-
What Is a Cyber Attack?
- Threat Overview: Cyber Attacks
- Cyber Attack Types at a Glance
- Global Cyber Attack Trends
- Cyber Attack Taxonomy
- Threat-Actor Landscape
- Attack Lifecycle and Methodologies
- Technical Deep Dives
- Cyber Attack Case Studies
- Tools, Platforms, and Infrastructure
- The Effect of Cyber Attacks
- Detection, Response, and Intelligence
- Emerging Cyber Attack Trends
- Testing and Validation
- Metrics and Continuous Improvement
- Cyber Attack FAQs
- Dark Web Leak Sites: Key Insights for Security Decision Makers
-
What Is a Zero-Day Attack? Risks, Examples, and Prevention
- Zero-Day Attacks Explained
- Zero-Day Vulnerability vs. Zero-Day Attack vs. CVE
- How Zero-Day Exploits Work
- Common Zero-Day Attack Vectors
- Why Zero-Day Attacks Are So Effective and Their Consequences
- How to Prevent and Mitigate Zero-Day Attacks
- The Role of AI in Zero-Day Defense
- Real-World Examples of Zero-Day Attacks
- Zero-Day Attacks FAQs
-
What Is Lateral Movement?
- Why Attackers Use Lateral Movement
- How Do Lateral Movement Attacks Work?
- Stages of a Lateral Movement Attack
- Techniques Used in Lateral Movement
- Detection Strategies for Lateral Movement
- Tools to Prevent Lateral Movement
- Best Practices for Defense
- Recent Trends in Lateral Movement Attacks
- Industry-Specific Challenges
- Compliance and Regulatory Requirements
- Financial Impact and ROI Considerations
- Common Mistakes to Avoid
- Lateral Movement FAQs
-
What is a Botnet?
- How Botnets Work
- Why are Botnets Created?
- What are Botnets Used For?
- Types of Botnets
- Signs Your Device May Be in a Botnet
- How to Protect Against Botnets
- Why Botnets Lead to Long-Term Intrusions
- How To Disable a Botnet
- Tools and Techniques for Botnet Defense
- Real-World Examples of Botnets
- Botnet FAQs
- What is a Payload-Based Signature?
-
What is Spyware?
- Cybercrime: The Underground Economy
-
What Is Cross-Site Scripting (XSS)?
- XSS Explained
- Evolution in Attack Complexity
- Anatomy of a Cross-Site Scripting Attack
- Integration in the Attack Lifecycle
- Widespread Exposure in the Wild
- Cross-Site Scripting Detection and Indicators
- Prevention and Mitigation
- Response and Recovery Post XSS Attack
- Strategic Cross-Site Scripting Risk Perspective
- Cross-Site Scripting FAQs
- What Is a Dictionary Attack?
- What Is a Credential-Based Attack?
-
What Is a Denial of Service (DoS) Attack?
- How Denial-of-Service Attacks Work
- Denial-of-Service in Adversary Campaigns
- Real-World Denial-of-Service Attacks
- Detection and Indicators of Denial-of-Service Attacks
- Prevention and Mitigation of Denial-of-Service Attacks
- Response and Recovery from Denial-of-Service Attacks
- Operationalizing Denial-of-Service Defense
- DoS Attack FAQs
- What Is Hacktivism?
-
What Is CSRF (Cross-Site Request Forgery)?
- CSRF Explained
- How Cross-Site Request Forgery Works
- Where CSRF Fits in the Broader Attack Lifecycle
- CSRF in Real-World Exploits
- Detecting CSRF Through Behavioral and Telemetry Signals
- Defending Against Cross-Site Request Forgery
- Responding to a CSRF Incident
- CSRF as a Strategic Business Risk
- Key Priorities for CSRF Defense and Resilience
- Cross-Site Request Forgery FAQs
- What Is Spear Phishing?
-
What Is Brute Force?
- How Brute Force Functions as a Threat
- How Brute Force Works in Practice
- Brute Force in Multistage Attack Campaigns
- Real-World Brute Force Campaigns and Outcomes
- Detection Patterns in Brute Force Attacks
- Practical Defense Against Brute Force Attacks
- Response and Recovery After a Brute Force Incident
- Brute Force Attack FAQs
- What is a Command and Control Attack?
- What Is an Advanced Persistent Threat?
- What is an Exploit Kit?
- What Is Credential Stuffing?
- What Is Smishing?
-
What is Social Engineering?
- The Role of Human Psychology in Social Engineering
- How Has Social Engineering Evolved?
- How Does Social Engineering Work?
- Phishing vs Social Engineering
- What is BEC (Business Email Compromise)?
