- 1. Understanding Indicators of Compromise
- 2. Why Are IoCs Important?
- 3. Types of IoCs
- 4. Examples of Indicators of Compromise
- 5. How do Indicators of Compromise (IoCs) Work?
- 6. How to Identify IoCs
- 7. Why Organizations Should Monitor for IoCs
- 8. IoC vs. IoA
- 9. The Role of AI and Machine Learning in IoC Detection
- 10. Enforcement Types for Indicators
- 11. Challenges in IoC Management
- 12. Best Practices for IoC Utilization
- 13. The IoC Lifecycle
- 14. Future Trends in IoC
- 15. Indicators of Compromise (IoCs) FAQs
- Understanding Indicators of Compromise
- Why Are IoCs Important?
- Types of IoCs
- Examples of Indicators of Compromise
- How do Indicators of Compromise (IoCs) Work?
- How to Identify IoCs
- Why Organizations Should Monitor for IoCs
- IoC vs. IoA
- The Role of AI and Machine Learning in IoC Detection
- Enforcement Types for Indicators
- Challenges in IoC Management
- Best Practices for IoC Utilization
- The IoC Lifecycle
- Future Trends in IoC
- Indicators of Compromise (IoCs) FAQs
What Are Indicators of Compromise (IoC)?
- Understanding Indicators of Compromise
- Why Are IoCs Important?
- Types of IoCs
- Examples of Indicators of Compromise
- How do Indicators of Compromise (IoCs) Work?
- How to Identify IoCs
- Why Organizations Should Monitor for IoCs
- IoC vs. IoA
- The Role of AI and Machine Learning in IoC Detection
- Enforcement Types for Indicators
- Challenges in IoC Management
- Best Practices for IoC Utilization
- The IoC Lifecycle
- Future Trends in IoC
- Indicators of Compromise (IoCs) FAQs
Indicators of compromise (IoC) are forensic artifacts found on a network or operating system that indicate a potential intrusion or breach. These data points—malicious IP addresses, unusual outbound network traffic, suspicious file hashes, and anomalous login attempts—help cybersecurity professionals identify, detect, and respond to security incidents. Effective use of IoCs is crucial for proactive defense and incident response.
Key Points
-
IoCs: Your Digital Breadcrumbs
IoCs are vital clues left by attackers that help you identify security breaches, detect malicious activity, and respond quickly to incidents. -
Faster Detection, Shorter Dwell Times
Using IoCs helps you find threats faster and reduces the time attackers spend in your system. For truly proactive security, combine IoCs with behavioral analytics and threat hunting. -
Types of IoCs and What to Monitor
IoCs fall into network, host, and email categories. Recognizing these, like suspicious IP addresses, file hashes, or unusual email patterns, helps you know what to watch out for. -
Integration is Key for Effective Detection
Knowing about IoCs isn't enough; you need to integrate them with your security tools like SIEM, EDR, and NDR, and use ongoing threat intelligence feeds for accurate detection. -
Managing IoCs Effectively
Good IoC management means reducing alert overload, keeping information up-to-date, and using continuous monitoring and automation to prevent problems. -
Dynamic IoC Management for Stronger Defense
IoC management is an ongoing process that requires overcoming operational challenges and adopting best practices for a resilient defense.
Understanding Indicators of Compromise
IoCs represent critical evidence of a security breach or ongoing malicious activity within an organization’s IT infrastructure. They are specific pieces of data—digital breadcrumbs—that an attacker leaves behind during an intrusion.
These aren't just abstract concepts; they are tangible signs, like a file’s unique signature (hash), a suspicious IP address communicating with internal systems, or an unusual pattern of data access. Identifying these indicators allows security teams to detect breaches that might otherwise go unnoticed, often before significant damage occurs.
IoCs are vital for proactive defense and swift incident response. They serve as early warning signals, enabling organizations to transition from reactive security measures to a more proactive posture. By understanding and actively monitoring for these indicators, cybersecurity professionals can significantly reduce the dwell time of an attacker within their network, limit the scope of a breach, and bolster their overall security posture.
Without effective IoC utilization, detecting sophisticated attacks becomes substantially more challenging, leaving enterprises vulnerable to prolonged compromise and severe consequences.
Why Are IoCs Important?
Accelerating Incident Response
IoCs enable security teams to quickly identify and respond to threats by providing specific artifacts to search for across systems. When analysts have concrete indicators, such as file hashes or IP addresses, they can rapidly determine the scope of an incident and initiate containment efforts within hours, rather than days or weeks.
Proactive Threat Detection
Organizations can feed IoCs into security tools, such as SIEM systems, intrusion detection systems, and threat intelligence platforms, to automatically scan for known malicious indicators. This enables the detection of threats before they cause damage, shifting from reactive cleanup to proactive blocking.
Enhancing Security Posture
Regular IoC analysis enables organizations to understand their threat landscape, identify security gaps, and enhance their defenses. By tracking which indicators appear in their environment, security teams can adjust controls, update policies, and improve monitoring capabilities.
Strategic Value for Cybersecurity Leaders
IoCs provide measurable data for risk assessment, compliance reporting, and security investment decisions. They enable leaders to demonstrate the effectiveness of their security programs, justify budget allocations, and communicate threat trends to executive stakeholders and board members.
