- 1. What created the need for container firewalls?
- 2. How do container firewalls work?
- 3. Why use container firewalls?
- 4. Where are container firewalls deployed?
- 5. What is the difference between a container firewall and a virtual firewall?
- 6. How container firewalls help achieve a Zero Trust strategy
- 7. What to look for in a container firewall
- 8. Container firewall FAQs
- What created the need for container firewalls?
- How do container firewalls work?
- Why use container firewalls?
- Where are container firewalls deployed?
- What is the difference between a container firewall and a virtual firewall?
- How container firewalls help achieve a Zero Trust strategy
- What to look for in a container firewall
- Container firewall FAQs
What Is a Container Firewall? How It Works + When to Use One
- What created the need for container firewalls?
- How do container firewalls work?
- Why use container firewalls?
- Where are container firewalls deployed?
- What is the difference between a container firewall and a virtual firewall?
- How container firewalls help achieve a Zero Trust strategy
- What to look for in a container firewall
- Container firewall FAQs
A container firewall is a type of software firewall that inspects and enforces policies on traffic moving between containers and services.
It operates at the level of pods, namespaces, or orchestration frameworks such as Kubernetes to regulate east–west communication. By applying segmentation and runtime inspection, it helps prevent lateral movement and enforces least-privilege access within container workloads.
What created the need for container firewalls?
Containers have become the foundation of modern application development.
Kubernetes and other orchestration tools made it possible to deploy thousands of services that scale up and down in seconds. The result is a level of speed and density that traditional security approaches were never designed to address directly.
Firewalls remain essential at the perimeter and in virtualized environments. But containerized workloads create a new challenge.
Most of their traffic is east–west, moving between pods and services inside clusters. That communication rarely reaches a VM or network boundary, so it requires its own layer of visibility and control.
Kubernetes networking also adds a visibility challenge.
