- 1. How do virtual firewalls work?
- 2. What makes a virtual firewall distinct?
- 3. Why use virtual firewalls?
- 4. Where are virtual firewalls deployed?
- 5. How do virtual firewalls compare to other firewall models?
- 6. How virtual firewalls uniquely support Zero Trust
- 7. What to look for in a virtual firewall
- 8. Virtual firewall FAQs
- How do virtual firewalls work?
- What makes a virtual firewall distinct?
- Why use virtual firewalls?
- Where are virtual firewalls deployed?
- How do virtual firewalls compare to other firewall models?
- How virtual firewalls uniquely support Zero Trust
- What to look for in a virtual firewall
- Virtual firewall FAQs
What Is a Virtual Firewall? How It Works + When to Use One
- How do virtual firewalls work?
- What makes a virtual firewall distinct?
- Why use virtual firewalls?
- Where are virtual firewalls deployed?
- How do virtual firewalls compare to other firewall models?
- How virtual firewalls uniquely support Zero Trust
- What to look for in a virtual firewall
- Virtual firewall FAQs
A virtual firewall is a type of software firewall delivered as a virtual machine or cloud instance.
It runs on hypervisors or cloud compute platforms and inspects both north–south and east–west traffic. Because it's software-based, it can scale with workloads and integrate with cloud automation tools for consistent policy across environments.
Virtual firewalls apply the same inspection and policy enforcement functions as a next-generation firewall.
How do virtual firewalls work?
A virtual firewall performs the same functions as a hardware firewall.
It inspects packets, compares them to policy, and allows or blocks connections. It can track session state, apply application-level rules, decrypt traffic, and log events for monitoring.
The difference is in how and where it runs.
A virtual firewall is delivered as a virtual machine image or cloud instance. It sits inline on a hypervisor switch or cloud gateway so all traffic between workloads or to and from the internet passes through it.