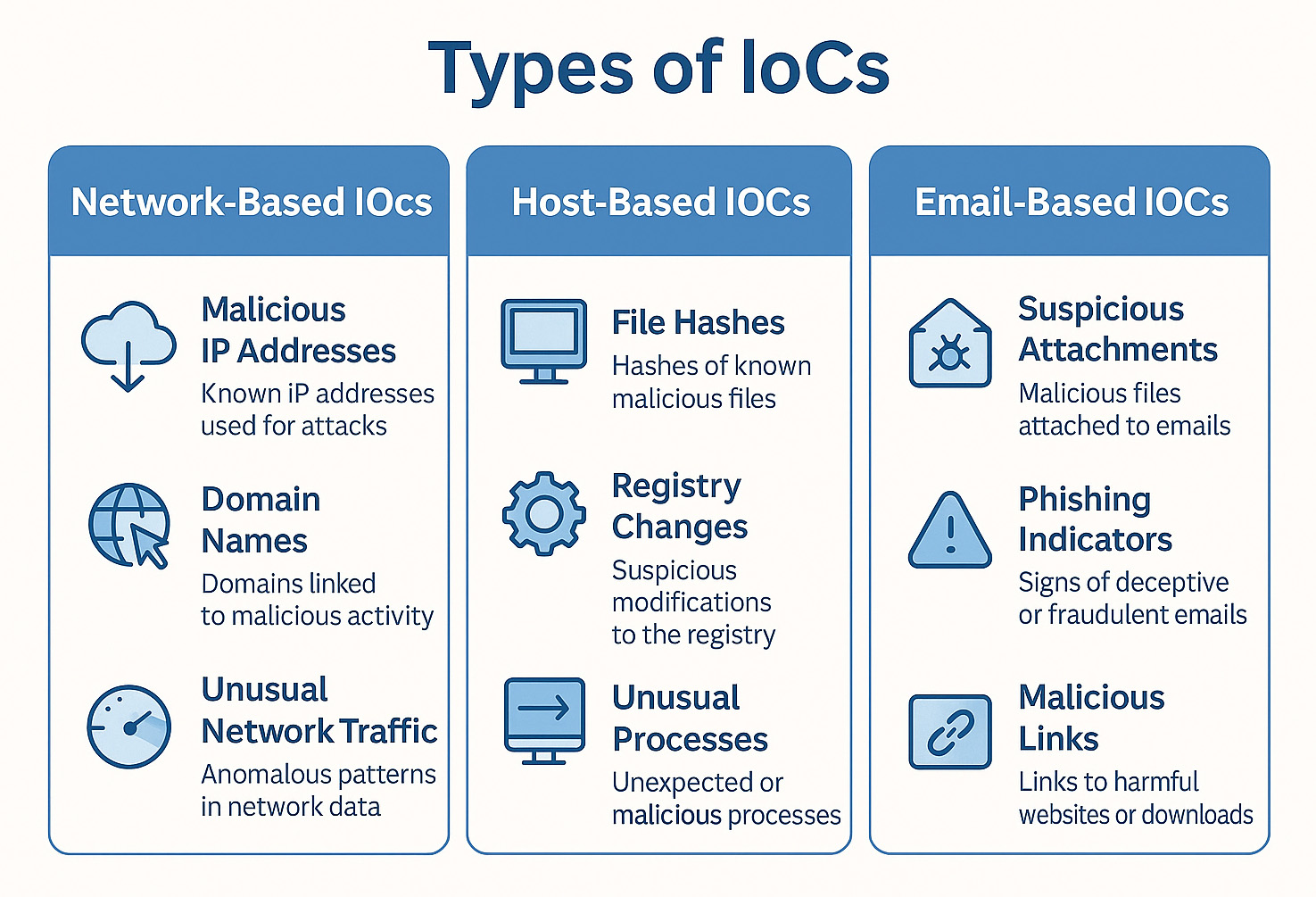
Figure 1: Types of IoCs Comparison
Types of IoCs
Network-Based IoCs
Network-based indicators concentrate on suspicious network communications and traffic patterns that imply a compromise or malicious activity.
Malicious IP Addresses
Known malicious IP addresses are linked to malware command and control servers, phishing sites, or attack infrastructure. These addresses are frequently shared through threat intelligence feeds and blacklists.
Unusual DNS Queries
Abnormal domain name resolution requests include queries to recently registered domains, algorithmically generated domain names, or domains with suspicious patterns that may indicate malware communication.
Command and Control (C2) Traffic
Regular beaconing patterns, encrypted channels, or connections to known malicious infrastructure are characteristic of network communications between compromised systems and attacker-controlled servers.
Anomalous Network Traffic Patterns
Traffic anomalies include atypical data transfers, such as substantial uploads during non-peak hours, connections to unexpected geographic areas, and traffic levels that significantly deviate from established baselines.
Host-Based IoCs
The following indicators focus on suspicious activities and artifacts found directly on endpoint devices, servers, and workstations that suggest system compromise.
File Hashes
Unique cryptographic fingerprints (MD5, SHA-1, SHA-256) serve to identify specific malicious files. Security tools utilize these hashes by comparing them against threat intelligence databases. This process enables the swift detection of known malware, regardless of whether the files have been renamed or moved.
Registry Key Changes
Changes to Windows registry entries can signify malicious activity. These modifications may include the creation of new startup programs, alterations to security settings, or the establishment of persistence mechanisms. Attackers frequently manipulate registry keys to maintain access to systems or to disable security features.
Unusual Process Activity
Be alert for abnormal running processes, such as:
- Unknown executables
- Processes running from suspicious locations (e.g., temporary folders)
- Elevated privilege escalation
- Legitimate processes are used maliciously via techniques like process hollowing or DLL injection.
Modified System Files
Changes to critical operating system files, configuration files, or system binaries can be indicators of malicious activity. This encompasses unauthorized alterations to system utilities, drivers, or fundamental OS components, which attackers may exploit for persistence or to elevate their privileges.
Account Logins and Privileges
Be alert for the following authentication-related events that may indicate malicious activity:
- Failed Login Attempts: An unusually high number of failed logins for a single account could suggest a brute-force attack.
- Unusual Login Activity: Look for logins occurring at times or from geographic locations that are not typical for the user.
- Privilege Escalations: Be suspicious of accounts gaining higher levels of access than they normally possess.
- New User Accounts: Investigate newly created accounts, especially if they appear suddenly or without proper authorization.
- Anomalous Resource Access: Monitor for accounts accessing resources that fall outside their regular scope of duties or historical access patterns.
Email-Based IoCs
These IoCs are associated with malicious email activities, including phishing attacks and threats delivered via email, targeting organizational messaging systems.
Malicious Email Addresses
Malicious email addresses are sender addresses linked to phishing, spam, or social engineering. They might involve:
- Spoofed legitimate domains
- Suspicious new domains
- Addresses from known malicious sources
Suspicious Attachments and Links
Email attachments can include potentially dangerous file types such as executables, macros, and scripts. Similarly, URLs embedded in emails may lead to malicious websites, exploit kits, or credential harvesting pages. Modern attack methods frequently involve the use of document macros or weaponized PDF files.
Email Header Anomalies
Unusual email metadata patterns can indicate malicious activity. These anomalies include:
- Spoofed sender information
- Suspicious routing paths
- Missing email authentication records (SPF, DKIM, DMARC)
- Headers suggesting the use of automated or bulk sending tools are often associated with spam campaigns.