Because of network address translation, all outbound traffic carries the node IP as the source. Firewalls outside the cluster only see the node–not the individual pod or container that generated the traffic. A container firewall avoids this blind spot by enforcing policies inside the cluster itself.
Compliance and Zero Trust strategies reinforce this need.
Regulated applications may share the same cluster with unregulated ones, and policies must be enforced at a very granular level. In other words, organizations need a way to apply segmentation and inspection inside the orchestration fabric itself. Container firewalls, which are a type of software firewall, fill this role.
They secure communication at the pod or namespace level. They provide enforcement points to contain movement inside clusters. And they're consistent with cloud-native architectures and industry standards for container security.
How do container firewalls work?
Container firewalls run inside container orchestration platforms such as Kubernetes.
They integrate with the networking layer of these systems, which allows them to see traffic that moves between pods, namespaces, or microservices. In other words, they operate where traditional or VM-based firewalls have no direct visibility.
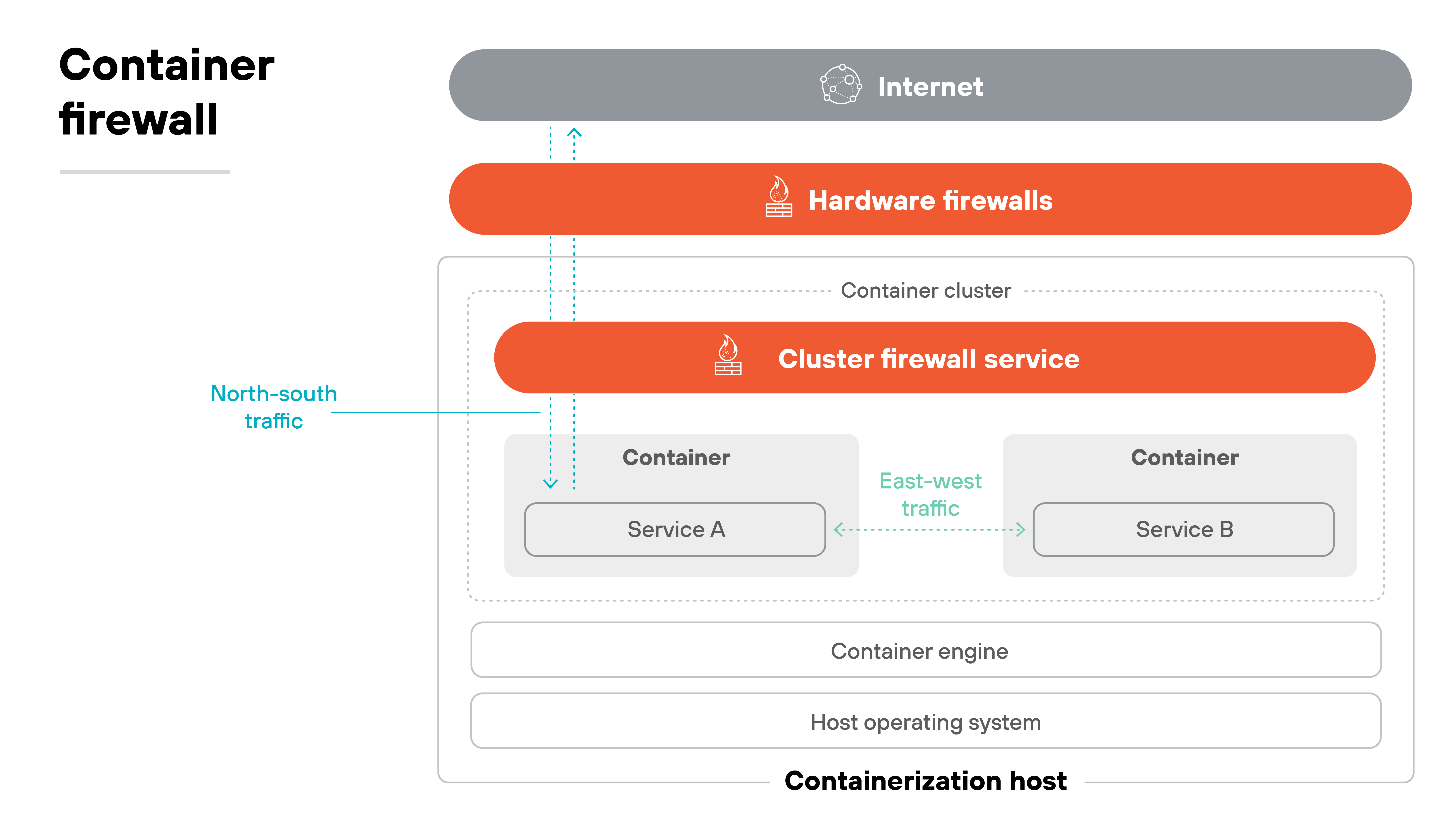
Policies are applied at different levels of the cluster.
For example, rules can govern which pods may talk to each other, which namespaces are isolated, and how traffic flows across services. This makes it possible to enforce segmentation inside the orchestration framework itself.
Enforcement adapts to the runtime state of the cluster.
Pods may spin up or shut down within seconds, and container firewalls evaluate each new connection in that context. This ensures that policy follows workloads as they change, rather than relying on static IP-based rules.
Segmentation takes place within the orchestration fabric.
Sensitive workloads can be placed in tightly controlled namespaces or zones, while general services remain in broader groups. The container firewall enforces those boundaries so traffic cannot move freely between parts of the cluster without authorization.
Identity and context are also used in decisions.
Instead of evaluating only addresses, container firewalls can reference labels, service identity, or role assignments defined in the orchestration system. Which means enforcement aligns more closely with application logic and Zero Trust design.
Why use container firewalls?
