- What Is Security Architecture?
- What is a Security Threat Assessment?
-
What is an IT Security Policy?
- What is Cybersecurity Transformation?
- Reducing Cybersecurity Risk at the Board Level
-
What Is a Distributed Enterprises and Why Does Cybersecurity Matter for Branch Offices?
-
How to Get the Most Value Out of Security Investments
What is Cybersecurity Consolidation?
Cybersecurity consolidation is the process of modernizing cybersecurity architectures to reduce the number of tools and vendors, eliminate silos, unify threat prevention and response, and shift to an integrated security approach that strengthens risk posture.
With cybersecurity consolidation, security platforms protect organizations on all attack surfaces—network, cloud, IoT, endpoints, SD-WAN, and more—while sharing the same technologies and intelligence. The result is a security infrastructure that’s unified, easier to manage, less costly, and future-proofed.
Why is Cybersecurity Consolidation Important?
Cyber threats are rapidly evolving, with 96% of business leaders experiencing a breach in 2022 and 57% of those experiencing three or more. And as threat actors increasingly leverage artificial intelligence (AI) to launch sophisticated cyberattacks, organizations have a new generation of threats to defend against.
At the same time, IT environments are more complex and borderless than ever before, with many enterprises now employing multi-cloud strategies and multiple-point products. This makes traditional risk management defenses ineffective, and leaves organizations open to attacks.
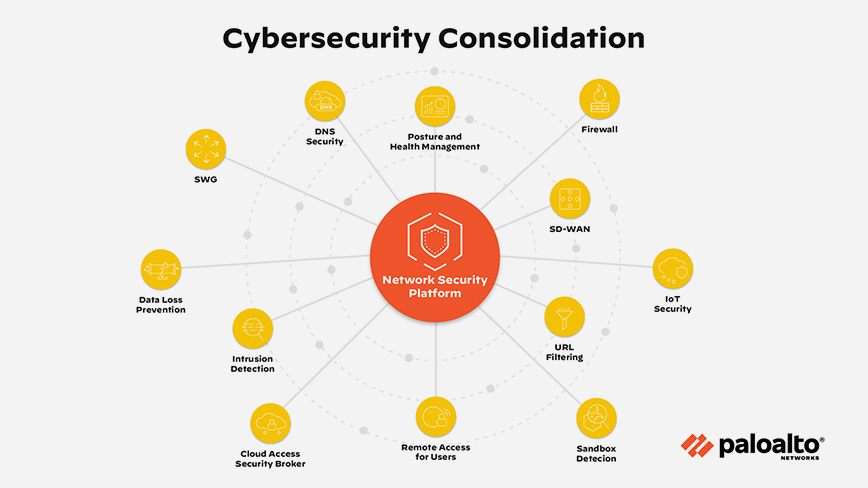
Cybersecurity consolidation strengthens risk management by protecting all attack surfaces using consolidated security platforms. Cybersecurity consolidation offers critical security features and services—firewall, DNS security, intrusion detection, SD-WAN—all in one platform, where those tools use shared intelligence to prevent zero-day attacks.
It enables security teams to maximize their use of key technologies such as automation, machine learning and artificial intelligence (AI) to accelerate response times and reduce IT complexity.
What Are the Benefits of Cybersecurity Consolidation?
Cybersecurity consolidation enhances risk posture by collectively sharing intelligence to prevent zero-day threats in real time. Tools share data points, dashboards and user experiences, providing security teams with a complete picture of their risk posture and an opportunity to centralize cyber threat detection and response.
Cybersecurity consolidation also reduces the number of individual security tools and services deployed in a single architecture. Today’s enterprises employ 31.5 security tools on average—each having its own procurement, implementation, and upkeep requirements. But with a consolidated architecture, those tools and services are merged into a few platforms that are simple to manage.
When every part of the cybersecurity stack works together in a simpler, more unified structure, organizations are fully prepared to handle the latest cyber threats.
Key Benefits of a Consolidated Cybersecurity Architecture
- Faster threat detection and response through automation, machine learning and artificial intelligence.