Examples of Indicators of Compromise
The following are examples of specific indicators of compromise across different categories:
IoC Type |
Example |
Description |
File Hash |
SHA-256 hash "a1b2c3d4e5f6..." associated with the Emotet banking trojan. |
Security teams can search for this exact hash across all systems to identify infected machines, even if the malware file is renamed or hidden. |
IP Address |
Traffic to 198.51.100.42, a known command and control server for APT29 campaigns. |
Any internal system communicating with this IP indicates potential compromise and active data exfiltration. |
Domain |
DNS queries to "update-security-ms[.]com" - a typosquatted domain mimicking Microsoft. |
Delivers malware payloads through fake security updates. |
Registry Entry |
New entry at "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" pointing to an executable in %TEMP%. |
Indicates a malware persistence mechanism. |
Email Address |
Sender address "security@micr0soft[.]net" with zero replacing 'o' in a phishing campaign targeting Office 365 credentials. |
Used in phishing campaigns targeting Office 365 credentials. |
Real-World Scenarios
Ransomware Campaign: Multiple systems showing the same file hash for ransomware executable, followed by mass file encryption activity and ransom note creation. Network traffic reveals communication with a known ransomware payment infrastructure.
APT Intrusion: Initial compromise through spear-phishing email containing a weaponized Word document. Subsequent IoCs include PowerShell execution, lateral movement via SMB, and regular beaconing to attacker-controlled domains over encrypted channels.
Insider Threat: Unusual after-hours database access by privileged user account, followed by large data exports to external cloud storage services not typically used by the organization.
Supply Chain Attack: Legitimate software update containing malicious code, identified by unexpected file hash changes in trusted applications and subsequent network connections to suspicious infrastructure.
Common IoC Patterns
Beaconing Activity: Regular, automated network connections at fixed intervals (every 30 minutes) to external servers, indicating malware check-ins with command and control infrastructure.
Living-off-the-Land: The abuse of legitimate system tools, such as PowerShell, WMI, or PsExec, for malicious purposes, creating process execution patterns that deviate from normal administrative activities.
Persistence Mechanisms: Consistent patterns of registry modifications, scheduled task creation, or service installations that allow malware to survive system reboots and maintain access.
Data Staging: The creation of large volumes of compressed files in temporary directories, often followed by network transfers, indicates preparation for data exfiltration.
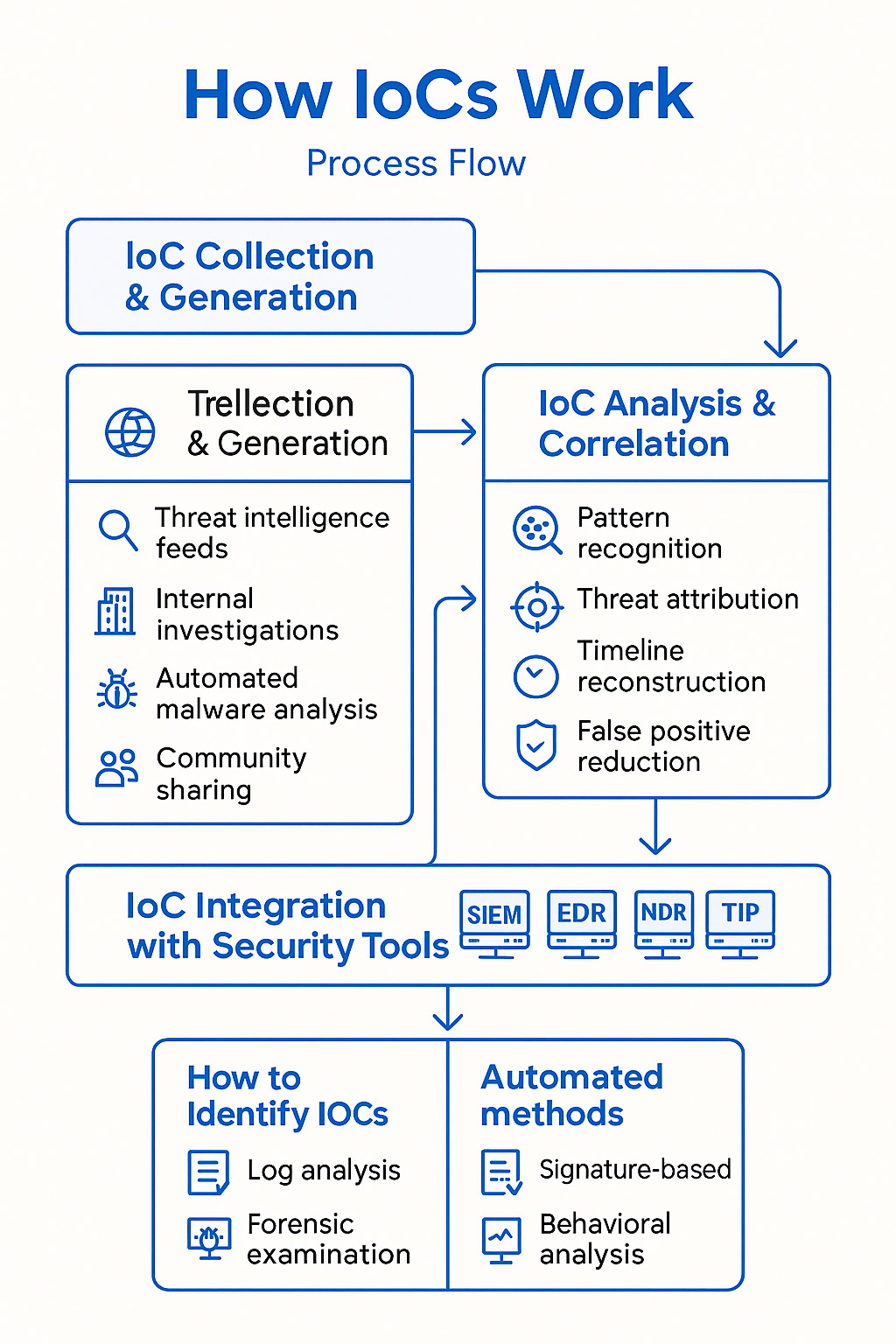
Figure 2: How IoCs Work
How do Indicators of Compromise (IoCs) Work?
IoCs are generated and collected through various sources, forming the foundation for threat detection and incident response efforts. These sources provide a continuous stream of information about known malicious activities and artifacts.
Threat Intelligence Feeds: Organizations subscribe to commercial and open-source threat intelligence services that provide continuously updated IoC databases. Sources include government agencies (US-CERT, CISA), security vendors (CrowdStrike, FireEye), and community platforms (MISP, AlienVault OTX).
Internal Incident Response: Security teams extract IoCs during breach investigations by analyzing compromised systems, malware samples, and attack artifacts. Forensic tools, such as Volatility, YARA rules, and sandbox environments, aid in identifying unique indicators from actual incidents.
Automated Malware Analysis: Sandboxes and dynamic analysis platforms automatically generate IoCs by executing suspicious files in controlled environments, capturing network communications, file modifications, and behavioral patterns.
