Benefits
A Security Roadmap Designed For Your Organization
Have a vision for your security posture? Want insights into how that vision will enable cyber resilience and drive business growth? Or maybe you want to see how Palo Alto Networks fits into your current security environment.
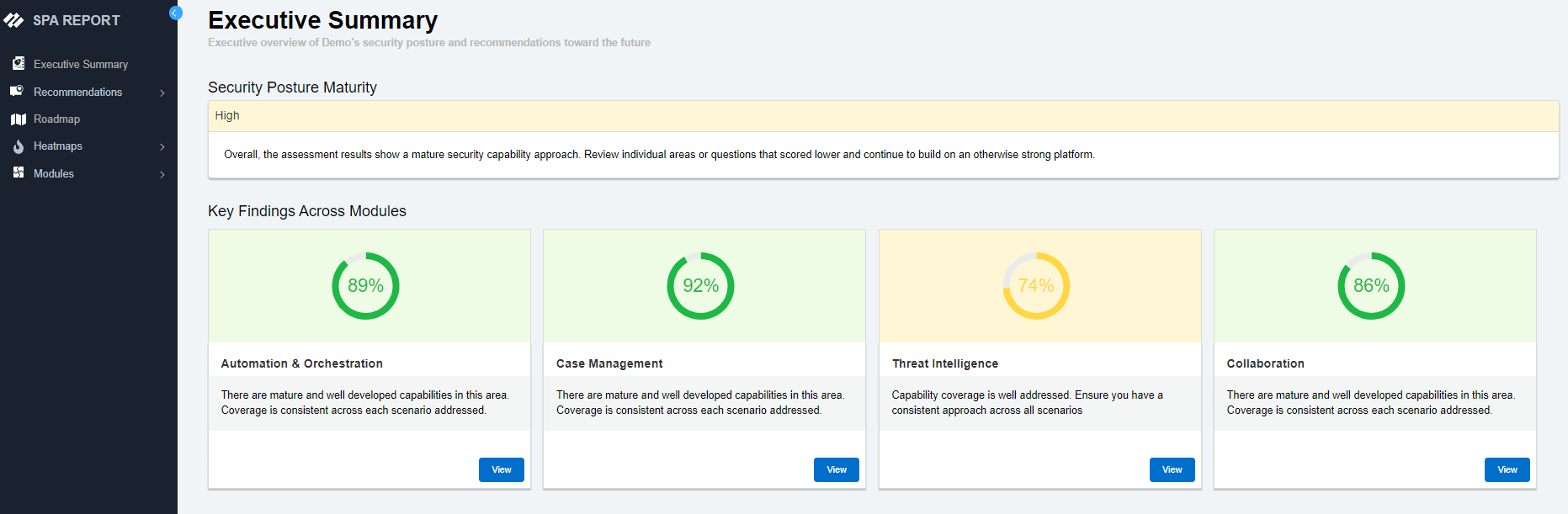
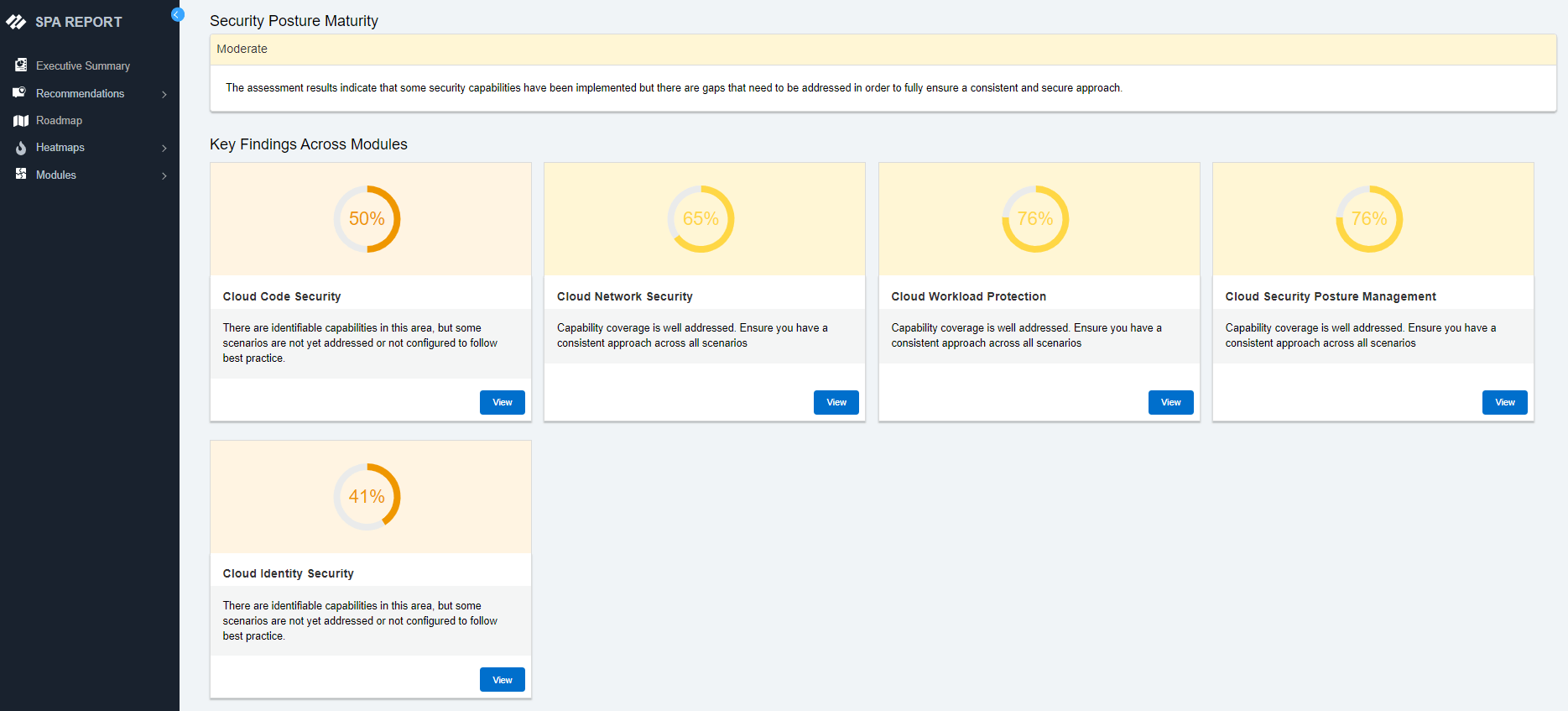
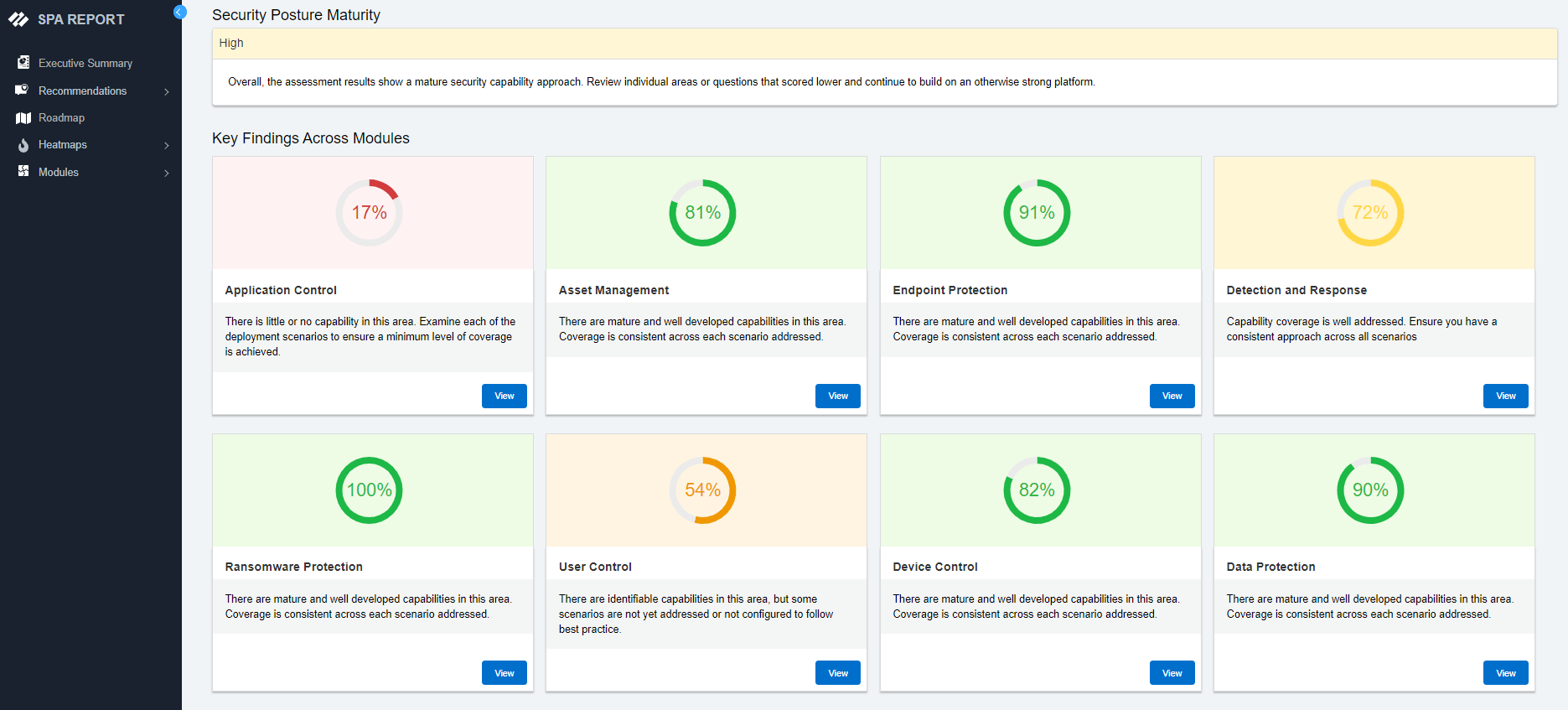
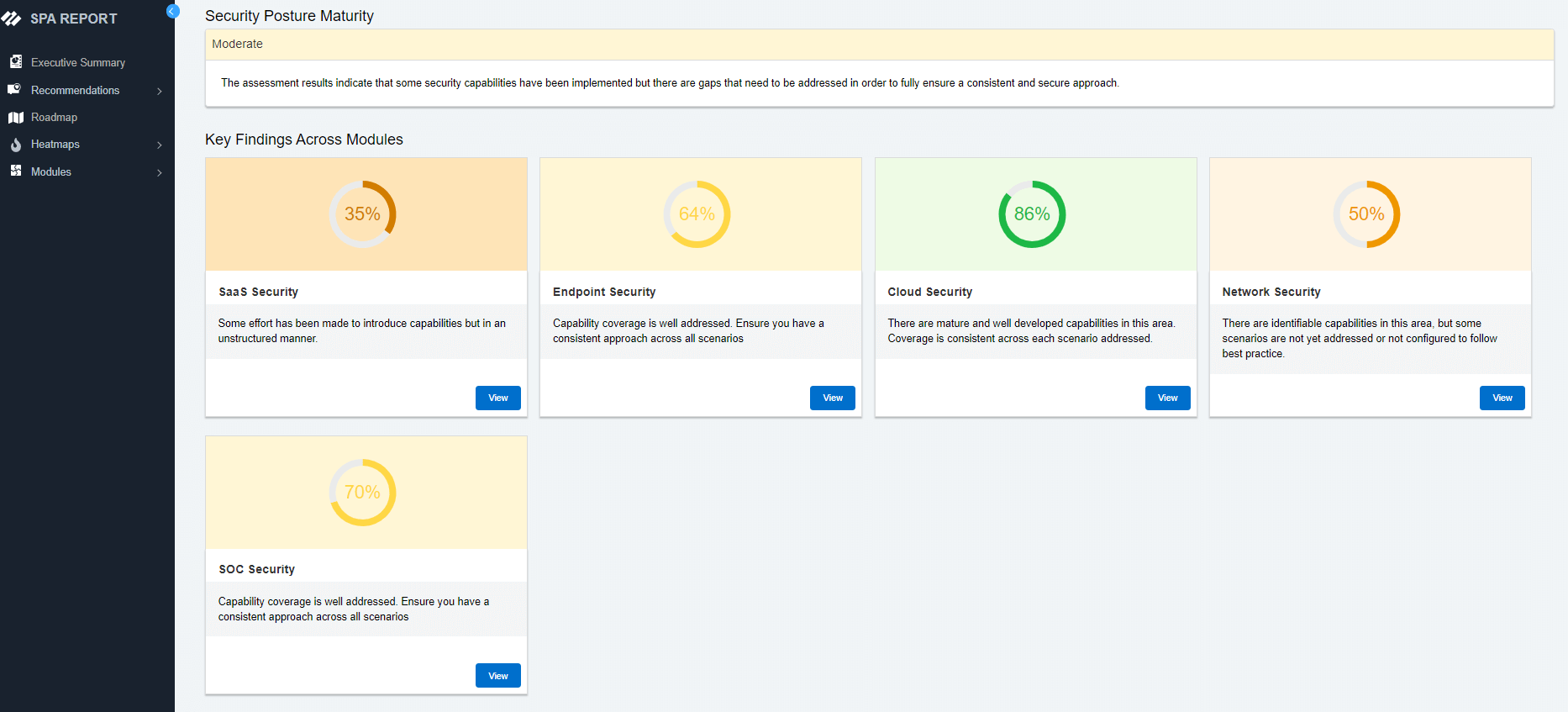