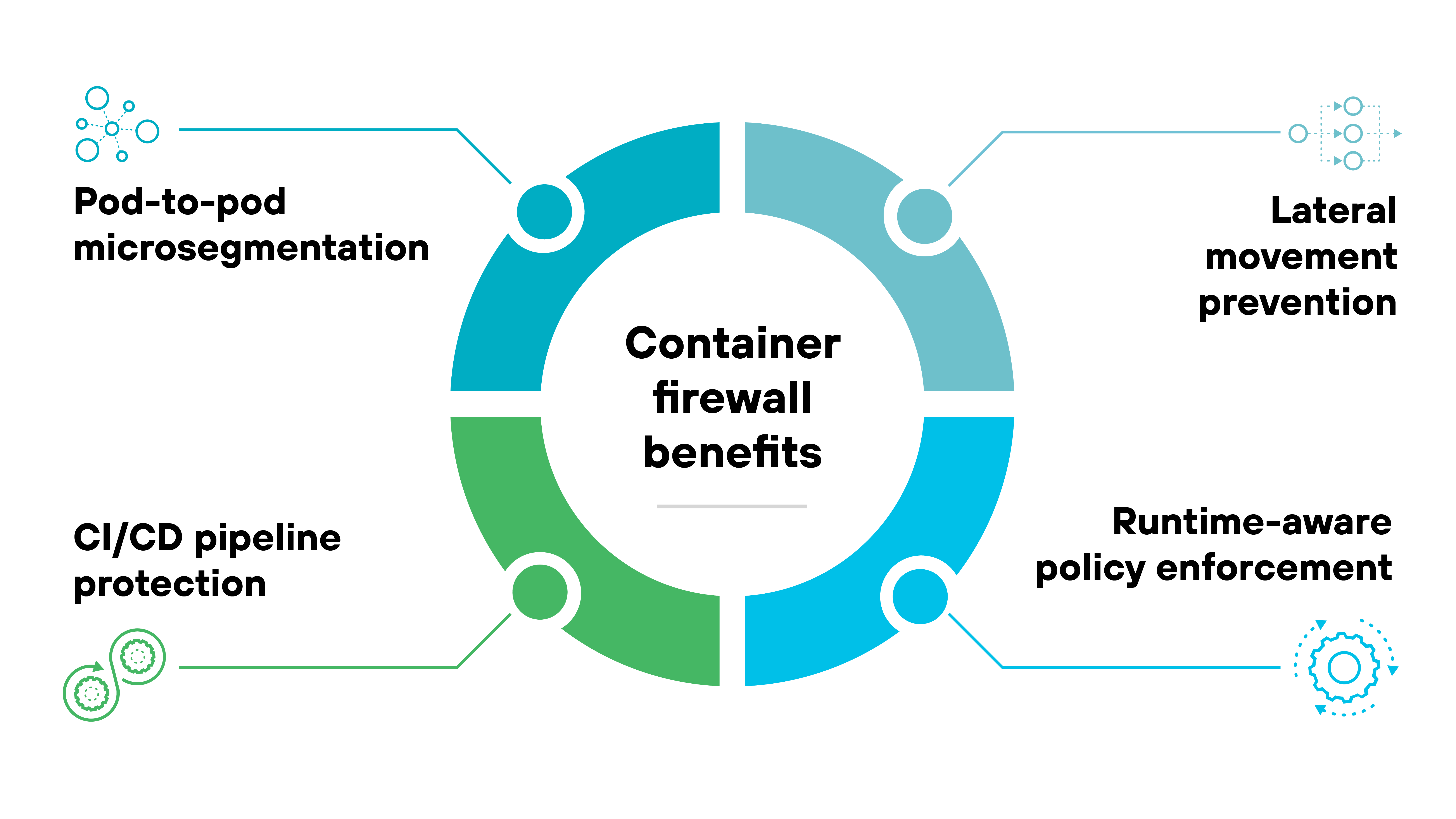
The primary benefit of container firewalls is protecting workloads that run inside Kubernetes and other orchestration systems.
Traditional network and VM firewalls cannot consistently monitor pod-to-pod or namespace-to-namespace traffic that stays within the cluster. A firewall built specifically for containers fills this gap.
Container firewalls implement microsegmentation inside clusters.
This limits the scope of any compromise by defining strict communication boundaries between services and namespaces. It also supports least-privilege principles inside clusters.
They also reduce the risk of lateral movement by controlling pod-to-pod and namespace-to-namespace traffic.
If one container is compromised, a container firewall can stop the attack from spreading to adjacent workloads inside the same cluster. This protection complements, but does not replace, perimeter or VM firewalls.
Another benefit is runtime policy enforcement.
Containers scale up and down quickly. Static rules cannot keep pace. Container firewalls enforce policies dynamically so security controls follow workloads as they appear or disappear.
Protection for CI/CD pipelines is also a major advantage.
Developers often pull images or code from public repositories. A container firewall can restrict outbound connections so workloads only communicate with approved sources, reducing the risk of introducing malicious code during build or deployment.
In short, container firewalls secure internal service communication, enforce segmentation at runtime, and safeguard development pipelines—capabilities that other firewall types are not positioned to deliver.
- What Is Container Runtime Security?