- Notable Social Engineering Incidents
- Social Engineering Prevention
- Consequences of Social Engineering
- Social Engineering FAQs
-
What Is a Honeypot?
- Threat Overview: Honeypot
- Honeypot Exploitation and Manipulation Techniques
- Positioning Honeypots in the Adversary Kill Chain
- Honeypots in Practice: Breaches, Deception, and Blowback
- Detecting Honeypot Manipulation and Adversary Tactics
- Safeguards Against Honeypot Abuse and Exposure
- Responding to Honeypot Exploitation or Compromise
- Honeypot FAQs
- What Is Password Spraying?
- How to Break the Cyber Attack Lifecycle
-
What Is Phishing?
- Phishing Explained
- The Evolution of Phishing
- The Anatomy of a Phishing Attack
- Why Phishing Is Difficult to Detect
- Types of Phishing
- Phishing Adversaries and Motives
- The Psychology of Exploitation
- Lessons from Phishing Incidents
- Building a Modern Security Stack Against Phishing
- Building Organizational Immunity
- Phishing FAQ
- What Is a Rootkit?
- Browser Cryptocurrency Mining
- What Is Pretexting?
- What Is Cryptojacking?
What Is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack aims to disrupt a server, service, or network by overwhelming it with a massive flood of internet traffic. These malicious attempts leverage multiple compromised computer systems, making mitigation challenging and posing a significant threat to online availability.
Key Points
-
Service Disruption: DDoS attacks aim to make online services and resources unavailable to legitimate users by overwhelming the target with traffic. -
Distributed Nature: These attacks originate from multiple compromised devices, often forming a botnet, making them harder to trace and mitigate than single-source DoS attacks. -
Impact on Operations: Successful DDoS attacks can lead to significant operational downtime, financial losses, and reputational damage for affected organizations. -
Evolving Threat: Attackers continuously develop new DDoS techniques, requiring organizations to maintain vigilant and adaptive defense strategies. -
Comprehensive Defense: Effective DDoS protection involves a multi-layered approach that combines network infrastructure, specialized mitigation services, and proactive threat intelligence.
Threat Overview
Distributed denial-of-service (DDoS) is a tactic and attack pattern rather than a vulnerability. DDoS attacks fall under TA0040: Impact in the MITRE ATT&CK framework, most commonly aligning with T1499: Endpoint Denial of Service and its sub-techniques, as well as T1498: Network Denial of Service. While MITRE currently frames these techniques in the context of endpoint or network targeting, real-world DDoS campaigns often combine multiple layers to impair infrastructure, applications, and service chains simultaneously.
DDoS attacks are distinct from application-level exploits, which target logic flaws, and from volumetric network floods, which seek to saturate throughput. A modern DDoS campaign may combine both. Synonymous or related terms include volumetric attack, application-layer DoS, protocol abuse, and resource exhaustion. The term “DoS” refers to the single-source variant, while “DDoS”, nearly universal in real-world incidents, specifies the distributed model.
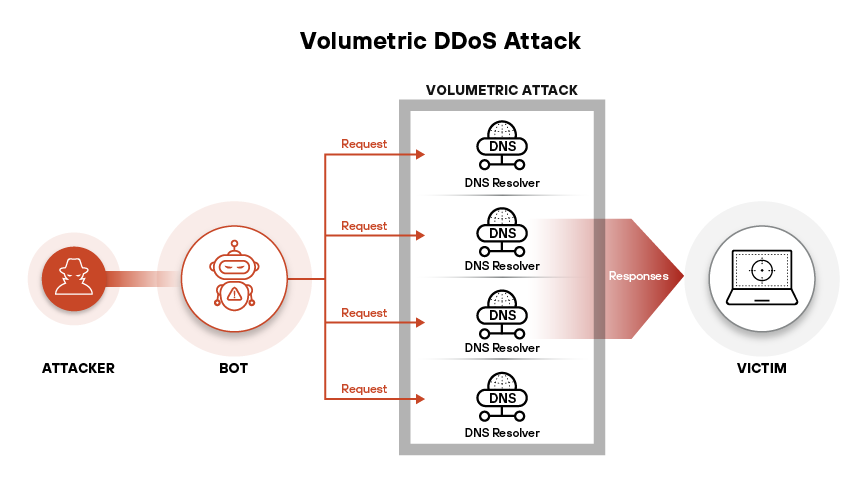
Figure 1: In this DDoS attack using DNS amplification, spoofed requests are sent to open DNS resolvers, which return amplified traffic to the victim.