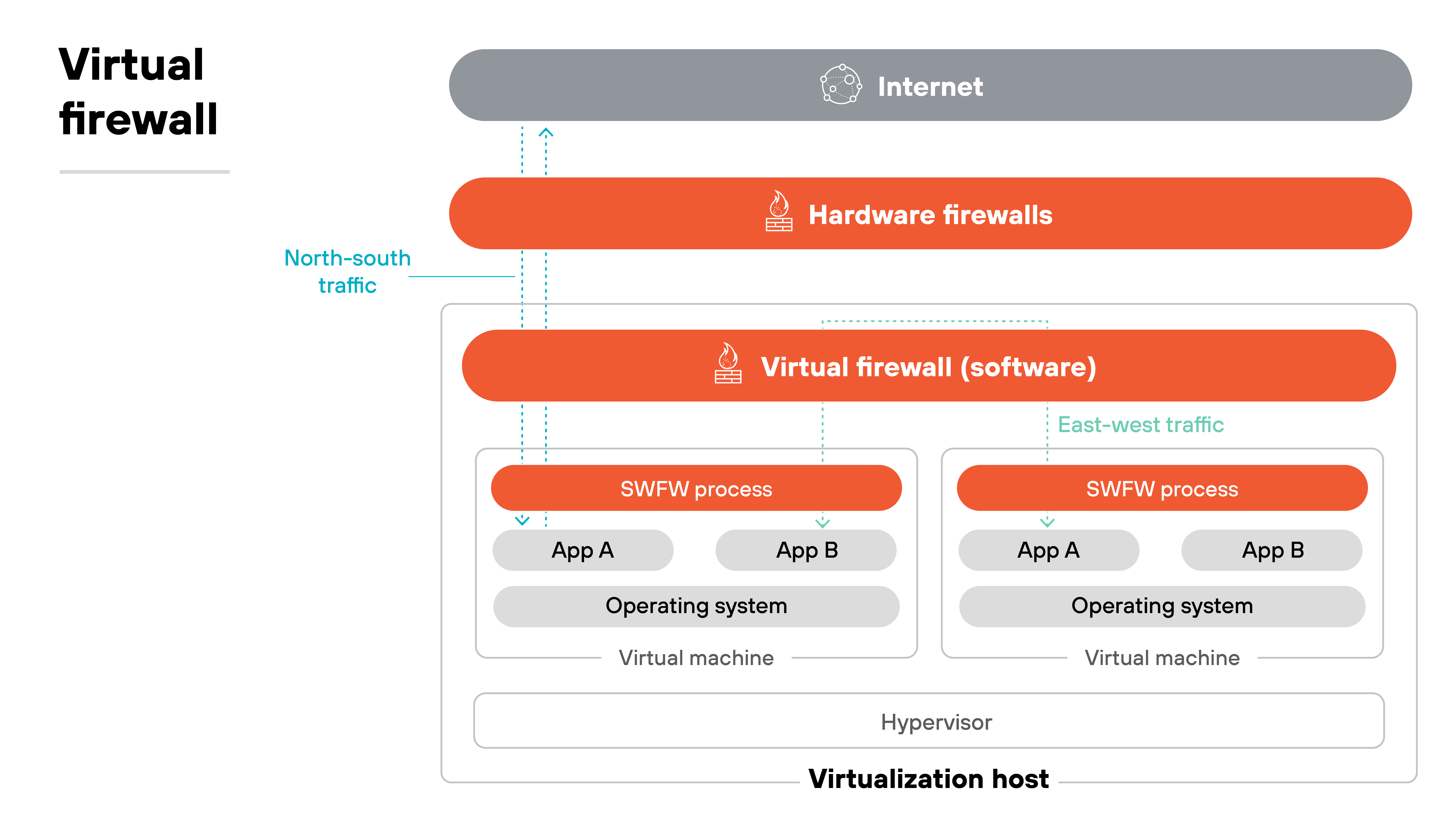
This position lets it secure both north–south traffic entering or leaving a virtual environment and east–west traffic flowing between workloads. That coverage goes beyond what many cloud-native controls provide.
Virtual firewalls are also elastic.
To accommodate traffic demands, they can be scaled up by allocating more vCPUs or scaled out by deploying more instances. Policies remain consistent because management happens centrally, while enforcement occurs at each instance close to the workload.
Integration with cloud tags, labels, and APIs is another difference.
Policies can adapt dynamically as workloads are created or destroyed, which allows security to keep pace with highly dynamic environments.
In short, virtual firewalls work like hardware devices but operate as flexible, scalable instances inside virtualized and cloud networks.
What makes a virtual firewall distinct?
A virtual firewall is different from a hardware appliance because of its form factor.
It runs as a VM or cloud instance instead of a dedicated device. Which means it can sit closer to workloads inside a virtualized network rather than only at a fixed perimeter.
This proximity changes how policies are applied.
Instead of securing only traffic that crosses into or out of a site, a virtual firewall can segment workloads and applications within the environment itself. That makes it useful for controlling east–west flows that a perimeter device would never see.
Another distinction is elasticity.
A hardware firewall is tied to the performance of its chassis. A virtual firewall can scale up by adding vCPUs or scale out by deploying new instances. Policies stay consistent, but capacity matches demand. For organizations running dynamic workloads, that flexibility is a practical advantage.
Automation also plays a role.