Community Sharing: Security researchers and organizations share IoCs through industry groups, information sharing organizations (ISAOs), and collaborative platforms to collectively defend against common threats.
IoC Analysis and Correlation
IoC analysis and correlation involve pattern recognition, threat attribution, timeline reconstruction, and the reduction of false positives.
Pattern Recognition: Security analysts examine multiple IoCs to identify relationships and patterns of attack. For example, correlating specific file hashes with particular IP addresses and domain names to map complete attack campaigns.
Threat Attribution: Analysts compare IoC clusters against known threat actor profiles to determine likely attribution. Similar tools, techniques, and infrastructure often link attacks to specific Advanced Persistent Threat (APT) groups or cybercriminal organizations.
Timeline Reconstruction: IoCs help establish attack timelines by correlating timestamps from logs, file creation dates, and network activity to understand the sequence of malicious events.
False Positive Reduction: Analysts validate IoCs against legitimate business activities and known good indicators to reduce false alerts and improve detection accuracy.
IoC Integration with Security Tools
Integrating IoCs with various security tools enhances threat detection and response capabilities.
SIEM Integration: Security Information and Event Management systems ingest IoC feeds and automatically search historical logs for matches. This enables retroactive threat hunting and identifies previously undetected compromises.
Endpoint Detection Response (EDR): EDR platforms continuously monitor endpoints for IoC matches in real-time, automatically blocking or quarantining suspicious files, processes, and network connections.
Network Security Tools: Firewalls, intrusion prevention systems, and DNS security solutions use IoC feeds to block malicious IP addresses, domains, and URLs at the network perimeter.
Threat Intelligence Platforms (TIP): Centralized systems aggregate, normalize, and distribute IoCs across security tools, providing automated feeds and API integrations for consistent threat data management.
How to Identify IoCs
Identifying IoCs is a critical aspect of cybersecurity, involving both manual investigation and automated detection methods.
Manual Investigation Techniques
Log Analysis: Security analysts manually review system logs, network logs, and application logs to identify suspicious patterns and anomalies. This includes examining Windows Event Logs, firewall logs, and web server access logs for anomalies like failed authentication attempts or unusual file access.
Forensic Examination: Deep-dive analysis of compromised systems using tools like Autopsy, FTK, or Volatility to examine memory dumps, disk images, and file system artifacts. Analysts look for hidden files, registry modifications, and remnants of malicious activity.
Network Traffic Analysis: Manual packet capture analysis using Wireshark or tcpdump to examine network communications, identify suspicious protocols, and trace data exfiltration attempts or command and control communications.
Threat Hunting: Proactive searching through enterprise environments using hypotheses about potential threats. Hunters use custom queries, behavioral analysis, and attack technique frameworks (MITRE ATT&CK) to discover hidden threats.
Automated Detection Methods
Signature-Based Detection: Antivirus and security tools automatically scan for known malicious file hashes, malware signatures, and attack patterns stored in threat databases, providing immediate identification of known threats.
Behavioral Analysis: Machine learning algorithms analyze system and network behavior to identify deviations from established baselines, detecting previously unknown threats through anomalous activity patterns.
Heuristic Analysis: Security tools use rule-based logic to identify potentially malicious activities based on suspicious combinations of actions, such as file encryption followed by network communications to external servers.
Automated IoC Matching: Security platforms continuously compare observed activities against threat intelligence feeds, automatically flagging matches and generating alerts for the security team investigation.
Security Information and Event Management (SIEM)
Centralized Log Aggregation: SIEM systems collect and normalize logs from across the enterprise infrastructure, creating a unified view of security events and enabling correlation across multiple data sources.
Real-Time Correlation: Advanced correlation engines analyze incoming events in real-time, identifying patterns that match known attack signatures or indicate potential compromise across multiple systems simultaneously.
Custom Detection Rules: Security teams create organization-specific rules and use cases that trigger alerts when certain IoC combinations are detected, enabling tailored threat detection for their unique environment.
Historical Analysis: SIEM platforms store months or years of security data, enabling analysts to conduct retroactive searches for IoCs identified in recent threat intelligence updates.
Endpoint Detection and Response (EDR): EDR provides deep visibility into endpoint activity, detecting and responding to IoCs at the individual device level by monitoring, analyzing, and enabling rapid action on suspicious behaviors and threats.
Continuous Endpoint Monitoring: EDR agents deployed on workstations and servers continuously monitor file system changes, process execution, network connections, and registry modifications in real-time.
Behavioral Monitoring: EDR solutions track process relationships and execution chains to identify suspicious activities, such as process injection, privilege escalation, or lateral movement attempts.
Threat Hunting Capabilities: EDR platforms offer advanced search capabilities, enabling security teams to hunt for specific IoCs across all managed endpoints using custom queries and investigative tools.
Automated Response: EDR systems can automatically isolate compromised endpoints, kill malicious processes, and quarantine suspicious files when IoCs are detected.
Network Detection and Response (NDR)
Network Traffic Analysis: NDR solutions monitor all network communications using deep packet inspection, flow analysis, and metadata extraction to identify malicious network-based IoCs.
East-West Traffic Monitoring: Unlike perimeter security tools, NDR monitors internal network traffic to detect lateral movement, command and control communications, and data exfiltration attempts.
Machine Learning Detection: Advanced NDR platforms use artificial intelligence to establish network behavior baselines and identify anomalous communications patterns that may indicate compromise.
Protocol Analysis: NDR tools analyze application-layer protocols to detect hidden tunnels, encrypted malware communications, and the abuse of legitimate protocols for malicious purposes.
Threat Intelligence Platforms
IoC Feed Management: TIP solutions aggregate threat intelligence from multiple sources, normalize data formats, and automatically distribute relevant IoCs to integrated security tools.
Contextual Enrichment: Platforms provide additional context for IoCs, including threat actor attribution, campaign information, and confidence scores to help analysts prioritize investigations.
Custom Intelligence Creation: Organizations can create and share custom IoCs derived from their incident response activities, building institutional knowledge and improving detection capabilities.
API Integration: TIPs provide APIs that enable automated sharing of IoCs with security tools, ensuring consistent and timely distribution of threat intelligence across the security infrastructure.
Why Organizations Should Monitor for IoCs
Monitoring for IoCs offers several critical benefits for organizations, significantly enhancing their security posture and reducing the impact of cyber threats. This section will delve into the key advantages of proactively monitoring IoCs.
Reducing Dwell Time
Faster Detection: IoC monitoring enables organizations to detect breaches within days or weeks rather than the industry average of 277 days. Automated systems continuously scan for known indicators, immediately alerting security teams when threats are identified.
