used hot air to melt away the storage chip’s soldering and extract its intel. The team examined the readable data, including primary credit card account numbers, account holder names, and expiration dates. They then compared this data with the dates and timestamps in the transaction log, matching those that occurred while the skimming device was at the retailer’s location.
HOW SKIMMERS WORK
Outside: PIN Pad Overlay
1. MAGNETIC STRIPE READER
Captures card data when swiped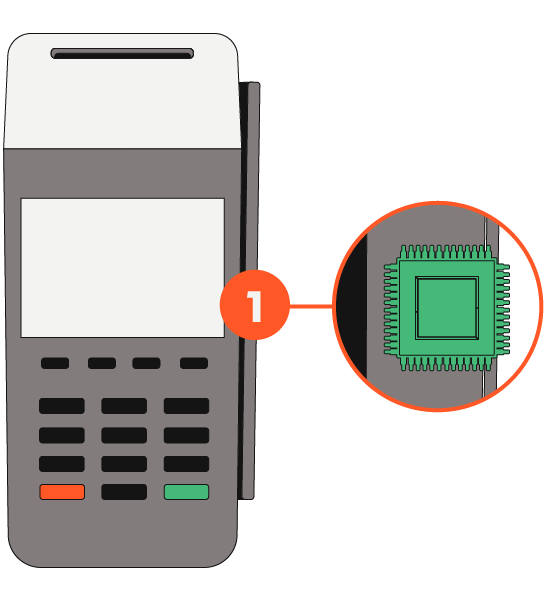
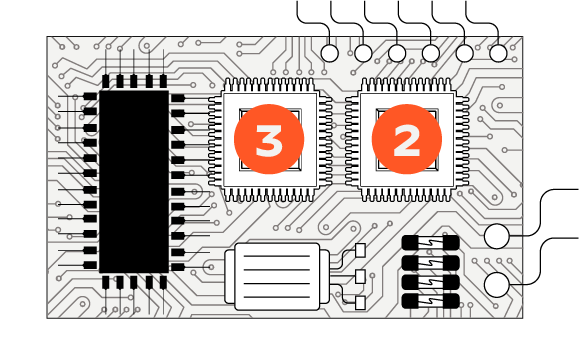
Inside: Main Circuit Board and Bluetooth Module
2. MICROCONTROLLER CHIP
Controls the main functions of the skimmer: Collecting card data from the stripe read-head, loading that information into the storage chip, and sending it out through the Bluetooth module
3. FLASH STORAGE CHIP
Can store over 3,000 credit card numbers
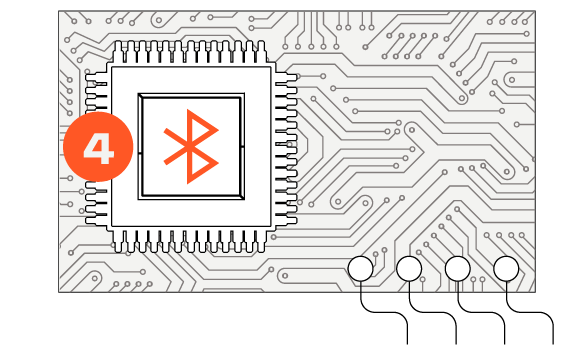
4. BLUETOOTH WIRELESS MODULE
Allows threat actors to wirelessly collect credit card data with a nearby Bluetooth device
Discoveries pave the way for a confident, future-ready response
Thanks to the limitations of POS skimmers and the quick-acting gas station staff, Unit 42 determined that data was only captured from a few dozen credit cards. Without the exact details uncovered from the digital forensics work, the company would have run the risk of disturbing the 3,000 customers whose cards were unaffected. The retailer was also rightly concerned that this type of attack might be repeated in the future and wanted to understand which tactics the attackers used and how to limit damage.
Working with Unit 42 delivered value for the client in three key areas:
- A defined incident scope: By determining when the attack happened and which cards were impacted, Unit 42 delivered forensic findings back to the client on the precise scope of the attack.
- Clarity on next steps: Armed with this information, the retailer was able to take appropriate action without setting off widespread alarm, which could have damaged their reputation. They notified the banks about the handful of customers affected, and the banks were then able to issue new credit cards and resolve the incident.
- Better preparedness for future incidents: By learning more about the attackers’ tactics—knowing what to check, what to prepare for, and how to respond—the retailer is now better equipped to reduce the possibility of future threats.
Ultimately, this incident response engagement gave the retailer more confidence in how to defend against skimmer attacks in the future and a trusted partner in Unit 42 that helped them deliver a resolution.
About Unit 42
Palo Alto Networks Unit 42® brings together world-renowned threat researchers, elite incident responders, and expert security consultants to create an intelligence-driven, response-ready organization that is passionate about helping you proactively manage cyber risk. Our team serves as your trusted adviser to help assess and test your security controls against the right threats, transform your security strategy with a threat-informed approach, and respond to incidents in record time so that you get back to business faster.
If you’d like to learn more about how Unit 42 can help your organization defend against and respond to severe cyberthreats, visit start.paloaltonetworks.com/contact-unit42.html to connect with a team member.
Under attack?
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team at start.paloaltonetworks.com/contact-unit42.html or call North America toll free: +1.866.486.4842 (+1.866.4.UNIT42), EMEA: +31.20.299.3130, UK: +44.20.3743.3660, APAC: +65.6983.8730, or Japan: +81.50.1790.0200.