Virtual firewalls integrate with orchestration tools and cloud APIs. Which means policies can be updated automatically as resources change. This reduces manual work and keeps enforcement aligned with the pace of deployment.
Why use virtual firewalls?
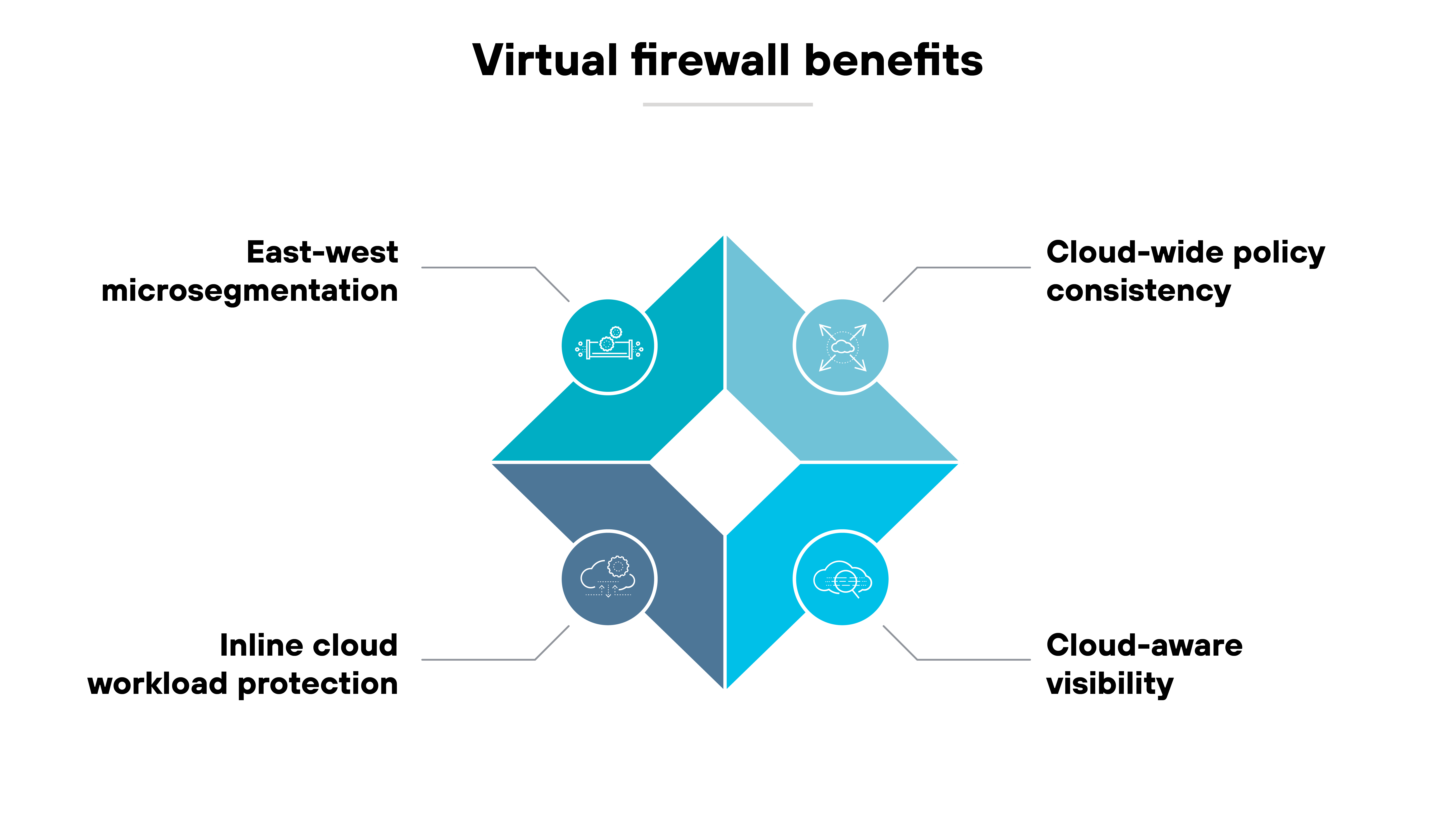
All firewalls inspect traffic and enforce policies. What sets virtual firewalls apart is how they deliver those same functions inside cloud and virtual environments.
Their software form factor allows them to sit close to workloads, scale with demand, and integrate with cloud-native tools. These capabilities translate into distinct benefits that address the challenges of securing dynamic, distributed infrastructure.
Cloud-wide policy consistency
Virtual firewalls apply the same security rules across public clouds, private clouds, and on-premises environments. Because they integrate with cloud APIs, tags, and labels, policies can follow workloads as they scale or migrate. That's different from cloud-native security groups, which are limited to one platform.
East–west microsegmentation
A virtual firewall can control traffic inside virtualized networks, not just at the edge. It enforces policies between VMs, subnets, or VPCs, creating boundaries that hardware firewalls cannot reach. This limits lateral movement in cloud and data center environments.
Inline cloud workload protection
Virtual firewalls sit in the path of internet-facing applications hosted in a VPC or VNet. They block malicious inbound requests before they hit the workload. They also monitor outbound traffic, stopping exfiltration attempts or preventing connections to untrusted code sources.
Cloud-aware visibility
Logs and reports from virtual firewalls include cloud metadata, such as tags and resource identifiers. This context makes it possible to see not just IPs or ports, but which workload or application is involved. That added visibility is key in dynamic environments where resources are constantly changing.
Where are virtual firewalls deployed?