Accelerated Investigation: Pre-established IoCs provide security analysts with specific artifacts to search for, dramatically reducing the time needed to determine breach scope and identify affected systems from months to hours.
Rapid Containment: Early IoC detection allows security teams to quickly isolate compromised systems, block malicious network traffic, and prevent attackers from establishing persistence or moving laterally through the network.
Cost Reduction: Studies show that breaches detected within 200 days cost $1.12 million less than those taking longer to identify. Reduced dwell time directly correlates with lower incident response costs and business impact.
Minimizing Breach Impact
Proactive monitoring of IoCs minimizes the impact of security breaches by enabling early detection and rapid response to threats.
Data Loss Prevention: Early IoC detection helps prevent large-scale data exfiltration by identifying suspicious network activity before attackers can steal sensitive information or intellectual property.
System Damage Limitation: Monitoring for ransomware IoCs enables organizations to stop encryption processes before entire network shares are compromised, potentially saving thousands of files and systems.
Reputation Protection: Faster breach detection and response help organizations avoid prolonged compromises that result in public disclosure, regulatory scrutiny, and long-term reputational damage.
Business Continuity: Quick IoC identification enables targeted response actions that minimize operational disruption compared to the broad network shutdowns required for advanced persistent threats (APTs).
Improving Threat Hunting Capabilities
IoCs are vital forensic artifacts that signal potential security intrusions. Monitoring IoCs is crucial for proactive defense, faster incident response, and understanding threat landscapes, ultimately enhancing an organization's overall security posture and compliance efforts.
Proactive Defense: IoC monitoring enables security teams to shift from reactive incident response to proactive threat hunting, allowing them to search for advanced threats before they cause damage.
Attack Pattern Recognition: Regular IoC analysis enables security teams to understand attacker tactics, techniques, and procedures (TTPs), thereby improving their ability to anticipate and defend against future attacks.
Threat Intelligence Integration: IoC monitoring programs naturally evolve into comprehensive threat intelligence capabilities, providing strategic insights into the trends and emerging attack methods within the threat landscape.
Skill Development: Consistent IoC analysis enables the security team to develop expertise in forensics, malware analysis, and threat hunting, thereby building organizational security capabilities over time.
Meeting Compliance Requirements
Monitoring IoCs is essential for organizations to meet compliance requirements. Frameworks like NIST, ISO 27001, and PCI DSS mandate continuous monitoring and threat detection, which IoC monitoring supports. It also provides documentation for reporting, logs for audit trails, and evidence of effective cybersecurity risk management for stakeholders.
Regulatory Mandates: Frameworks such as the NIST Cybersecurity Framework, ISO 27001, and PCI DSS require organizations to implement continuous monitoring and threat detection capabilities, which IoC monitoring directly supports.
Incident Response Documentation: IoC monitoring provides the detailed logs and evidence required for compliance reporting, demonstrating due diligence in threat detection and response activities.
Audit Trail Creation: Systematic IoC tracking enables the creation of comprehensive audit trails that document security monitoring activities, investigation procedures, and response actions taken during security incidents.
Risk Management Evidence: IoC monitoring programs provide measurable metrics and documentation that demonstrate effective cybersecurity risk management to auditors, regulators, and business stakeholders.
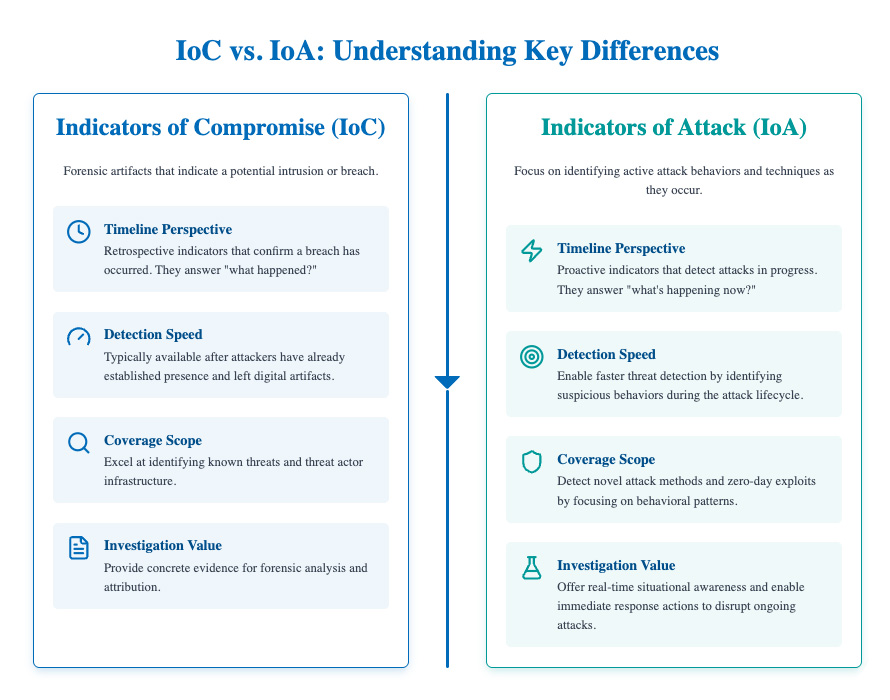
Figure 3: IoC vs IoA: Understanding the Key Differences
IoC vs. IoA
While IoCs and IoAs both aim to identify threats, they differ significantly in their approach, timeline, and strategic application. Understanding the nuances between IoCs, which focus on past evidence of intrusion, and IoAs, which emphasize real-time detection of malicious behavior, is vital for building a comprehensive and proactive defense against modern cyber threats.
Defining Indicators of Attack (IoA)
Real-Time Threat Detection: IoAs focus on identifying active attack behaviors and techniques as they occur, rather than static artifacts left behind. They monitor for suspicious patterns like privilege escalation attempts, lateral movement activities, or unusual data access patterns that indicate an ongoing attack.
Behavioral Analysis: IoAs analyze how attackers operate by examining sequences of actions, timing patterns, and procedural anomalies, for example, detecting when a user account suddenly accesses multiple systems in rapid succession or when administrative tools are used outside normal business hours.
Proactive Threat Hunting: IoAs enable security teams to identify attacks in progress before significant damage occurs, focusing on attacker tactics, techniques, and procedures (TTPs) rather than relying on forensic evidence after a compromise.
MITRE ATT&CK Framework Alignment: IoAs map directly to the MITRE ATT&CK framework, identifying specific attack stages like initial access, persistence, privilege escalation, and data exfiltration as they unfold in real-time.