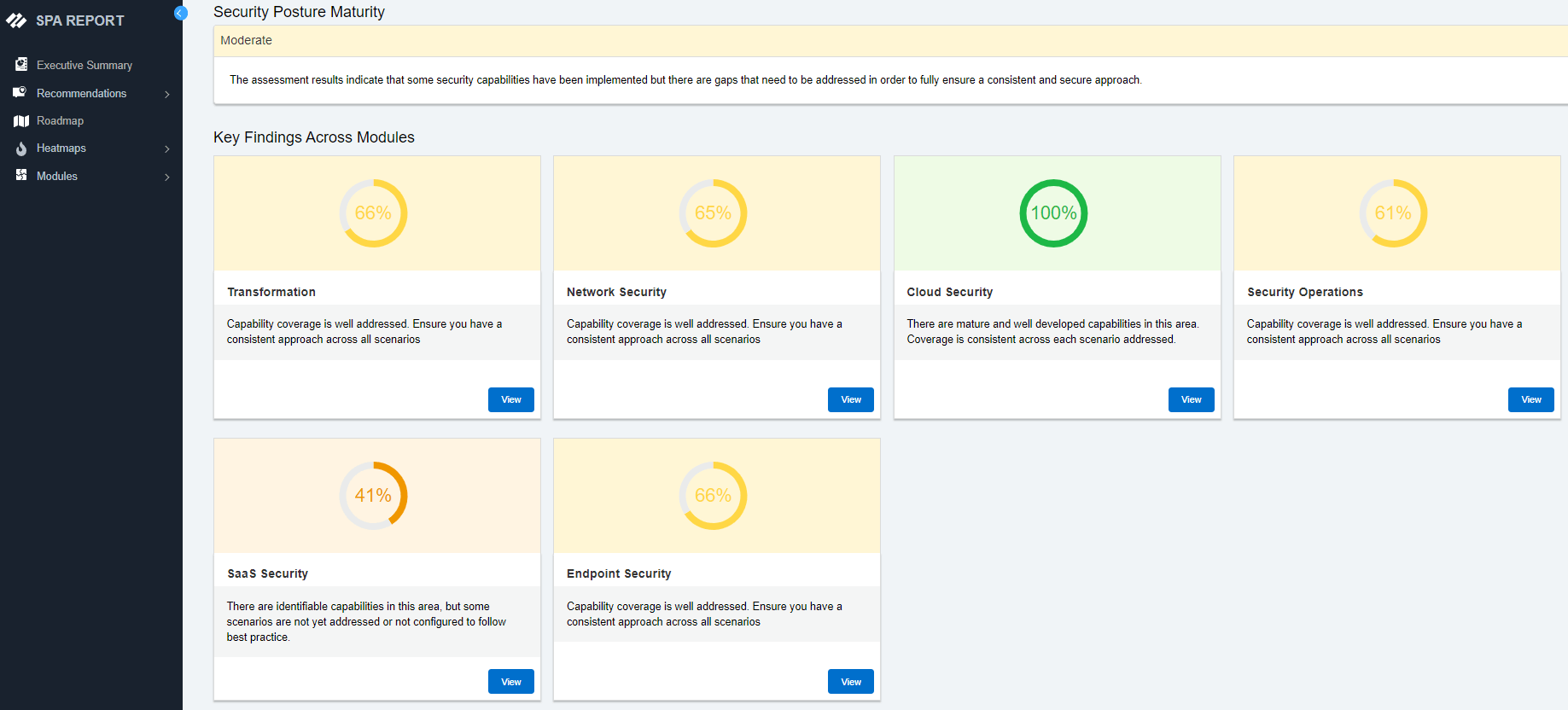
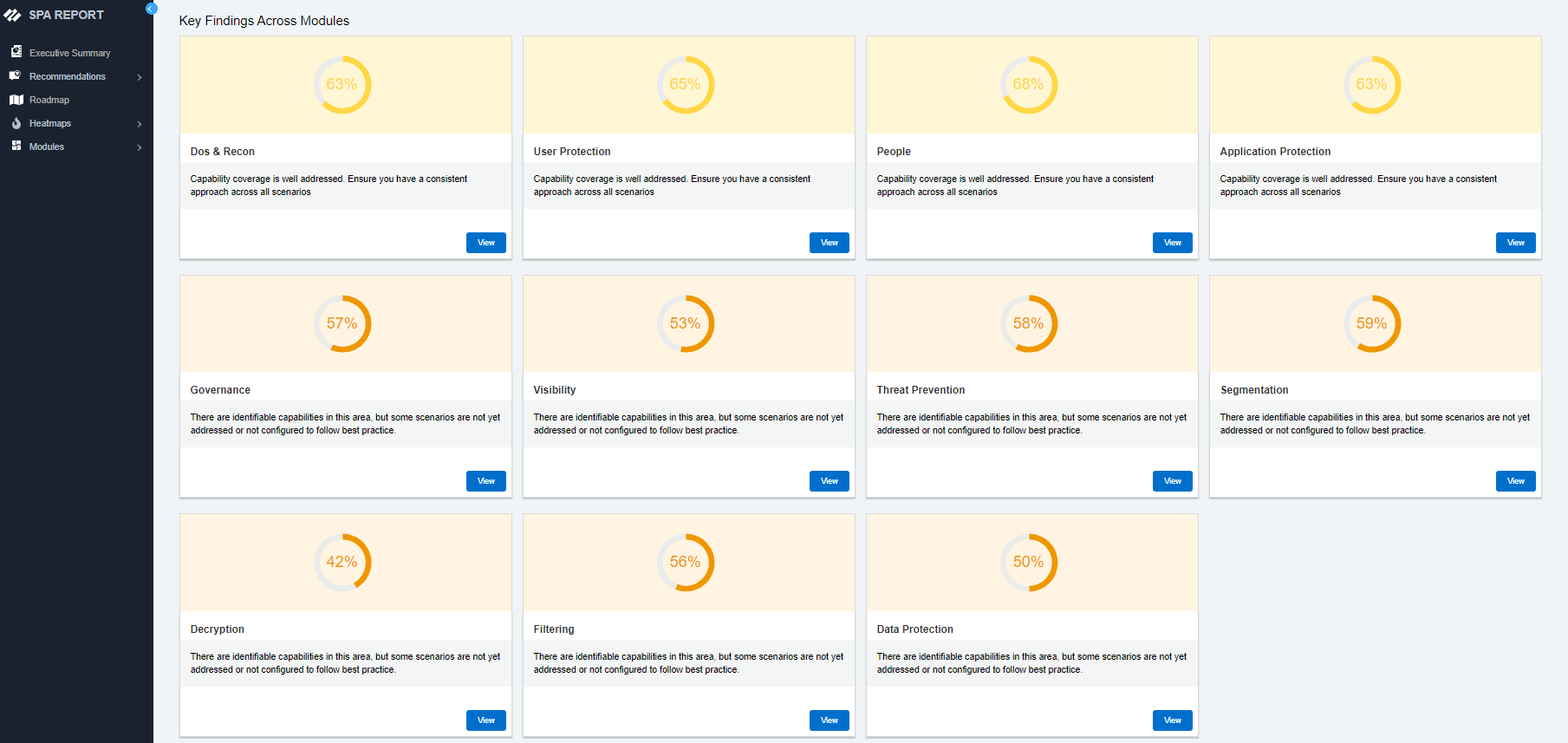
The Palo Alto Networks Security Posture Assessment (SPA) is designed to simplify your transformation journey, ensure a maximum return