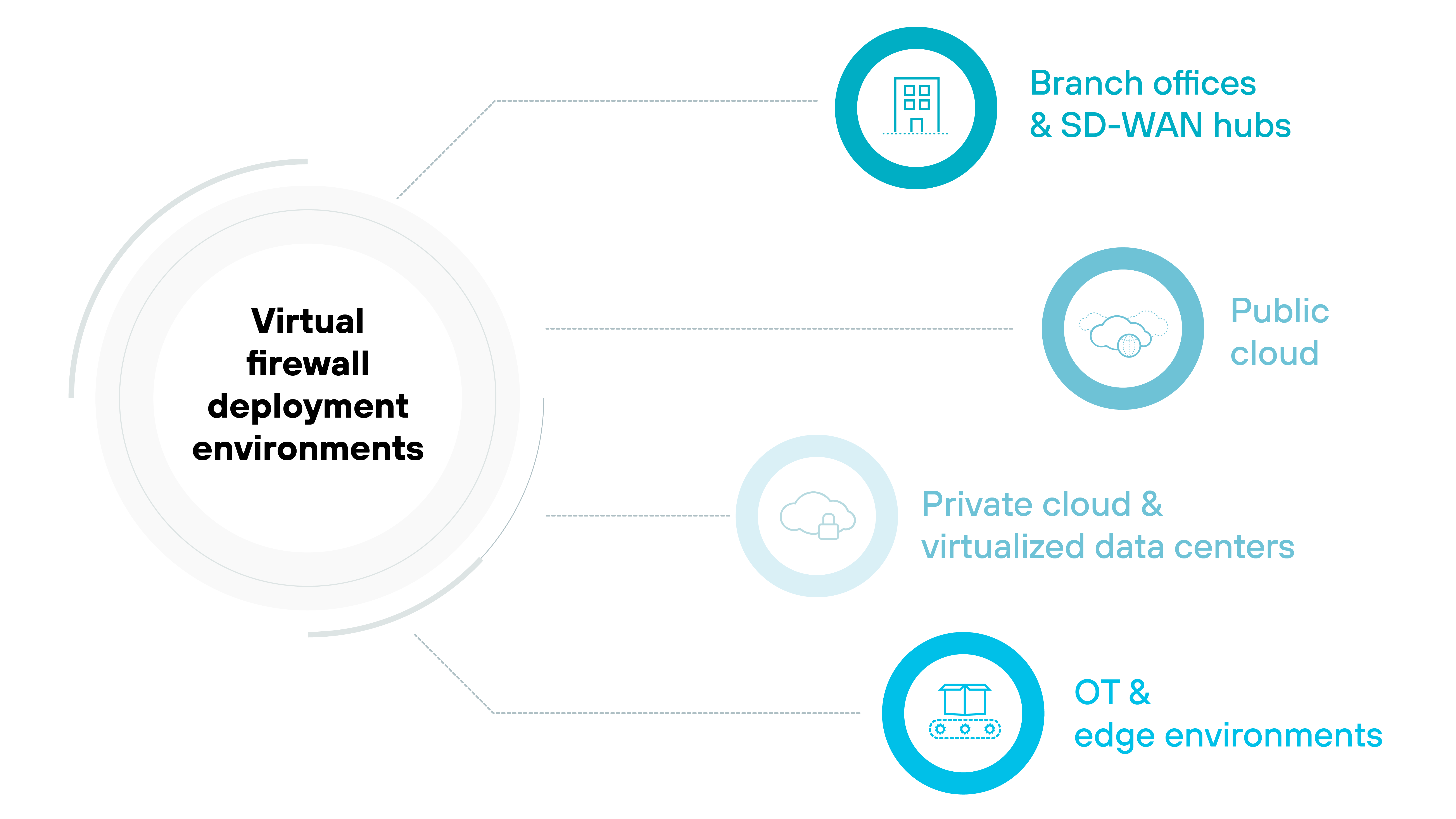
Virtual firewalls can be deployed in multiple environments where physical appliances are not practical, including:
- Public cloud
- Private cloud and virtualized data centers
- Branch offices and SD-WAN hubs
- OT and edge environments
Their role is to extend firewall controls into cloud, virtualized, and distributed networks so security follows the workloads.
Public cloud
Virtual firewalls are often placed inside public cloud environments.
They can be inserted into VPCs or VNets as gateways or as part of a hub-and-spoke design. This lets them inspect north–south traffic entering workloads and east–west traffic between applications.
In transit gateway patterns, they can also serve as a central inspection point before traffic moves between regions or to the internet.
Private cloud and virtualized data centers
In private clouds, workloads run on hypervisors and virtual networks. A virtual firewall can be deployed between segments or VLANs to enforce security policies.
For example, it can separate a finance application from a development environment. It can also create microsegmentation zones that restrict traffic even within the same data center.
These controls reduce the risk of lateral movement in highly connected environments.
Branch offices and SD-WAN hubs
Branches often lack space for full appliances. In these cases, a virtual firewall can run on universal CPE or existing x86 servers. It provides segmentation and threat prevention without requiring dedicated hardware.