Complementary Roles in Detection
Timeline Perspective: IoCs are retrospective indicators that confirm a breach has occurred, while IoAs are proactive indicators that detect attacks in progress. IoCs answer "what happened?" while IoAs answer "what's happening now?"
Detection Speed: IoAs enable faster threat detection by identifying suspicious behaviors during the attack lifecycle, whereas IoCs typically become available after attackers have already established a presence and left digital artifacts.
Coverage Scope: IoCs excel at identifying known threats and threat actor infrastructure, while IoAs detect novel attack methods and zero-day exploits by focusing on behavioral patterns rather than specific signatures.
Investigation Value: IoCs provide concrete evidence for forensic analysis and attribution, while IoAs offer real-time situational awareness, enabling immediate response actions to disrupt ongoing attacks.
Strategic Application of Both
Layered Defense Strategy: Organizations should implement both IoC and IoA detection capabilities to create comprehensive threat detection coverage. IoCs provide broad protection against known threats, while IoAs catch sophisticated attacks that bypass signature-based detection.
Threat Intelligence Integration: IoCs feed into threat intelligence platforms for automated blocking and historical analysis, while IoAs inform real-time security orchestration and automated response systems to stop attacks in progress.
Resource Allocation: IoC monitoring can be automated primarily through security tools and feeds, while IoA detection requires more analyst expertise and behavioral analysis capabilities, necessitating strategic investments in both technology and skilled personnel.
Incident Response Optimization: IoAs trigger immediate containment actions during active attacks, while IoCs support post-incident forensics and long-term threat hunting activities. Both are essential for complete incident response capabilities.
The Role of AI and Machine Learning in IoC Detection
Enhancing Anomaly Detection
Behavioral Baselines: Machine learning algorithms establish normal patterns of network traffic, user behavior, and system activity by analyzing historical data. These baselines enable detection of subtle deviations that may indicate compromise, such as unusual login times, abnormal data access patterns, or atypical network communications.
Unsupervised Learning: AI systems utilize clustering and statistical analysis to identify outliers and anomalies, eliminating the need for predefined rules or signatures. This enables the detection of previously unknown attack patterns, zero-day exploits, and novel malware variants that traditional signature-based systems would typically miss.
Multi-Dimensional Analysis: ML algorithms simultaneously correlate multiple data points, examining relationships between network traffic, endpoint behavior, user activities, and system logs to identify complex attack patterns that would be impossible for human analysts to detect manually.
Adaptive Learning: AI systems continuously update their understanding of normal behavior as environments evolve, automatically adjusting detection thresholds and incorporating new data patterns to maintain accuracy as organizational infrastructure and user behavior change over time.
Speeding Up Analysis
Automated IoC Extraction: Machine learning algorithms automatically extract potential IoCs from vast amounts of security data, including log files, network captures, and malware samples, processing millions of events per second to identify relevant indicators in real-time.
Rapid Correlation: AI systems instantly correlate new IoCs against historical data, threat intelligence feeds, and known attack patterns, providing immediate context and threat assessment that would take human analysts hours or days to complete.
Intelligent Prioritization: ML algorithms rank and prioritize IoCs based on confidence scores, threat severity, and potential business impact, ensuring security teams focus on the most critical threats first rather than manually triaging thousands of alerts.
Natural Language Processing: AI systems parse unstructured threat intelligence reports, security advisories, and research papers to automatically extract and classify new IoCs, dramatically accelerating the integration of external threat intelligence into security operations.
Reducing False Positives
Contextual Analysis: Machine learning models consider environmental context, user roles, business processes, and historical patterns when evaluating potential IoCs, thereby significantly reducing the number of benign activities flagged as malicious compared to rule-based detection systems.
Dynamic Threshold Adjustment: AI algorithms automatically tune detection sensitivity based on feedback from security analysts, learning from false positive patterns to improve accuracy over time and reduce alert fatigue among security teams.
Ensemble Methods: Multiple ML models collaborate to validate IoC detections, requiring consensus or weighted voting before generating alerts, which significantly reduces false positives while maintaining high detection rates for legitimate threats.
Feedback Learning: AI systems learn from analyst decisions about true positives and false positives, continuously refining their detection algorithms to better distinguish between legitimate IoCs and benign system artifacts or normal business activities.
Predicting Emerging Threats
Threat Evolution Modeling: ML algorithms analyze historical attack patterns and IoC trends to predict how threat actors might modify their tactics, techniques, and procedures, enabling proactive defense against future attack variants.
Campaign Attribution: AI systems identify relationships between seemingly unrelated IoCs to uncover broader attack campaigns and predict likely future targets, infrastructure, or attack vectors based on observed threat actor behavior patterns.
Synthetic IoC Generation: Advanced machine learning models generate potential future IoCs based on observed patterns of attack evolution, enabling security teams to prepare defenses against predicted threats before they emerge in the wild.
Early Warning Systems: AI algorithms monitor global threat intelligence feeds, dark web communications, and attack trends to provide early warnings about emerging threats and new attack techniques, enabling organizations to update their IoC detection capabilities proactively.
Enforcement Types for Indicators
Validated IoCs are essential for informing cybersecurity actions. Organizations employ various enforcement methods to leverage this intelligence, and these methods form critical layers within a comprehensive security approach.
Blocking and Filtering
Network Perimeter Defense: Firewalls, intrusion prevention systems (IPS), and DNS security solutions automatically block malicious IP addresses, domains, and URLs identified in IoC feeds, preventing initial compromise attempts and command-and-control communications at the network edge.
Email Security Gateways: Anti-spam and email security platforms filter malicious sender addresses, domains, and attachment hashes, blocking phishing campaigns and malware distribution before reaching user inboxes.
Web Content Filtering: Proxy servers and secure web gateways block access to malicious websites, exploit kits, and phishing pages using IoC-derived blacklists, protecting users from drive-by downloads and credential harvesting attempts.
Endpoint Protection: Antivirus engines and endpoint detection systems automatically quarantine or delete files matching known malicious hashes, preventing malware execution and lateral movement across endpoints.
Alerting and Notification
SIEM Alert Generation: SIEM systems generate prioritized alerts when IoCs are detected in network traffic, system logs, or endpoint activities, providing security analysts with immediate notification of potential threats.
Threat Intelligence Notifications: Automated systems alert security teams when new IoCs related to their industry, geography, or technology stack become available, enabling proactive defense against emerging threats.
Executive Dashboards: Real-time dashboards display IoC detection metrics, trending threats, and security posture indicators, providing leadership visibility into organizational threat exposure and security effectiveness.
Stakeholder Communication: Automated notification systems inform relevant business units, legal teams, and external partners when critical IoCs are detected, ensuring appropriate incident response coordination and communication.