Evolution of DDoS Techniques
The earliest denial-of-service attacks in the 1990s relied on basic flooding — single hosts issuing repeated requests to crash or freeze vulnerable systems. The late 1990s and early 2000s saw the rise of botnets like Trinoo and TFN, which introduced distributed command and control (C2) for orchestrating traffic from multiple compromised hosts. Attackers exploited insecure services and poor endpoint hygiene to build scale.
As defenses adapted, attackers shifted from bandwidth saturation alone to exploiting protocol behaviors. Reflection and amplification attacks used misconfigured DNS, NTP, SSDP, and Memcached servers to multiply traffic volumes while obscuring origin. A single query could yield hundreds of times its size in attack payload.
Application-layer DDoS attacks followed. These target resource-intensive operations (i.e., login pages, search queries) with low-and-slow tactics that consume CPU or database calls without triggering volumetric alarms. Such attacks are harder to detect and filter, as they often mimic legitimate traffic.
In the last decade, DDoS campaigns have grown in sophistication and accessibility. Botnets now incorporate cloud workloads, containerized assets, and infected IoT devices. Traffic routing often leverages proxy networks or anonymity infrastructure like VPN exit nodes and residential IPs. Attack tools are commoditized and available in criminal marketplaces, often bundled with dashboards, SLA guarantees, and payment options.
Tactical Complexity
Modern DDoS attacks don’t remain static. Cyber criminals frequently pivot between L3/L4 volumetric floods and Layer 7 attacks midstream, forcing defenders to operate across multiple control planes in real time. Attackers also employ burst patterns, randomized intervals, and adaptive payload construction to evade behavioral signatures and rate-based throttling.
More than a brute force tactic, DDoS represents a deliberate, evolving threat technique designed to test resilience and punish latency-sensitive services. It’s also increasingly used to extract ransom without breaching data. As infrastructure becomes more elastic and API-driven, DDoS tactics have shifted to exploit not just resource ceilings but also billing models and operational workflows and recovery gaps.
How Distributed Denial-of-Service Attacks Work
A DDoS attack weaponizes volume, concurrency, or resource sensitivity to disrupt the availability of targeted infrastructure or services. The mechanics differ based on the layer of the stack being targeted, but the outcome remains the same: intentional exhaustion of service capacity until legitimate requests fail or experience unacceptably high latency.
Coordinated Traffic Amplification
Attackers begin by recruiting a distributed set of sources to generate traffic. Botnets remain the most common vehicle, often comprising compromised routers, IoT devices, misconfigured cloud instances, or containerized workloads running in abused CI pipelines. Command-and-control infrastructure may operate over encrypted channels, DNS-based tunneling, or direct socket connections, issuing instructions and rotating payload types midstream.
Many DDoS attacks rely on reflection or amplification. In a typical reflection attack, the adversary sends forged requests to stateless services (i.e., DNS, NTP, CLDAP) with the source IP spoofed as the victim’s. The service replies to the forged address, pushing large volumes of traffic toward the target without exposing the attacker's origin. Amplification arises when the response is significantly larger than the request. A 60-byte DNS query can produce a 4,000-byte response, yielding a 66× amplification factor.
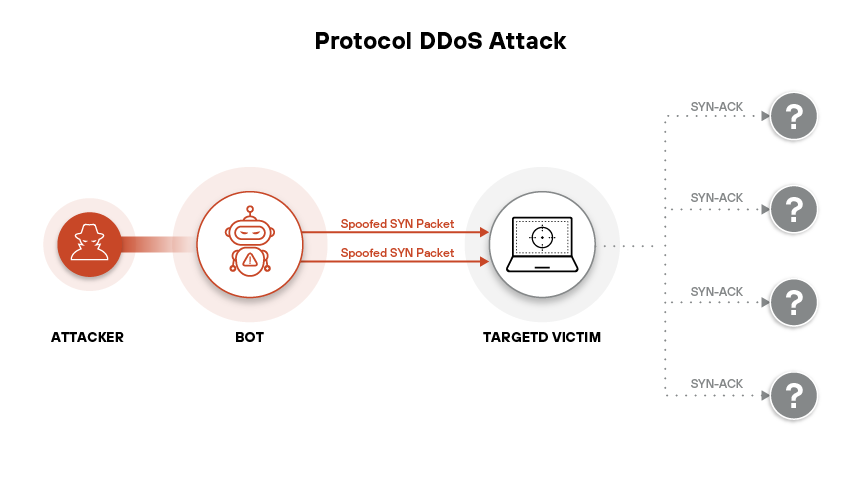
Figure 2: A protocol DDoS attack using spoofed SYN packets floods the victim with fake connection requests, exhausting resources through half-open TCP sessions
Protocol Exploitation and State Exhaustion
Volumetric attacks at Layers 3 and 4 use raw bandwidth saturation or connection flooding to impair routers, firewalls, or load balancers. SYN floods, for instance, exploit TCP’s handshake by sending an overwhelming number of SYN packets and never completing the connection. Servers allocate memory and processing to track half-open connections, which soon exhaust available sockets. UDP floods, ICMP floods, and fragmented packet floods also stay in rotation.