- Securing Your Kubernetes Cluster: Kubernetes Best Practices and Strategies
- How to Secure Kubernetes Secrets and Sensitive Data
Where are container firewalls deployed?
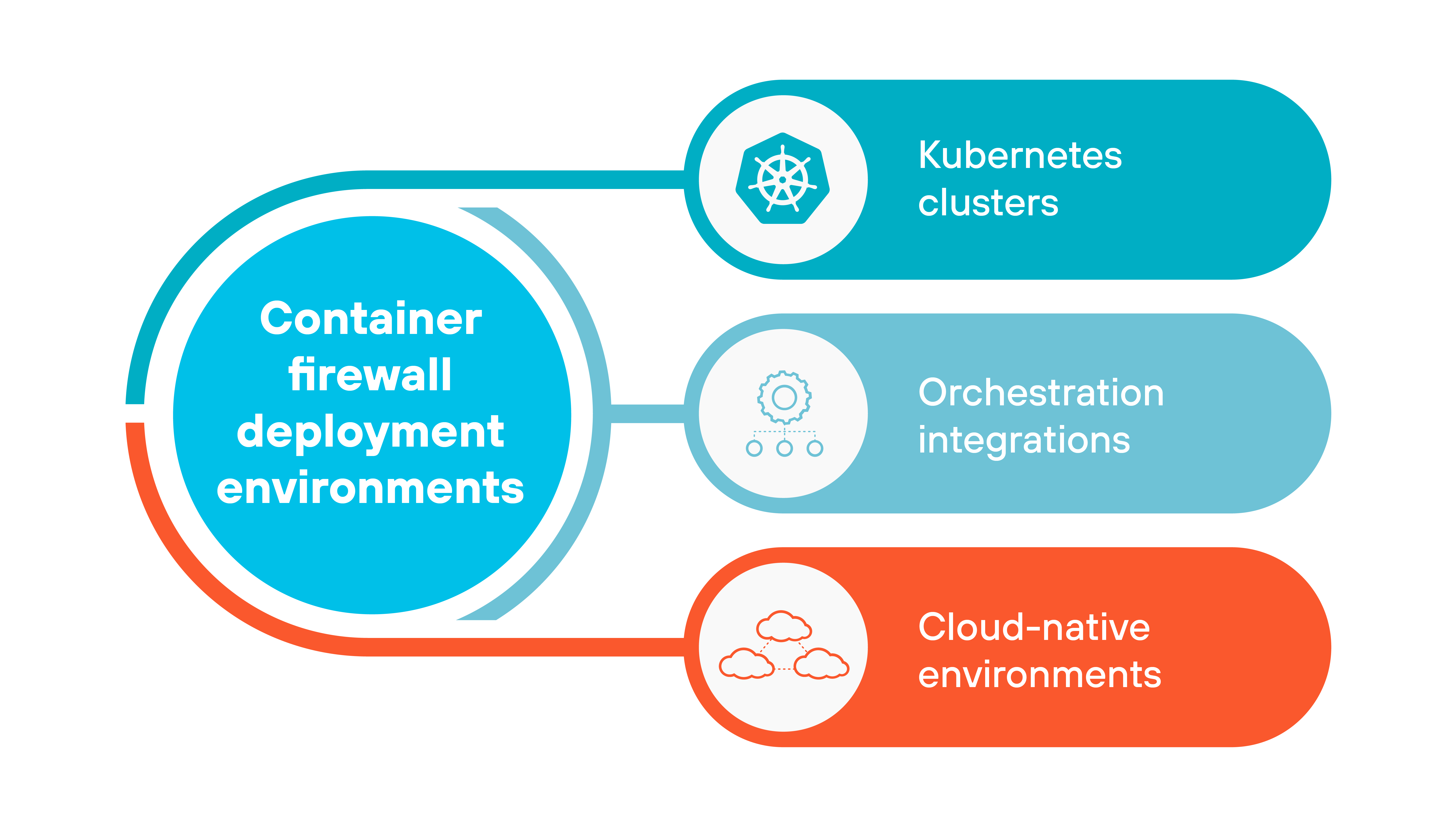
Container firewalls are positioned inside the environments where containers run and communicate.
Here's where they're most often deployed:
- Kubernetes clusters
- Orchestration integrations
- Cloud-native environments
Their role is to enforce policies within the orchestration layers that manage modern applications, rather than at traditional network boundaries.