Automated Response Actions
Network Isolation: Security orchestration platforms automatically isolate compromised systems from the network when high-confidence IoCs are detected, preventing lateral movement and data exfiltration.
Account Suspension: IAM systems automatically disable user accounts associated with compromised credentials or suspicious authentication patterns identified through IoC analysis.
Process Termination: Endpoint detection and response (EDR) systems automatically terminate malicious processes, remove persistence mechanisms, and remediate registry changes when known malware IoCs are detected.
Traffic Redirection: Network security tools automatically redirect suspicious communications to honeypots or sinkholes, allowing security teams to analyze attack techniques while protecting production systems.
Challenges in IoC Management
Effective utilization of IoCs is crucial for a comprehensive cybersecurity posture. However, the management of IoCs presents several key challenges that organizations must address to maximize their effectiveness.
Alert Fatigue and False Positives
Volume Overwhelm: Security teams receive thousands of IoC-based alerts daily from multiple security tools, creating cognitive overload that leads to missed genuine threats and analyst burnout from constantly triaging low-priority alerts.
Context Limitations: IoCs often lack sufficient context regarding threat severity, business impact, or environmental relevance, resulting in analysts spending excessive time investigating benign activities or outdated threats that no longer pose a risk.
Tuning Complexity: Balancing detection sensitivity to minimize false positives while maintaining coverage requires continuous fine-tuning of IoC rules and thresholds, demanding significant analyst expertise and time investment.
Quality Variance: IoC feeds from different sources vary significantly in accuracy and relevance, with some containing outdated, duplicate, or incorrectly classified indicators that generate numerous false-positive alerts.
Timeliness and Obsolescence of IoCs
Rapid Infrastructure Changes: Threat actors frequently modify IP addresses, domains, and file hashes to evade detection, rendering many IoCs obsolete within days or hours of publication, thereby reducing their defensive value.
Intelligence Lag Time: The time between IoC discovery, analysis, publication, and deployment in security tools creates detection gaps, during which threats remain undetected despite the availability of intelligence.
Lifecycle Management: Organizations struggle to systematically retire outdated IoCs from their security tools, leading to performance degradation and continued false positive generation from obsolete indicators.
Attribution Accuracy: IoC attribution to specific threat actors or campaigns may be incorrect or evolve, leading to misguided defensive priorities and resource allocation decisions.
Integration Complexities
Tool Proliferation: Organizations typically deploy dozens of security tools with varying IoC format requirements, APIs, and update mechanisms, resulting in significant integration overhead and operational complexity.
Data Format Inconsistencies: IoC feeds utilize various formats (STIX, JSON, CSV, XML) and taxonomies, necessitating normalization and translation processes that introduce delays and potential errors in the distribution of threat intelligence.
API Limitations: Many security tools have restrictive API rate limits or batch processing requirements that slow IoC deployment and prevent the integration of real-time threat intelligence.
Legacy System Constraints: Older security infrastructure may lack modern threat intelligence APIs or automated update capabilities, necessitating manual IoC deployment processes that are prone to errors and time-consuming.
Resource Constraints
Skilled Personnel Shortage: Organizations often lack sufficient cybersecurity analysts with threat intelligence expertise to effectively manage IoC programs, resulting in delayed implementation and suboptimal utilization of available intelligence.
Budget Limitations: Comprehensive IoC management requires investments in threat intelligence platforms, security orchestration tools, and analyst training that many organizations cannot afford or justify to leadership.
Computational Resources: Processing and correlating large volumes of IoCs against organizational data requires significant computing power and storage capacity that strains existing infrastructure.
Time Investment: Effective IoC utilization demands continuous monitoring, analysis, and refinement activities that compete with other security priorities and incident response responsibilities.
Best Practices for IoC Utilization
Effective IOC utilization involves continuously monitoring for forensic evidence of malicious activity, integrating threat intelligence, and establishing comprehensive incident response plans to rapidly detect, contain, and remediate cyber threats.
Integrating Threat Intelligence
Multi-Source Strategy: Subscribe to diverse threat intelligence feeds, including commercial providers, government sources, industry-sharing groups, and open-source communities, to ensure comprehensive IoC coverage across different threat actors and attack types.
Contextual Enrichment: Enhance IoCs with additional context such as threat actor attribution, campaign information, confidence scores, and recommended actions to help analysts prioritize investigations and response efforts effectively.
Risk-Based Prioritization: Implement scoring mechanisms that consider IoC confidence levels, threat severity, asset criticality, and business impact to ensure security teams focus on the most relevant and dangerous threats first.
Intelligence Validation: Establish processes to verify IoC accuracy through internal testing, community feedback, and historical analysis, thereby preventing the deployment of false or misleading threat intelligence.
Establishing a Continuous Monitoring Program
24/7 Operations: Implement round-the-clock monitoring capabilities to detect IoC matches in real-time, ensuring threats are identified and responded to regardless of when attacks occur or business hours.
Baseline Establishment: Create comprehensive baselines of normal network traffic, user behavior, and system activity to improve IoC detection accuracy and reduce false positive rates through contextual analysis.
Performance Metrics: Track key performance indicators, such as mean time to detection, false positive rates, IoC coverage effectiveness, and analyst productivity, to continuously improve monitoring program performance.
Regular Assessment: Conduct periodic reviews of monitoring coverage, detection gaps, and emerging threats to ensure the continuous monitoring program adapts to evolving organizational needs and threat landscape.
Automating IoC Deployment
SOAR Integration: Implement Security Orchestration, Automation, and Response platforms to automatically distribute IoCs across security tools, reducing manual deployment time and ensuring consistent threat intelligence coverage.
API Automation: Develop automated workflows that consume threat intelligence feeds and push IoCs to firewalls, DNS filters, endpoint protection systems, and SIEM platforms without manual intervention.
Quality Assurance: Develop automated validation and testing processes that verify IoC formatting, detect duplicates, and validate indicator functionality before deployment to production security systems.
Version Control: Maintain detailed logs of IoC deployments, updates, and removals to support audit requirements, troubleshooting efforts, and rollback procedures when necessary
Regular Review and Refinement
Effectiveness Analysis: Regularly assess which IoCs generate actionable detections versus false positives, retiring ineffective indicators, and adjusting detection rules to improve overall program performance.
Threat Landscape Monitoring: Stay current with evolving attack techniques, emerging threat actors, and new IoC types to ensure detection capabilities remain relevant and effective against current threats.
Feedback Incorporation: Collect and analyze feedback from security analysts, incident responders, and threat hunters to identify IoC program improvements and address operational challenges.