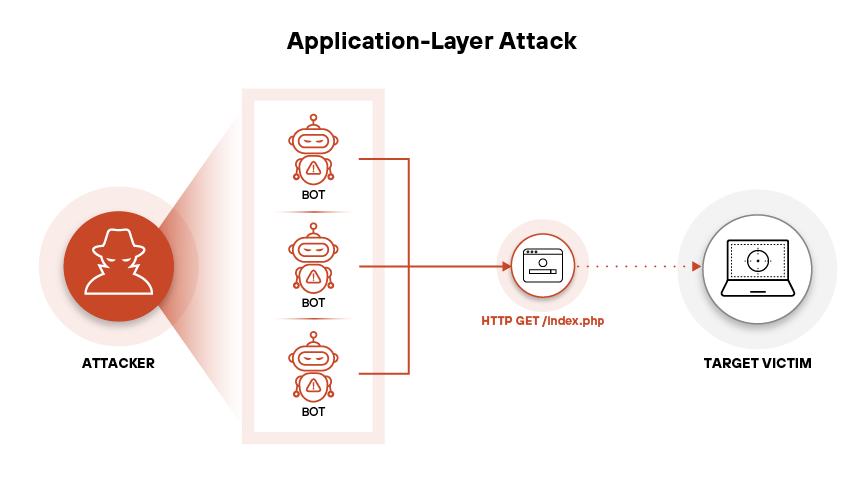
Figure 3: An application-layer DDoS attack with bots sends repeated HTTP GET requests to exhaust server resources
At the application layer, attackers shift from raw throughput to resource exhaustion. HTTP floods target endpoints with high computational cost. Attackers often randomize headers or use rotating user agents. Some simulate browser behavior to evade caching and fingerprint-based mitigations.
Many attacks go further, combining application-layer pressure with bot activity that mimics user interactions. Slowloris, for example, holds open concurrent HTTP connections and sends headers in tiny increments. Servers allocate memory per connection, keeping them alive indefinitely and starving new clients.
Tools and Delivery Infrastructure
Open-source tools like LOIC, HOIC, MHDDoS, and Hammer remain widely available and easily customized. More sophisticated kits integrate browser-based JavaScript payloads, leveraging WebSocket abuse or WebRTC signaling to conscript users’ browsers into DDoS operations via phishing campaigns or malicious ad networks.
Attackers increasingly route traffic through proxy networks. Residential proxy services, nominally designed for legitimate market research, can be abused to anonymize traffic and inject plausible request patterns. Similarly, VPN exit nodes, Tor relays, or hijacked CDN edge servers may relay payloads, complicating attribution and null routing.
In cloud environments, attackers may exploit misconfigured services to amplify effects. Public-facing Kubernetes dashboards, unauthenticated APIs, or serverless functions with poor concurrency controls all represent viable footholds for recursive or bounce-based attacks.
Hybrid and Evasive Variants
Modern campaigns don’t rely on a single technique. Attackers frequently blend Layers 3, 4, and 7 into hybrid operations that adapt in real time. A campaign may begin with a UDP flood, switch to a TLS handshake attack and pivot to HTTP/2 multiplexed requests once defenses adjust.
Some operations employ burst attacks, hitting in short, high-volume waves spaced by irregular intervals. Others persist at subthreshold levels, avoiding detection while incrementally degrading performance. Layer 7 attacks often mimic legitimate traffic profiles, making pattern-based mitigation unreliable.
Ultimately, DDoS succeeds by forcing defenders to expend resources (i.e., bandwidth, CPU cycles, memory, time) faster than the attacker. Unlike traditional exploits, success depends on exploiting architecture, as well as assumptions and limits.
DDoS in Multistage Attack Campaigns
Distributed denial-of-service is often misclassified as a standalone threat, detached from strategic intent. In reality, DDoS is frequently integrated into larger attack workflows, either as a diversion or a mechanism for extortion and control. While it doesn’t enable access directly, it manipulates the conditions under which defenders must operate, forcing distraction or degradation.
Diversion for Initial Access and Lateral Movement
Many adversaries use DDoS as a smokescreen to mask reconnaissance, credential abuse, or infrastructure tampering. During high-throughput attacks against external applications or APIs, defenders divert resources to response and containment. The shift in attention weakens monitoring elsewhere, often across VPN gateways, cloud management interfaces, or identity providers. Attackers exploit that window to probe for misconfigurations or initiate login attempts using stolen or brute-forced credentials.