In SD-WAN architectures, virtual firewalls can be used as hub or spoke devices to secure branch-to-cloud or branch-to-branch traffic. This extends policy enforcement beyond the data center into distributed sites.
OT and edge environments
Some operational technology and edge deployments also use virtual firewalls.
When a virtualized platform is already present, a firewall VM can provide inspection without adding new hardware. This is useful in scenarios where physical space or environmental requirements make appliances impractical.
How do virtual firewalls compare to other firewall models?
The distinction between virtual firewalls and other firewall models comes down to how they are delivered and where they fit.
| Virtual firewalls vs. other software firewall models |
|---|
| Parameter | Virtual firewall | Hardware firewall | Container firewall | Managed firewall service |
|---|---|---|---|---|
| Form factors | Runs as a VM or cloud instance on a hypervisor | Physical appliance with dedicated CPU, memory, and interfaces | Runs inside container platforms such as Kubernetes | Software firewall instances hosted and operated by a provider |
| Installation & operation | Deployed on virtual machines or cloud compute; managed centrally with local enforcement | Installed between network devices; requires physical setup and lifecycle management | Integrated at the orchestration layer; configured through container APIs | Provider deploys and maintains; customer defines policies |
| Deployment options | Public and private clouds, virtual data centers, branch offices, SD-WAN hubs | Data center or campus edge, industrial sites | Microservices and containerized applications | Provider's infrastructure, delivered as a managed service |
| Complexity | Requires cloud networking integration and capacity planning | Higher due to physical hardware, refresh cycles, and skilled staff | Narrow scope but complexity tied to dynamic container environments | Lower for the customer; less direct control over operations |
Essentially:
- A hardware firewall is a physical appliance. It anchors the edge of a network and provides predictable performance through dedicated resources.
- A virtual firewall is delivered as a VM or cloud instance. It runs on shared infrastructure and can be scaled up or down as workloads change.
- Container firewalls take a different approach. They are designed specifically for microservices and integrate with orchestration platforms like Kubernetes. Their scope is narrow, but they adapt quickly to short-lived workloads.
- Managed firewall services shift responsibility to a provider. The software is hosted and maintained externally, while the customer defines and applies policies. This reduces operational burden but also means less direct control.
Each firewall model addresses a different need. Together, they provide complementary options that can be combined as part of a broader network security strategy.
- What Is a Hardware Firewall? Definition & Explanation
- Hardware Firewalls vs. Software Firewalls
- What Is a Container Firewall? How It Works + When to Use One
How virtual firewalls uniquely support Zero Trust
Virtual firewalls bring Zero Trust principles into cloud and virtual environments by enforcing policy where workloads actually run.
Unlike perimeter devices, they can be deployed inline on hypervisors, VPCs, or VNets. This placement allows enforcement points to exist throughout the environment, not just at the edge.
One way this supports Zero Trust is through distributed control.
Each virtual firewall instance checks traffic between workloads or tiers. That makes it possible to verify every request and restrict access to the minimum required, which aligns directly with least privilege access.
Microsegmentation is another fit.
Virtual firewalls can create boundaries between VMs, subnets, or virtual private clouds. These divisions help ensure that a compromise in one part of the environment does not automatically spread to another.