Kubernetes clusters
Container firewalls are most often deployed inside Kubernetes clusters. They operate at the pod, node, or namespace level to monitor the east–west traffic that moves within the cluster. So they enforce policies directly where services communicate, instead of only at the perimeter.
Orchestration integrations
Container firewalls also integrate with orchestration components such as Container Network Interface (CNI) plugins or service mesh frameworks. This placement allows them to apply rules as part of the cluster's own networking fabric. For instance, policies can be tied to service identity or labels defined by the orchestrator. Which ensures that segmentation follows workloads as they scale.
Cloud-native environments
Finally, container firewalls run across cloud-native deployments. They support public cloud, private cloud, and hybrid environments where containerized workloads are distributed across multiple providers. As a result, centralized policy management is important, since rules must remain consistent even when clusters span different platforms.
What is the difference between a container firewall and a virtual firewall?
| Container firewall vs. virtual firewall |
|---|
| Aspect | Virtual firewall | Container firewall |
|---|---|---|
| Form factor | Runs as a software instance on a virtual machine | Embeds into container orchestration platforms such as Kubernetes |
| Traffic focus | Inspects north–south traffic and communication between VMs | Inspects east–west traffic between pods, nodes, and namespaces |
| Environments | Virtualized data centers, public cloud, hybrid cloud, branch resources | Kubernetes clusters, service mesh, and containerized applications |