In hybrid environments, sustained DDoS pressure may lead defenders to temporarily relax WAF rules, reconfigure rate limits, or expose bypass endpoints to preserve service continuity. Adversaries monitor these adjustments in real time and pivot to lateral movement through compromised user sessions or overprivileged service tokens.
Precursor to Exploitation and Privilege Escalation
In advanced attacks, DDoS serves as an access enabler — not by breaching systems, but by weakening or destabilizing defenses. A volumetric DDoS attack, for example, may cause rate-limiting services, authentication APIs, or network telemetry collectors to fail open. Where load balancers or CDNs sit in front of critical applications, saturation may trigger fallback behaviors that expose administrative interfaces or bypass geofencing restrictions.
Privileged access often depends on consistent telemetry and enforcement. DDoS interruptions can delay log propagation to SIEMs, degrade MFA response times, or temporarily disable session validity checks. Adversaries exploit those moments to escalate privileges or exfiltrate credentials undetected.
Post-Compromise Leverage and Extortion
Following initial compromise, DDoS may serve as a coercive tool. Ransom DDoS (RDDoS) groups operate by threatening sustained outages unless a fee is paid. Others use DDoS in retaliation for detection, targeting SOC platforms, ticketing systems, or threat intelligence portals to impair incident response coordination.
When malware is already in place, a timed DDoS event may coincide with destructive payloads. For instance, wipers or ransomware operators may launch a DDoS campaign concurrent with data encryption to delay forensic analysis, isolate teams from cloud-based management consoles, or flood VPN endpoints, impeding remote recovery efforts.
Dependencies and Enablers
DDoS rarely operates in isolation. It thrives in environments with:
- Inconsistent observability: Lack of end-to-end telemetry across control planes and cloud regions increases blind spots.
- Overreliance on perimeter filtering: Static rate limits or appliance-based filtering fail against dynamic, distributed traffic.
- Fragmented response workflows: Separate teams managing DDoS, identity, and threat detection introduce latency and reduce decision quality under pressure.
- Unscalable service architectures: APIs or web applications with blocking operations, unbounded concurrency, or non-idempotent behavior are especially vulnerable.
Adversary Workflow Integration
Below is a simplified DDoS integration path within a multistage attack lifecycle:
Step 1: Reconnaissance
The attacker profiles DNS records, service endpoints, and CDN configurations. They identify rate-limited APIs and sensitive transactional paths.
Step 2: Pre-positioning
Botnets are activated or rented. Reflection vectors (e.g., DNS or NTP servers) are validated. Application endpoints are tested for cost-to-execute ratios.
Step 3: Initial Access (Parallel)
While DDoS initiates pressure on the frontend, other tools attempt credential stuffing, token reuse, or phishing-based entry.
Step 4: Defensive Manipulation
SOC attention shifts. Rate-limiting rules are adjusted. Access controls may loosen. Monitoring thresholds are tuned to avoid false positives.
Step 5: Lateral Movement/Privilege Escalation
Compromised credentials or sessions are used to move laterally. Weak MFA or overpermissioned roles become vectors for privilege gain.
Step 6: Payload Execution or Extortion
Ransomware is detonated, or extortion emails are issued while systems remain offline. In other variants, persistent access is maintained.
Step 7: Cleanup or Prolonged Disruption
DDoS persists beyond breach to complicate recovery or to reinforce extortion demands.
DDoS applies pressure tactically to expose seams in process, policy, and posture. In the context of broader adversary strategies, it functions as an instrument of timing and leverage.
Real-World DDoS Incidents and Organizational Impact
Modern DDoS attacks have evolved beyond headline-making outages into persistent, targeted campaigns. The past 18 months have produced a wave of impactful incidents across multiple sectors, each demonstrating the operational and financial consequences of fragile service availability under attack pressure.
DDoS Disruption at Denmark’s Central Bank
In one of the most coordinated campaigns to target a national financial ecosystem, at least seven banks in Denmark, including the central bank, suffered a wave of DDoS attacks beginning on January 9, 2024. The attacks overloaded websites and online banking platforms, causing hours of inaccessibility for retail and commercial users. The attackers, identified as the hacktivist group NoName057(16), used DDoS as a protest mechanism while demonstrating tactical precision. They rotated targets daily and adjusted payloads to evade static defenses.
While no data was exfiltrated, the campaign disrupted interbank clearing operations and temporarily degraded public confidence. Several institutions triggered business continuity protocols, rerouting traffic through scrubbing centers and deploying emergency rate-limiting measures at the CDN layer. The case reinforced that regulatory oversight alone doesn't ensure service resilience.