on investment, and supercharge cyber resilience. It analyzes your existing environment and provides a roadmap to your desired security outcome — entirely autonomously.
The Palo Alto Networks Security Posture Assessment (SPA) is designed to simplify your transformation journey, ensure a maximum return on investment, and supercharge cyber resilience. It analyzes your existing environment and provides a roadmap to your desired security outcome — entirely autonomously.
Choose your journey
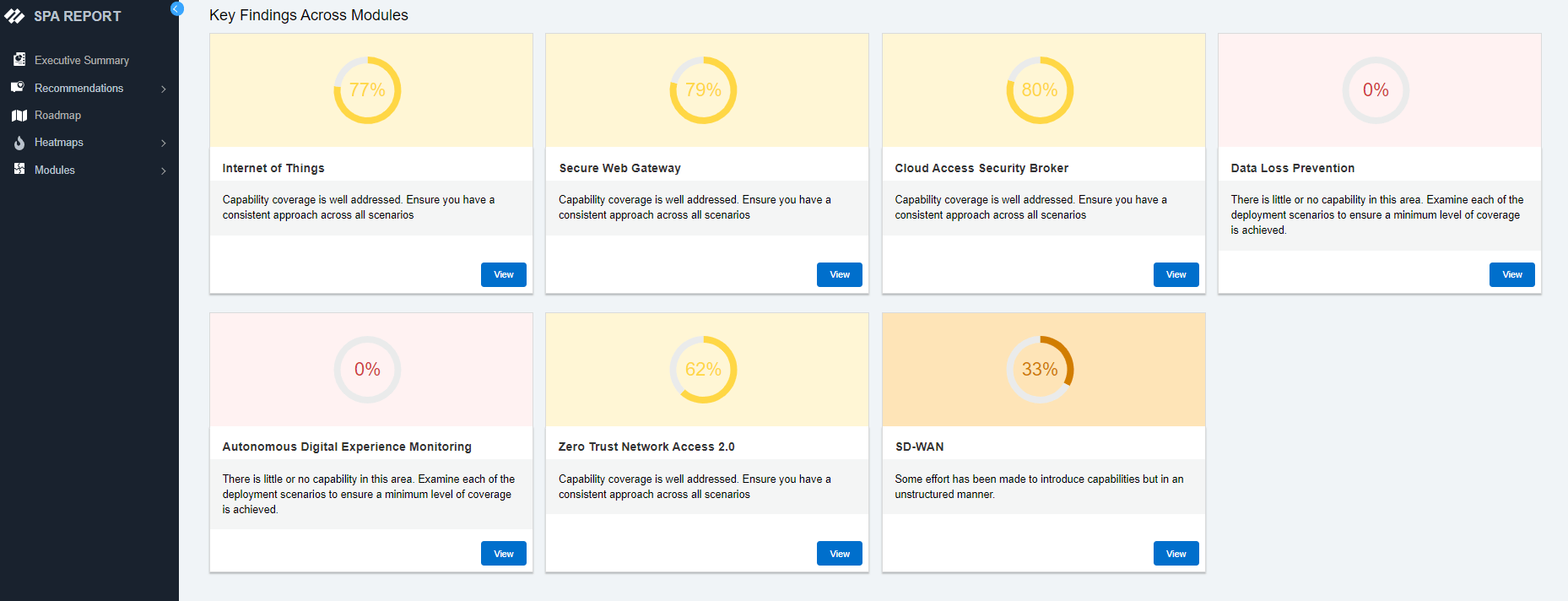
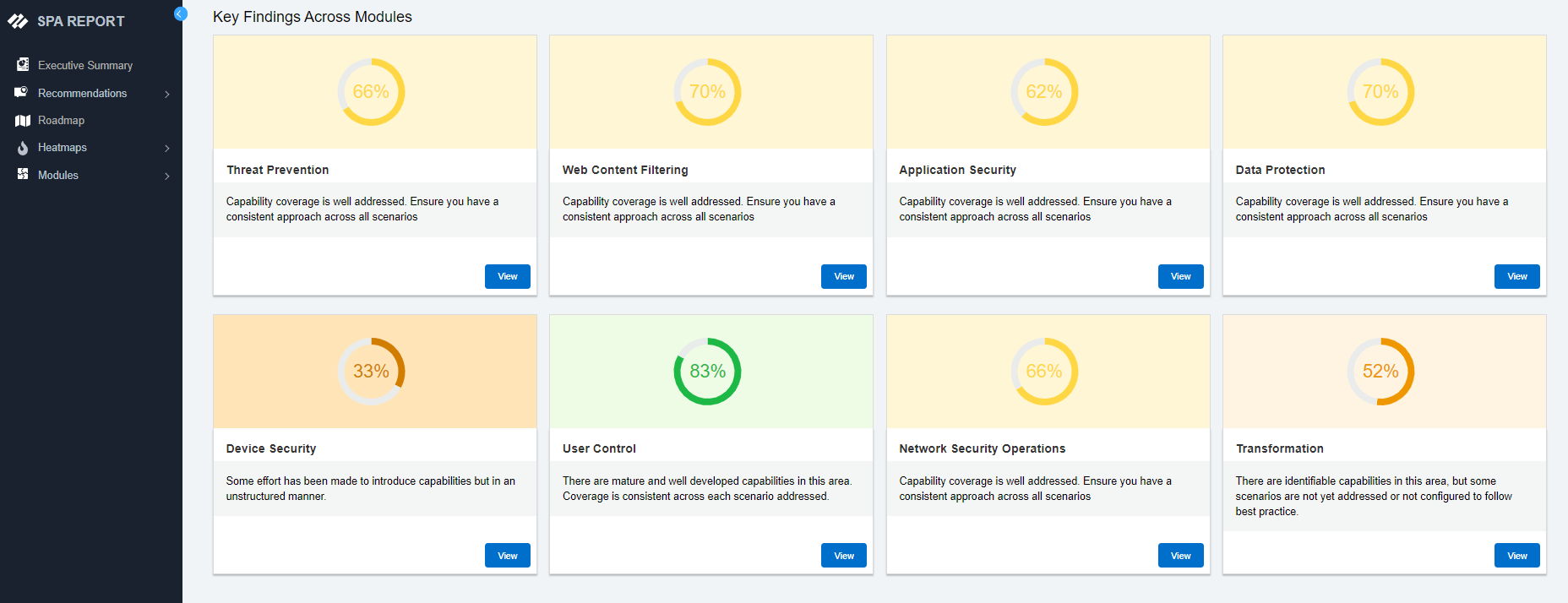
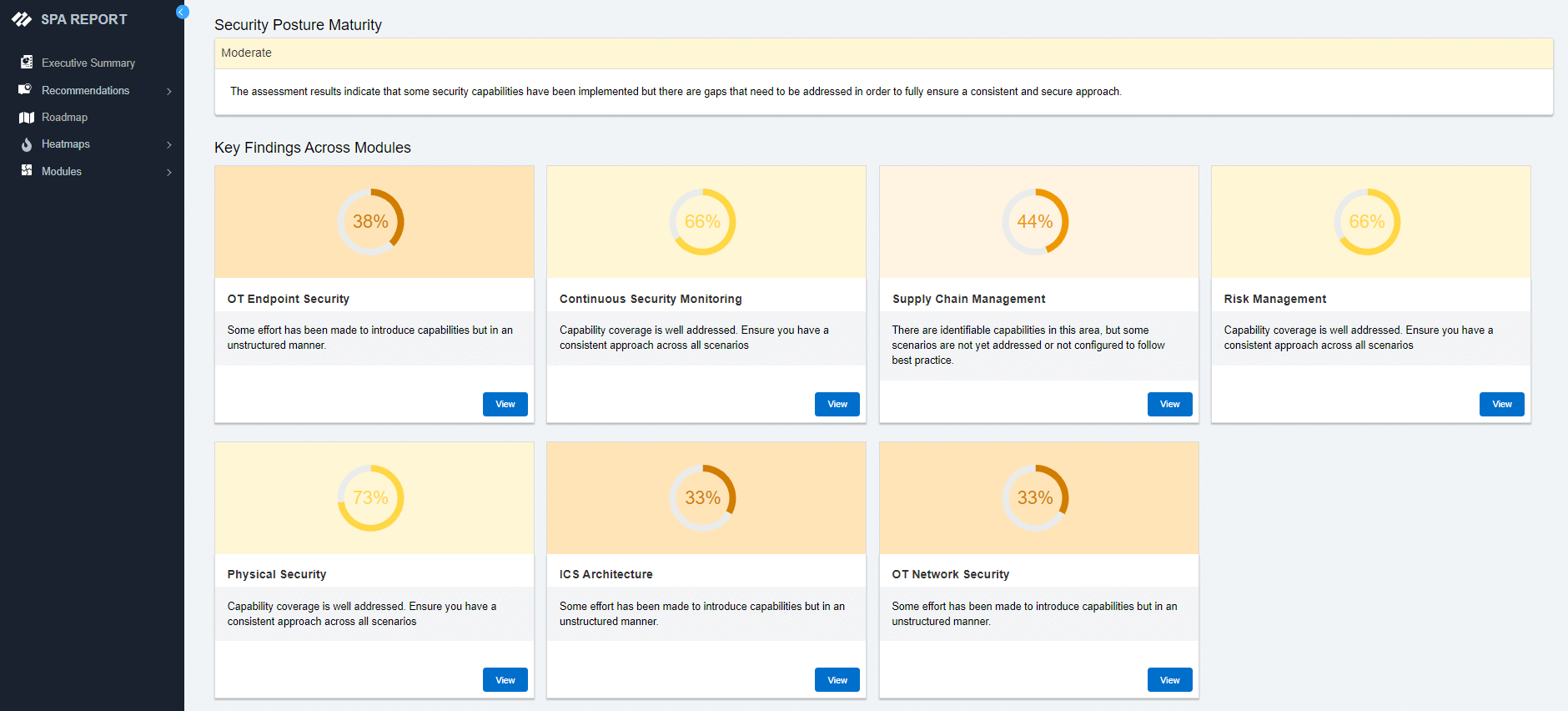
Choose from any of our security assessments based on your specific business needs. The SPA can contextualize even the most complex environments and generate audience-specific recommendations within minutes.
SASE / ZTNA 2.0 Deployments
Network Security Refresh / Improvement
SOC Modernization
Operational Technology (OT) Security
Cloud and Cloud Code Security
Endpoint Security Controls
Enterprise CyberSecurity - In-depth
Enterprise CyberSecurity - Concise
5G Capability and Readiness (Telco)