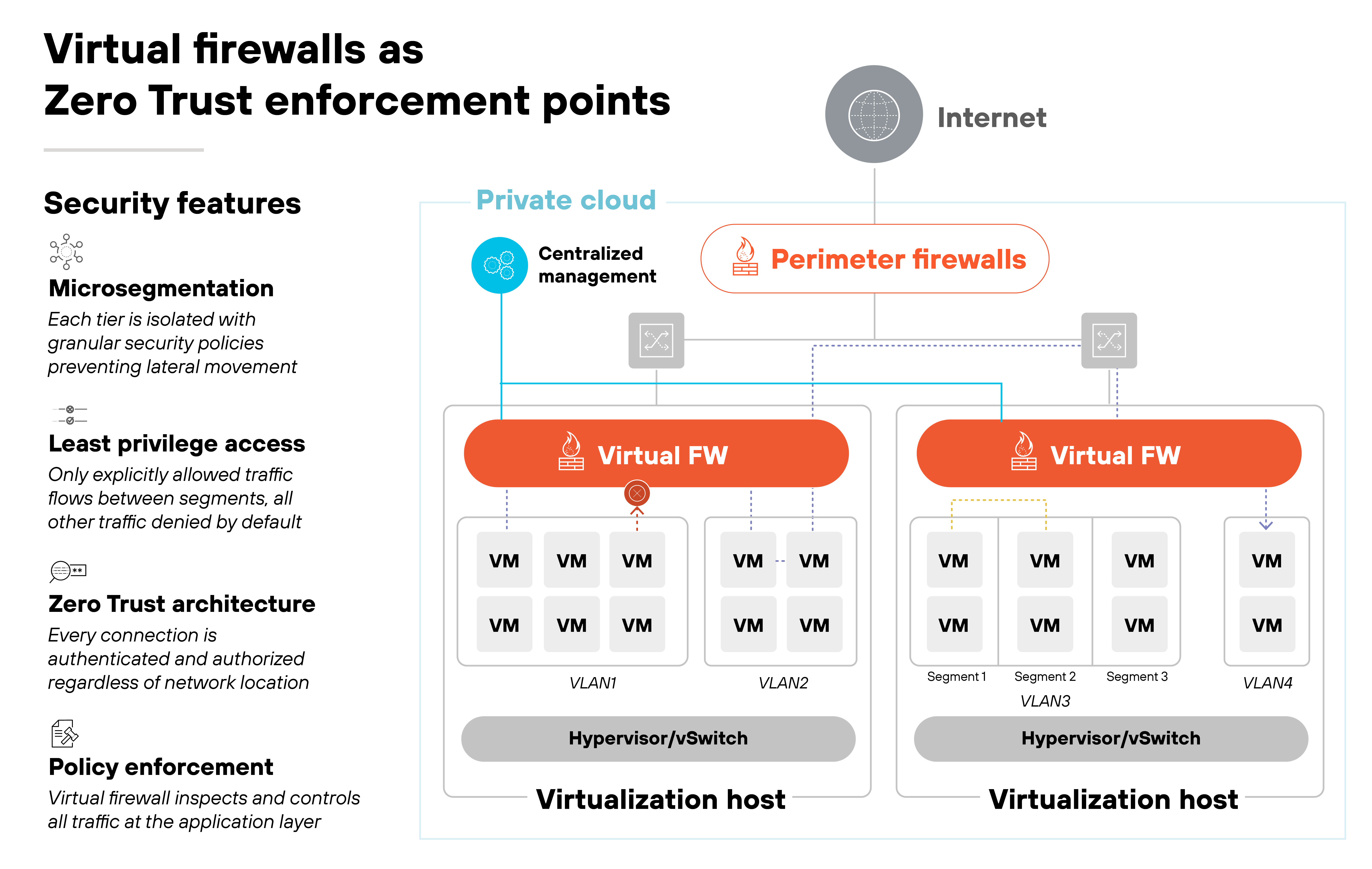
They also support dynamic policy.
Rules can be tied to cloud attributes such as tags or resource identifiers rather than static IP addresses. As resources scale up or down, policies follow automatically. This keeps enforcement continuous even in highly elastic environments.
In short, virtual firewalls make Zero Trust practical in places where traditional appliances cannot reach. They distribute enforcement close to workloads, provide segmentation across virtual networks, and apply policies that adapt as environments change.
What to look for in a virtual firewall
Choosing a virtual firewall means looking beyond the basic form factor.
Since the core inspection functions are the same across models, the difference comes down to which features make the firewall effective in dynamic cloud and virtual environments.
Here are the qualities to prioritize:
Application-aware protections
A virtual firewall should provide the same advanced protections as a next-generation appliance.
As mentioned, that includes Layer 7 inspection, intrusion prevention, SSL/TLS decryption, URL filtering, and DNS security. These capabilities ensure threats are blocked even when they hide in application traffic.
Integration with cloud automation
Look for integration with cloud tags, labels, and orchestration tools.
Virtual firewalls that support APIs and automation platforms like Terraform or Ansible can adapt policies as workloads change. This reduces manual effort and keeps security aligned with dynamic environments.
Centralized management and visibility
Management should extend across multiple clouds and on-premises environments. A central console allows policies to be defined once and enforced everywhere.
Logging and telemetry should also integrate with monitoring systems to give teams full visibility into applications, users, and traffic flows.
High availability and scale
Virtual firewalls should support cloud-native availability patterns. That includes integration with load balancers, autoscaling groups, and failover mechanisms.
These features help ensure continuous enforcement even when demand spikes or an instance fails.
Clear performance guidance
Performance depends on the underlying instance type.
Vendors should provide sizing guidance so security teams can match vCPUs, memory, and throughput to their traffic mix. This avoids under-provisioning or unnecessary overspending.