- Reduced time to respond to incidents via centralized cyber threat detection and response.
- Reduced risk of security gaps caused by siloed solutions and human errors.
- Improved productivity and morale for overworked and over-extended SOC and cybersecurity teams, resulting in reduced turnover.
- Reduced time to update security policies, implement patches consistently across all environments and complete threat analyses.
- Improved user experience, with a more direct path to Zero Trust architectures.
- Faster speed to market by empowering DevSecOps and a “shift left” security posture that enhances innovation.
Why is Cybersecurity Consolidation a Priority in 2023?
2023 is a mission-critical period in cybersecurity. Multi-cloud architectures are now the rule, not the exception, requiring more centralized control and enterprise-wide visibility. At the same time, hybrid work is the new workplace reality, with employees who log in from anywhere and everywhere.
SIEM, IAM, threat intelligence, Zero Trust and other aspects of a modern cybersecurity system must be tightly integrated in order to deliver the benefits of security infrastructure optimization and enterprise-wide risk management.
At the same time, threat actors are better funded and more sophisticated in their use of automation, machine learning and artificial intelligence. With intelligent tools, adversaries create more effective phishing emails and deep fakes, using automation to make their attacks more potent and massive in scale.
Hybrid work and the Internet of Things (IoT) have increased the attack surface, and adversaries are using intelligent technologies to ramp up attacks in these areas. For example, 84% of cybersecurity decision-makers have seen more incidents due to hybrid work over the past 12 months.
What Are the Challenges of Implementing Cybersecurity Consolidation?
Cybersecurity consolidation is a marathon—not a sprint. Organizations will face several key challenges when adopting cybersecurity platforms. Here are a few:
Integration Issues
Integration remains a key concern when procuring new cybersecurity solutions. Organizations entrenched in existing workflows have to determine whether a consolidated platform will integrate with their current architecture. It’s often not a simple “rip and replace” when implementing new solutions, and will require a cybersecurity provider that works hand-in-hand with the security team to determine if consolidation is the right answer.
Vendor Lock-In
Many security tools use proprietary technologies designed to solve specific problems—without providing an easy path to integration. At the same time, many organizations often have significant, long-term investments and training with particular vendors and technologies.
Organizations must look at their current investments and determine whether a consolidated security platform makes sense from a financial and operational perspective.
Resistance to Change
Switching security solutions is a tough decision for enterprises. How do you know your next solution will be an improvement? Will a single platform model meet all of your IT and business needs? And how will end users adapt to the new tools and services?
Deploying new cybersecurity tools will require a concerted effort across the entire organization to ensure the tools are properly deployed, effectively managed and understood by every end user.
Consolidated Platform vs. Best of Breed
Cybersecurity technology typically falls into two camps: best of breed or platform. The best-of-breed approach means organizations choose security tools as needed by the business. The platform approach means organizations get an entire suite of security tools that provide end-to-end security.
Both approaches have their advantages and disadvantages. Let’s take a look:
Pros of Consolidated Platforms
- Consolidated security architecture to reduce the number of point solutions
- Single vendor, single console for endpoint protection solutions, SEIM, IAM, cyber threat detection and response
- Centralized visibility to simplify risk management, security compliance, vulnerability management and cybersecurity transformation
- Simpler, more straightforward path to Zero Trust
- Future-proofed security architecture
Cons of Consolidated Platforms
- Possibility of missing potential innovations
- Potential challenges of moving to new vendors and costs involved in migration, training, learning new tools and failing to maximize existing investments.
Pros of Best-of Breed-solutions
- Using the best technology for each point solution
- Using different vendors provides extra flexibility
- Ability to take advantage of new technology and product innovations as they come to market, without waiting for your platform vendor to develop it
- Flexibility to leverage existing investments and training
Cons of Best-of Breed-solutions
- Lack of integration and interoperability increases cyber risk
- Vendor lock-in for key products and solutions, such as SIEM or IAM
- More complexity in managing governance and compliance
- Makes budgeting more difficult and less predictable
- Doesn’t adequately address the problem of too many vendors and tools