| Use cases | Protects general-purpose VMs and cloud-hosted applications | Protects dynamic container workloads with segmentation and runtime enforcement |
| Role | Extends firewall controls into hypervisors and cloud platforms | Acts as a policy enforcement point within container environments |
A virtual firewall runs as a software instance on a virtual machine. It's designed to protect workloads inside virtualized or cloud environments by inspecting north–south traffic and securing communication between VMs. Essentially, it extends the familiar firewall form factor into hypervisors and cloud platforms where hardware appliances cannot be deployed.
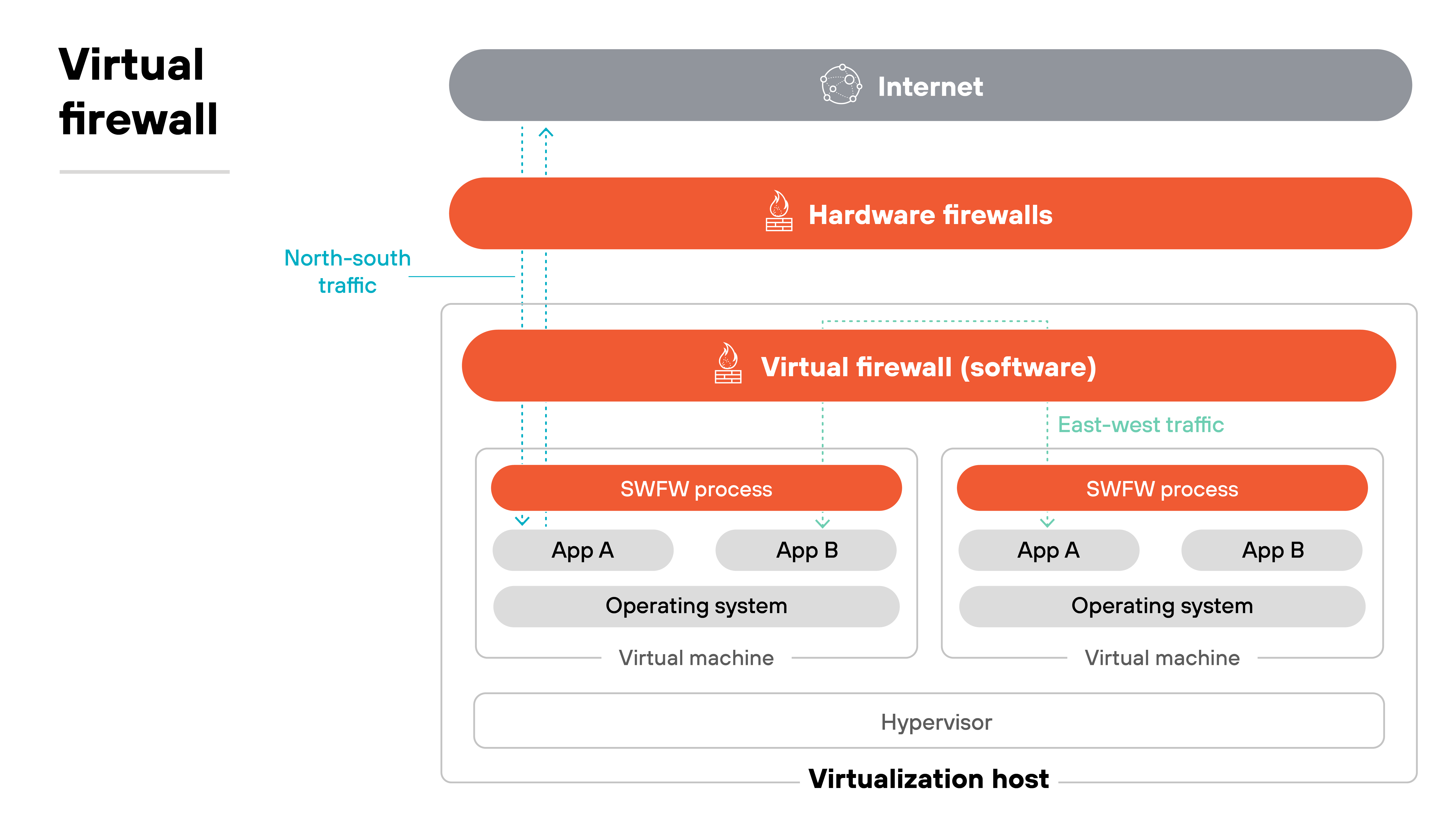
A container firewall operates differently. It embeds into container orchestration platforms such as Kubernetes to inspect traffic that moves between pods, nodes, and namespaces. Which means: it focuses on east–west communication inside clusters, where virtual firewalls have no direct visibility.
The use cases are distinct. Virtual firewalls are best suited for protecting general-purpose VMs, cloud-hosted applications, or branch resources. Container firewalls are built for workloads that scale dynamically through orchestration systems, where segmentation and runtime enforcement are required at a granular level.
Together, they're complementary. Virtual firewalls secure traffic at the VM and cloud level, while container firewalls enforce policies inside containerized environments. Both are software-based, but their placement and purpose are tailored to different layers of modern infrastructure.