Process Optimization: Continuously refine IoC management processes, tools, and procedures based on lessons learned, industry best practices, and organizational maturity improvements.
Cultivating a Culture of IoC Sharing
Internal Collaboration: Encourage sharing of IoCs discovered during incident response activities across different teams and business units to maximize defensive value and prevent repeat compromises.
Industry Participation: Actively participate in industry information sharing organizations, threat intelligence communities, and security conferences to contribute and receive valuable IoC intelligence.
Public-Private Partnerships: Engage with government cybersecurity initiatives, law enforcement agencies, and regulatory bodies to share and receive IoCs related to national security and critical infrastructure threats.
Vendor Collaboration: Collaborate closely with security vendors, managed service providers, and technology partners to share IoCs and receive customized threat intelligence tailored to the organization's infrastructure and risk profile.
The IoC Lifecycle
Discovery and Creation
Incident Analysis: Security analysts extract IoCs during breach investigations by analyzing malware samples, network traffic, system artifacts, and attacker infrastructure to identify unique IoCs.
Threat Research: Cybersecurity researchers discover new IoCs through malware analysis, attack simulation, honeypot deployment, and dark web monitoring to identify emerging threats and attack techniques.
Community Contributions: Security professionals share IoCs discovered in their environments through industry forums, threat intelligence platforms, and information-sharing organizations to benefit the broader security community.
Automated Generation: ML systems and malware sandboxes automatically generate IoCs by analyzing suspicious files, network communications, and behavioral patterns to scale threat intelligence production.
Sharing and Dissemination
Threat Intelligence Platforms: IoCs are published through commercial and open-source threat intelligence platforms, utilizing standardized formats such as STIX/TAXII to enable automated consumption by security tools.
Industry Networks: Information Sharing and Analysis Centers (ISACs) distribute sector-specific IoCs to member organizations, providing targeted threat intelligence relevant to specific industries or geographical regions.
Government Channels: Federal agencies and national cybersecurity organizations publish IoCs through official bulletins, alerts, and automated feeds to protect critical infrastructure and national security interests.
Vendor Integration: Security vendors incorporate IoCs into their product signatures, detection rules, and threat intelligence services to provide customers with immediate protection against known threats.
Implementation and Monitoring
Tool Integration: IoCs are deployed across various security infrastructure components, including firewalls, intrusion detection systems, endpoint protection platforms, and SIEM solutions, to enable automated threat detection and blocking.
Performance Tracking: Security teams monitor the effectiveness of IoC by tracking detection rates, false positives, and successful threat prevention to measure the value of different intelligence sources and indicator types.
Contextual Analysis: Analysts correlate IoC detections with other security events, user activities, and environmental factors to validate threats and minimize false-positive investigations.
Response Coordination: IoC detections trigger incident response procedures, threat hunting activities, and additional intelligence gathering to understand and contain identified threats fully.
Deprecation and Archiving
Relevance Assessment: Security teams regularly evaluate IoC effectiveness and relevance, retiring indicators that no longer provide detection value due to infrastructure changes or threat evolution.
Historical Preservation: Archived IoCs are retained for forensic analysis, trend analysis, and attribution research even after removal from active detection systems to support long-term security intelligence.
Documentation Maintenance: Comprehensive records of IoC lifecycle events, including creation, deployment, performance, and retirement, are maintained for audit compliance and process improvement initiatives.
Knowledge Transfer: Lessons learned from IoC utilization are documented and shared with security teams to improve future threat intelligence operations and detection capabilities.
Future Trends in IoC
Automation and Orchestration
AI-Driven Intelligence: Advanced artificial intelligence systems will automatically discover, validate, and deploy IoCs at machine speed, dramatically reducing the time between threat identification and defensive implementation across organizational infrastructure.
Contextual Automation: Future systems will automatically enrich IoCs with environmental context, business impact assessments, and recommended response actions, enabling fully automated threat response without human intervention for routine threats.
Cross-Platform Orchestration: Unified security orchestration platforms will seamlessly distribute IoCs across hybrid cloud environments, on-premises infrastructure, and third-party services through standardized APIs and protocols, ensuring a unified approach to security.
Predictive Deployment: Machine learning algorithms will anticipate likely IoC evolution patterns and pre-deploy defensive measures against predicted threat variants before they appear in the wild.
Behavioral Analytics
Intent-Based Detection: Next-generation IoC systems will focus on attacker intent and behavioral patterns, rather than static artifacts, detecting attacks based on procedural anomalies and tactical sequences, regardless of the specific tools or infrastructure used.
User Behavior Analytics: IoC detection will incorporate user and entity behavior analytics to identify compromised accounts, insider threats, and credential abuse through analysis of access patterns, data usage, and privilege escalation activities.
Temporal Pattern Analysis: Advanced analytics will identify time-based attack patterns and sequences that span multiple IoCs, enabling detection of complex, multi-stage attacks that unfold over weeks or months.
Collective Intelligence: Behavioral analytics will aggregate IoC detection patterns across multiple organizations to identify coordinated attacks, campaign evolution, and emerging threat actor tactics at industry scale.
Cloud-Native IoCs
Container-Specific Indicators: Specialized IoCs will emerge for containerized environments, including malicious container images, suspicious orchestration activities, and anomalous inter-service communications in Kubernetes and similar platforms.
Serverless Security: New IoC categories will address serverless computing threats, including malicious function deployments, abnormal execution patterns, and suspicious API gateway activities in cloud-native architectures.
Multi-Cloud Intelligence: IoC systems will provide unified threat intelligence across multiple cloud providers, correlating indicators from AWS, Azure, Google Cloud, and hybrid environments to detect cross-platform attacks.
Infrastructure-as-Code Threats: IoCs will evolve to detect malicious infrastructure deployment patterns, suspicious configuration changes, and compromised DevOps pipelines in cloud-native development environments.
Evolving Threat Landscape
AI-Powered Attacks: IoC detection will adapt to identify artificial intelligence-generated threats, including deepfake social engineering campaigns, AI-crafted malware, and machine learning-assisted attack optimization techniques.
IoT and Edge Computing: Specialized IoCs will emerge for Internet of Things devices, edge computing infrastructure, and operational technology environments as these attack surfaces expand rapidly.
Quantum-Resistant Indicators: Future IoCs will incorporate quantum-resistant cryptographic techniques and detection methods to address threats from quantum computing capabilities and post-quantum cryptographic transitions.
Supply Chain Intelligence: IoC systems will integrate software supply chain analysis, third-party risk assessment, and vendor security intelligence to detect compromised software dependencies and malicious code injection attacks.