HTTP/2 Rapid Reset Attacks at Scale
A newly weaponized vector targeting the HTTP/2 protocol led to the largest DDoS events recorded. Google Cloud reported defending against an attack that peaked at 398 million RPS (requests per second). Amazon and Cloudflare faced similar incidents during the same period. These attacks exploited the protocol’s stream multiplexing feature by sending repeated RST_STREAM frames to initiate and cancel requests rapidly, consuming server resources without waiting for a full payload exchange.
Unlike volumetric floods, the Rapid Reset vector required fewer bots and less traffic volume to overwhelm application-layer infrastructure. It bypassed most rate-based thresholds and forced providers to coordinate emergency patches across HTTP/2 libraries. Cloud-native services that lacked full Layer 7 traffic introspection remained vulnerable for weeks, exposing a critical visibility gap in popular microservice architectures.
DDoS-for-Hire Targeting U.S. Healthcare Facilities
A surge in DDoS-for-hire services, marketed under “stresser” branding, contributed to a spike in healthcare outages across the United States. One campaign in March 2024 focused on regional hospital networks in Illinois and Michigan. Attackers flooded telehealth and EHR (electronic health record) platforms during peak appointment hours, causing delayed consultations and temporary data synchronization failures across cloud-hosted portals.
Some facilities experienced up to 90 minutes of downtime, forcing a manual switch to backup communication lines. The attacks were traced to paid API keys from illicit marketplaces selling access to residential proxy networks and open reflector nodes. While no patient data was stolen, the resulting impact triggered HHS notifications and placed scrutiny on third-party digital service vendors that hadn’t implemented anti-DDoS controls at the edge.
Detection and Frequency Trends
DDoS campaigns have become both more frequent and harder to attribute. According to NETSCOUT’s Threat Intelligence Report, there were 7.9 million DDoS attacks globally in 2023, representing a 13% year-over-year increase. Of these, two-thirds lasted under 15 minutes, reflecting a shift to short-burst attacks designed to test defenses or degrade uptime without detection.
Attackers are increasingly targeting DNS, authentication, and API gateways, components whose failure causes service-wide ripple effects. In SaaS and fintech, even a 90-second outage can trigger SLA penalties or automated failover to less secure configurations.
The pace and precision of modern DDoS attacks underscore the risk of treating availability as an assumed baseline. Without dynamic, multilayered mitigation, many cloud-forward organizations will discover that resiliency can be one packet flood away from collapse.
DDoS Attack Detection Indicators
DDoS detection depends on identifying velocity, volume, and entropy changes across network and application layers. The key to early identification lies in deviation from established norms, such as rate, sequence, distribution, and protocol fidelity.
Observable Indicators Across the Stack
DDoS signals rarely originate from a single source. Telemetry must be aggregated across CDN edge locations, origin servers, DNS resolvers, API gateways, and authentication layers. Indicators vary depending on attack type, but common artifacts surface at all tiers.
Network-layer indicators often include sudden spikes in inbound traffic without a proportional increase in legitimate user behavior. You may observe:
- Sustained TCP SYN floods without corresponding ACK completions
- Unsolicited UDP traffic from high-port source ranges
- ICMP floods originating from spoofed or non-routable address space
- DNS query floods targeting single domains with randomized subdomains (DNS water torture)
- Unusual TTL values or packet sizes indicating crafted payloads
Application-layer indicators typically appear in web server logs, WAF dashboards, or reverse proxy metrics. Red flags include:
- High RPS to single endpoints, particularly those triggering expensive backend operations
- Header spoofing, such as invalid user-agent strings or mismatched Accept-Encoding values
- Malformed HTTP verbs (e.g., OPTIONS, TRACE) in large volumes
- Repeated POSTs with no variation in payload size or content
- Unusually high concurrency from single IPs or rotating IP blocks with consistent session behavior
Protocol abuse indicators often involve legitimate services being manipulated beyond expected volume. Reflection attacks show up as:
- Burst traffic from known open resolvers or NTP servers
- Request-to-response byte ratio anomalies, especially responses exceeding 10x the request size
- Repeated RST_STREAM frames in HTTP/2 environments signaling rapid connection resets
Behavioral Patterns and Attack Fingerprints
Modern DDoS attacks often blend volume with behavior-aware tactics. Even low-volume probes can precede full-scale events. Indicators of pending or active behavioral abuse include:
- Bursts of traffic following login flows but failing at token exchange
- Intentional header variance to evade caching or content delivery optimizations
- Slowloris-style header trickling, where HTTP headers are sent over long durations to hold sockets open
- Burst traffic against legacy endpoints with known computation-heavy responses, such as XML parsers or image conversion routines
- API calls without authorization tokens, especially at odd intervals or nonstandard times
Attackers increasingly rotate patterns to defeat anomaly-based detection. Look for nonhuman click cadence, predictable inter-request timing, or geographic distribution mismatches relative to customer base.