Container firewalls fit alongside hardware, virtual, and managed firewalls as part of the overall ecosystem. Each model addresses different layers of the infrastructure, and organizations often deploy several together for comprehensive protection.
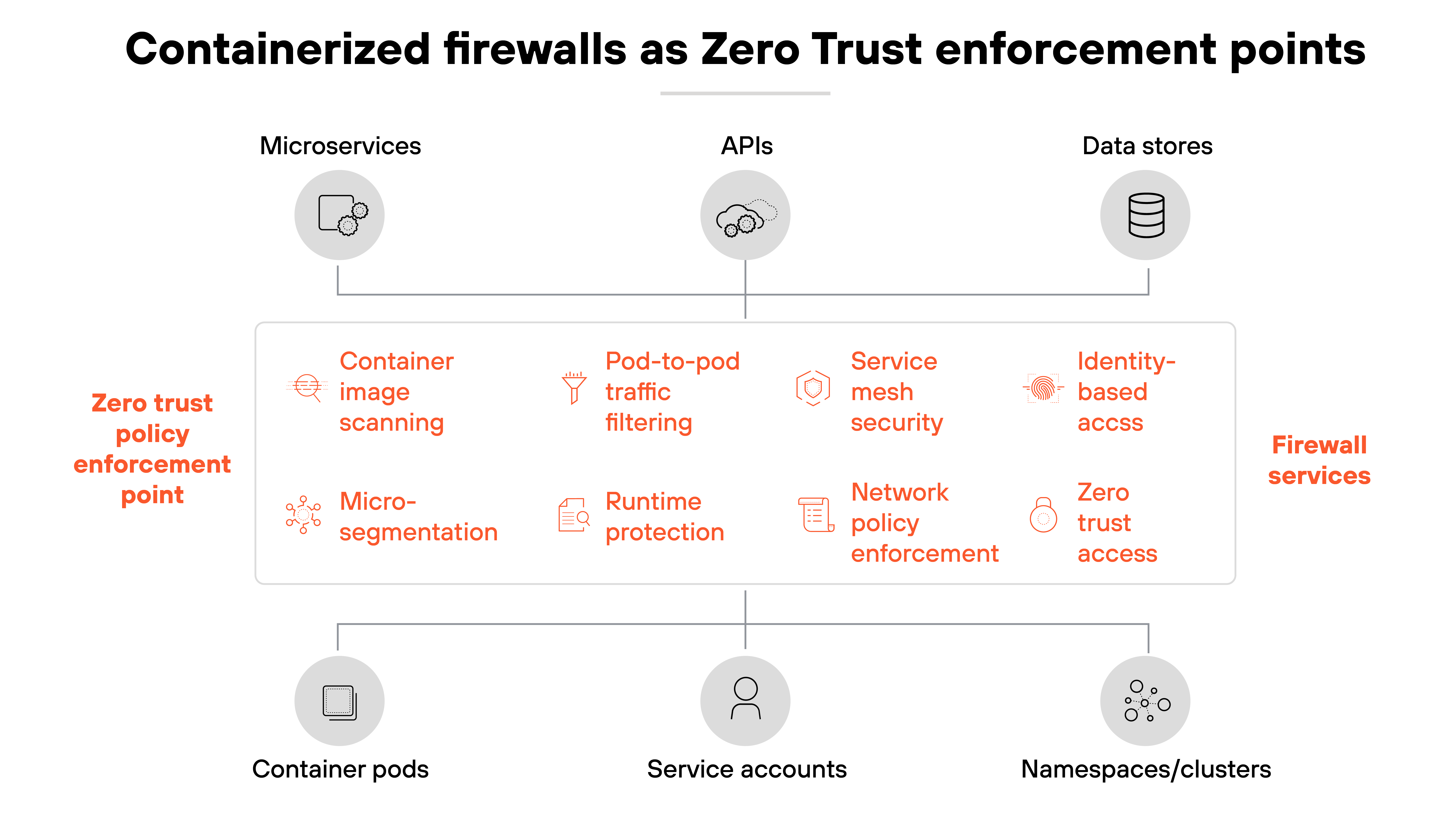
How container firewalls help achieve a Zero Trust strategy
Zero Trust requires security controls to be applied as close to the workload as possible.
Container firewalls make this possible inside orchestration systems such as Kubernetes. They act as enforcement points for traffic that never leaves the cluster but still requires strict control.
As explained, microsegmentation is central to this role. Container firewalls allow policies to be defined between pods, nodes, or namespaces, limiting communication paths to only what is explicitly authorized. And segmentation is a well established way to reduce attack surfaces in containerized applications.
Why is this important?
Because containers are short-lived and scale quickly. Static rules cannot keep up. A container firewall applies rules dynamically. So security policies follow workloads as they start, stop, or move within the cluster.
In a Zero Trust architecture, every workload needs a policy enforcement point.
Container firewalls provide that function inside container environments. They enforce identity- and context-based controls that match orchestration attributes such as labels or service roles. Which means decisions are tied to workload identity, not network location.
To sum up: Container firewalls support Zero Trust by embedding enforcement into the orchestration fabric.
What to look for in a container firewall
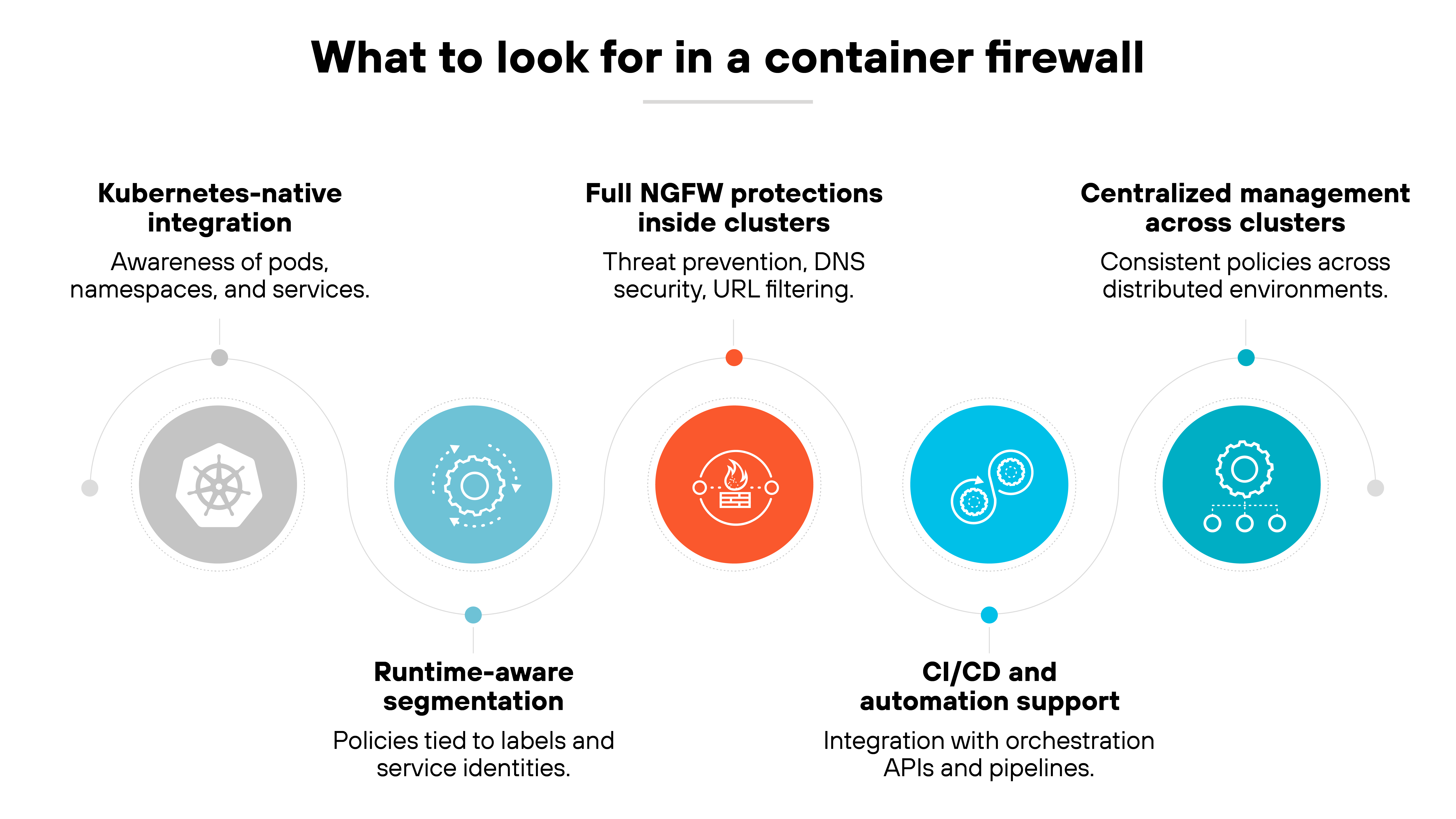
Choosing a container firewall means focusing on how well it fits into orchestration platforms like Kubernetes.
The inspection functions are familiar, but the difference comes down to which features make the firewall effective inside dynamic container environments.
Here are the qualities to prioritize:
Kubernetes-native integration
A container firewall should integrate directly with Kubernetes networking.
That includes awareness of pods, namespaces, and services, as well as visibility past NAT so policies can be applied at the workload level. Without this, external firewalls remain blind to pod-to-pod traffic.
Runtime-aware segmentation
Look for the ability to enforce segmentation as containers start, stop, or move.
The firewall should tie policies to labels or service identities, so rules adapt to the cluster’s runtime state rather than relying on static IPs. This keeps security aligned with ephemeral workloads.
Full NGFW protections inside clusters
A container firewall should bring advanced threat prevention directly into the orchestration layer.
Intrusion prevention, DNS security, and URL filtering need to apply to pod-to-pod and namespace-to-namespace traffic, not just traffic crossing the edge. This ensures the same level of inspection reaches internal service communication.
CI/CD and automation support
Deployment should fit naturally into CI/CD pipelines.
A container firewall that integrates with orchestration APIs and automation tools can enforce outbound connection policies during build and runtime. This prevents unapproved images or code from reaching the environment.
Centralized management across clusters
Management should extend across multiple Kubernetes clusters and cloud providers.
A container firewall that connects into a central console allows teams to define policies once and enforce them consistently across distributed environments. This avoids silos between clusters and keeps container security aligned with broader enterprise firewalls.