Monitoring and Telemetry Strategy
Effective detection requires a layered telemetry strategy. Relying solely on perimeter signals (i.e., volumetric thresholds at a firewall, netflow summaries) creates blind spots. Instead, prioritize deep visibility across:
- Reverse proxies and API gateways: Monitor request patterns, header integrity, and endpoint concentration. Flag deviations from typical token validation or auth flows.
- DNS analytics: Track query per second (QPS) spikes, randomized subdomains, or geographic anomalies.
- Load balancers: Watch for imbalance across nodes or exhaustion of connection pools.
- XDR/SIEM platforms: Correlate spikes in RPS, error codes (HTTP 429, 503), dropped packets, and service latency.
- Synthetic monitoring agents: Place external probes across key regions to alert on rising latency, dropped transactions, or service degradation patterns not reflected internally.
Metrics should include not just request volume, but also distribution entropy, in addition to cache bypass rates and protocol-level status codes. Alerting should adapt to each application’s baseline with logic that prioritizes deviations by endpoint criticality.
DDoS doesn't hide in plain sight. It hides in volume, exploiting systems where visibility is measured only in bandwidth, without even a glance at behavior. Effective detection depends on measuring fidelity, not just flow.
DDoS Prevention and Mitigation
Prevention requires more than volumetric filtering or traffic offloading. A meaningful defense must anticipate how adversaries exploit architecture, tooling, and operational gaps. Effective mitigation depends on layered controls that adapt in real time and absorb impact gracefully, controls that minimize the operational surface vulnerable to overload.
Architectural Hardening
Designing for resilience starts with understanding where systems fail under pressure. Statelessness, elasticity, and minimal coupling all reduce DDoS exposure at the application layer.
Avoid deploying stateful services behind public endpoints without caching or request validation. Place reverse proxies or API gateways in front of origin applications to enforce schema checks, concurrency limits, and header normalization. Normalize request patterns early and drop malformed or suspicious payloads before allocating compute.
Use autoscaling groups to handle load increases but always apply upper thresholds to prevent cost exhaustion. For backend databases or critical systems, introduce buffering or asynchronous queues to decouple response time from request rate.
Reject reliance on static IPs. Use DNS with short TTLs and rotate addresses under duress. Maintain regionally redundant infrastructure but avoid automatic failover to identical configurations, which can replicate the bottleneck.
Network and Protocol Controls
At the network layer, block known reflection vectors. Disable or restrict protocols such as NTP, SSDP, or Memcached from responding to unsolicited public queries. Apply ingress filtering at the provider edge to prevent outbound amplification abuse if hosting any publicly accessible services.
Employ source validation with BCP 38 compliance wherever possible. Enforce strict packet inspection on edge firewalls and intrusion prevention systems. Drop traffic with spoofed headers, malformed TCP flags, or excessive fragmentation.
Rate limiting remains essential, but not in isolation. Apply token bucket or leaky bucket algorithms with endpoint-aware policies. Tune thresholds based on behavioral baselines, and separate rate policies for authenticated versus anonymous users.
Use Transport Layer Security (TLS) session caching and offload negotiation to hardened edge nodes. Where possible, enable HTTP/2 mitigation options to restrict stream resets and protect against Rapid Reset variants.
Deploy scrubber services capable of inline or rerouted mitigation. Ensure failover between scrubbing centers is automatic, not ticket-based. When using CDN or WAF vendors, confirm coverage includes all layers (Layer 3 to Layer 7) and doesn’t rely on signature matching alone.
Access and Identity Boundaries
IAM configurations directly affect how DDoS amplifies operational risk. Prevent attackers from escalating a performance issue into a security incident by restricting sensitive APIs, management planes, and escalated roles behind conditional access.
Segment environments based on trust and criticality. Avoid placing control interfaces or telemetry collection on public IPs. Require just-in-time access for administrative sessions, with enforced MFA and session auditing.
Don’t allow elevated identity roles to bypass rate limits or firewall policies. Avoid hardcoding service-to-service allowlists that can’t adapt to active threats. In multicloud architectures, use federated identity with policy enforcement at the resource layer rather than relying solely on central brokers.
Human and Organizational Readiness
Many DDoS attacks succeed not because of technical gaps, but because teams respond in isolation or underprepared. Run tabletop exercises focused on service degradation. Ensure operations, security, and application owners know their roles when latency climbs.
Provide operational staff with dashboards that show request anomalies, cache hit ratios, and backend saturation. Train engineering teams to interpret high RPS events alongside business context, such as time of day and user region.
Avoid blanket mitigations that block entire geographies or user agents unless business risk clearly warrants it. Misconfigured defenses often create more downtime than the attack.
Ineffective or Overstated Defenses
Several approaches often give a false sense of protection:
- Blacklisting IPs: Attackers rotate sources using proxy networks, VPNs, or botnets with near-infinite supply. Static deny lists become obsolete within seconds.
- Relying on cloud scale alone: Auto-scaling without rate enforcement or budget caps can trigger resource exhaustion at the billing layer, in addition to the compute layer.
- Web application firewalls (WAFs) with default policies: Without tuning, WAFs miss behavioral attacks or produce false positives that impact legitimate users.
- Relying solely on traffic volume metrics: Many modern attacks operate below alert thresholds by targeting expensive code paths or API queries with precision rather than noise.
DDoS resilience isn’t a product of any one control. It’s a reflection of system design, operational discipline, and the ability to prioritize signal over throughput under pressure.
DDoS Response and Recovery
DDoS response must happen in parallel across operational, technical, and communication layers. Delays or siloed reactions can worsen impact. A well-prepared organization coordinates teams around predefined thresholds and clear recovery criteria.
Immediate Containment and Traffic Control
Initiate mitigation using predefined playbooks tailored to the attack type and affected service. Route traffic through a cloud-based scrubbing provider or activate on-premises DDoS mitigation appliances. Where supported, trigger CDN or WAF rate-limiting policies to throttle anomalous behavior at the edge.
Block reflection vectors by disabling open services such as DNS recursion, NTP, or SSDP if they’re being abused. For application-layer attacks, isolate dynamic endpoints from static content and reduce concurrency limits to protect backend services from saturation.
Don’t disable security controls in an attempt to preserve performance. Attackers often escalate payloads after observing relaxed defenses.
In highly elastic environments, cap auto-scaling to prevent cost exhaustion. When serverless functions or container workloads experience traffic spikes, define concurrency ceilings and configure graceful rejection paths to maintain API health under load.
Cross-Functional Coordination
Response should extend beyond network operations. Engage the following functions:
- Security operations (SOC): Correlate with ongoing intrusion attempts or campaign patterns. Determine whether the DDoS serves as a diversion for deeper compromise.
- Application engineering: Identify high-cost endpoints, assess whether any misconfigurations contribute to resource amplification, and recommend defensive code changes.
- Site reliability or infrastructure teams: Manage routing changes, traffic shedding, and controlled failover between regions. Validate DNS propagation and rollback readiness.
- Communications and legal: Notify customers, partners, and regulators as required. Ensure messaging is accurate, actionable, and avoids speculative attributions.
Document all mitigation actions in real time. Preserve packet captures, server metrics, and application logs for forensic review. Maintain a timeline of changes across services, including configuration adjustments, code deployments, and incident communication.
Recovery and Postmortem Review
Recovery doesn’t begin when the traffic stops. It starts when controls are back to baseline and telemetry is fully restored. Resume service in phases, validating session state, cache synchronization, and backend availability before reintroducing full public access.
Conduct a full postmortem within 72 hours. Focus on:
- Control gaps: Did traffic bypass filters? Were rate limits too permissive or misaligned with behavior?
- Visibility breakdowns: Were metrics delayed or misinterpreted? Did telemetry coverage extend across all layers?
- Response speed: Where were delays introduced? Were escalation paths clear and followed?
- Customer impact: Did clients experience degraded availability, timeout errors, or service lockouts? Quantify both scope and duration.
Extract signatures or behavioral patterns from the attack. Use these to update detection logic, rate thresholds, and scrubber profiles. Where application logic contributed to amplification, plan engineering work to reduce complexity or exposure.
Hardening for Future Events
Update service diagrams to reflect actual attack paths and mitigation efficacy. Tune playbooks for specific vectors such as HTTP floods, TCP SYN floods, or HTTP/2 resets. Integrate synthetic testing to benchmark DDoS readiness across regions, endpoints, and providers.
Validate vendor SLAs and service tier eligibility. Ensure security partners can scale to current throughput levels. Confirm that load testing includes not just expected usage, but attack-like patterns targeting edge, cache, and origin.
DDoS response is a reflection of how well teams coordinate under pressure, how infrastructure absorbs imbalance, and how quickly control is reestablished under adversarial conditions.
