- 1. What is the Internet of Medical Things (IoMT)?
- 2. Why is IoMT security important?
- 3. What are some examples of IoMT devices?
- 4. What are the primary IoMT security risks and challenges?
- 5. What are the most common IoMT attack methods?
- 6. How does IoMT security work?
- 7. How does IoMT security fit into a broader healthcare cybersecurity strategy?
- 8. What frameworks, standards, and regulations guide IoMT security?
- 9. IoMT security FAQs
- What is the Internet of Medical Things (IoMT)?
- Why is IoMT security important?
- What are some examples of IoMT devices?
- What are the primary IoMT security risks and challenges?
- What are the most common IoMT attack methods?
- How does IoMT security work?
- How does IoMT security fit into a broader healthcare cybersecurity strategy?
- What frameworks, standards, and regulations guide IoMT security?
- IoMT security FAQs
What Is Internet of Medical Things (IoMT) Security? Overview
- What is the Internet of Medical Things (IoMT)?
- Why is IoMT security important?
- What are some examples of IoMT devices?
- What are the primary IoMT security risks and challenges?
- What are the most common IoMT attack methods?
- How does IoMT security work?
- How does IoMT security fit into a broader healthcare cybersecurity strategy?
- What frameworks, standards, and regulations guide IoMT security?
- IoMT security FAQs
IoMT security is the practice of protecting connected medical devices and the data they exchange from unauthorized access, disruption, or misuse.
It focuses on safeguarding the systems that connect medical devices to clinical networks.
Sometimes referred to as medical IoT security, IoMT security ensures these devices function safely, remain available, and do not introduce risks to patient care or broader hospital infrastructure.
What is the Internet of Medical Things (IoMT)?
The Internet of Medical Things (IoMT) refers to connected medical devices that communicate with clinical networks to support patient care. These devices collect, transmit, or act on health data. Often in real time.
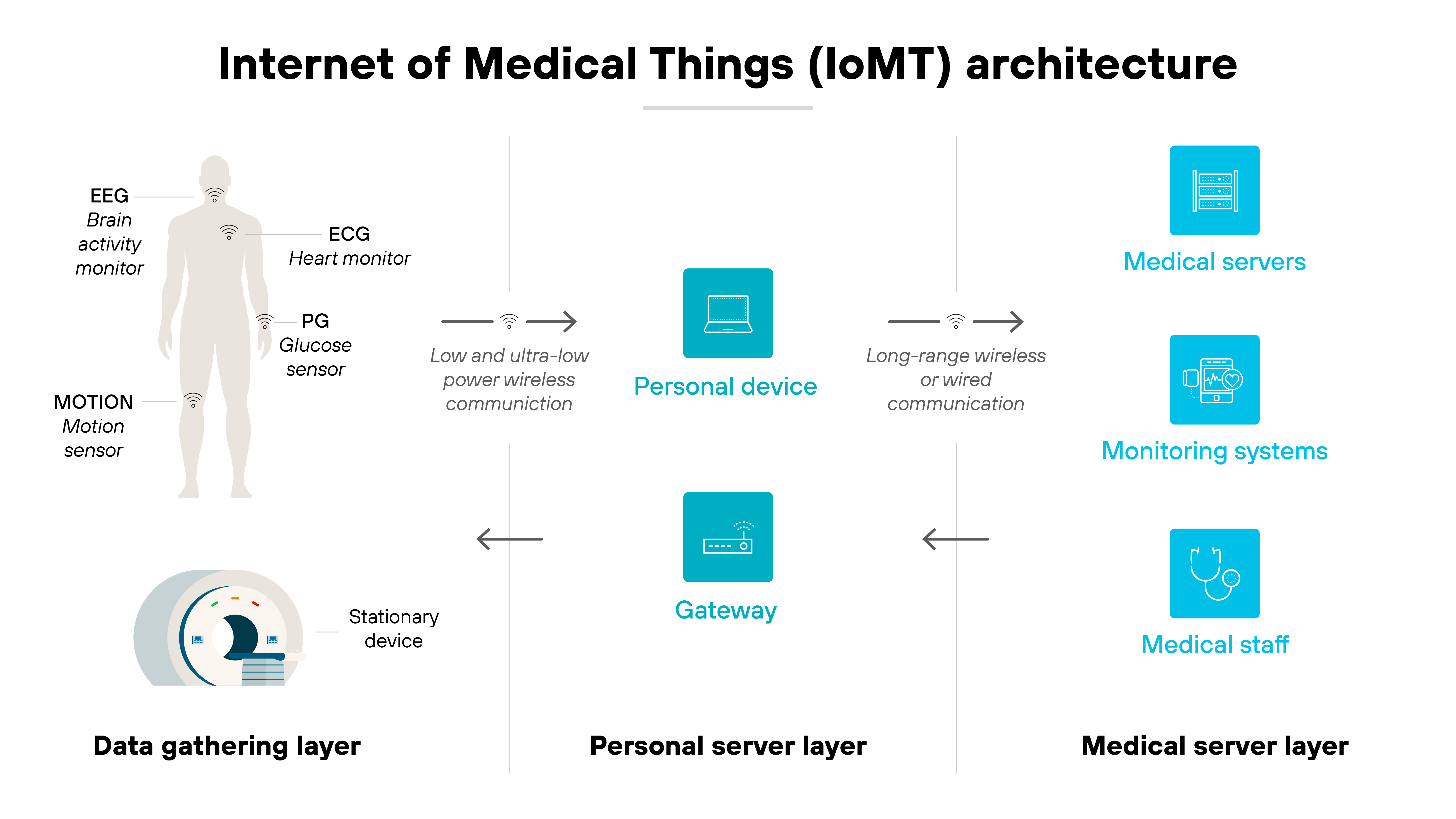
IoMT includes everything from wearable monitors and implantable sensors to imaging systems and infusion pumps.
Some operate independently. Others integrate with electronic health records, AI diagnostics, or cloud-based platforms.
Why is IoMT security important?
The rise of connected medical devices has introduced new risks to patient safety and healthcare delivery.
The global IoT in healthcare market is projected to reach $188 billion by 2028, up from 2020 levels.
The rapid proliferation of Internet of Medical Things (IoMT) technology is transformative, affecting medical professionals and patients alike.
IoMT systems often include legacy devices, underpowered sensors, and decentralized infrastructure. These limitations create significant vulnerabilities. Especially when devices operate in uncontrolled environments or exchange data over public networks.
Here's why that matters.
Medical data is highly sensitive. It's also a target. A breach doesn't just expose personal health information. It can impact treatment workflows or delay care altogether. And in critical cases, compromised device functionality could affect clinical outcomes.
As AI and machine learning become more common in diagnostics and monitoring, new security gaps are emerging. From training data integrity to model manipulation. Attackers can exploit these systems in subtle, high-impact ways that aren't always easy to detect.
IoMT security is important because healthcare environments can't rely on traditional IT defenses alone. They need tailored protections that account for real-world limitations like unpatchable firmware, multi-vendor ecosystems, and constrained bandwidth.
Without that, the growing complexity of connected care becomes a liability instead of an advantage.
What are some examples of IoMT devices?
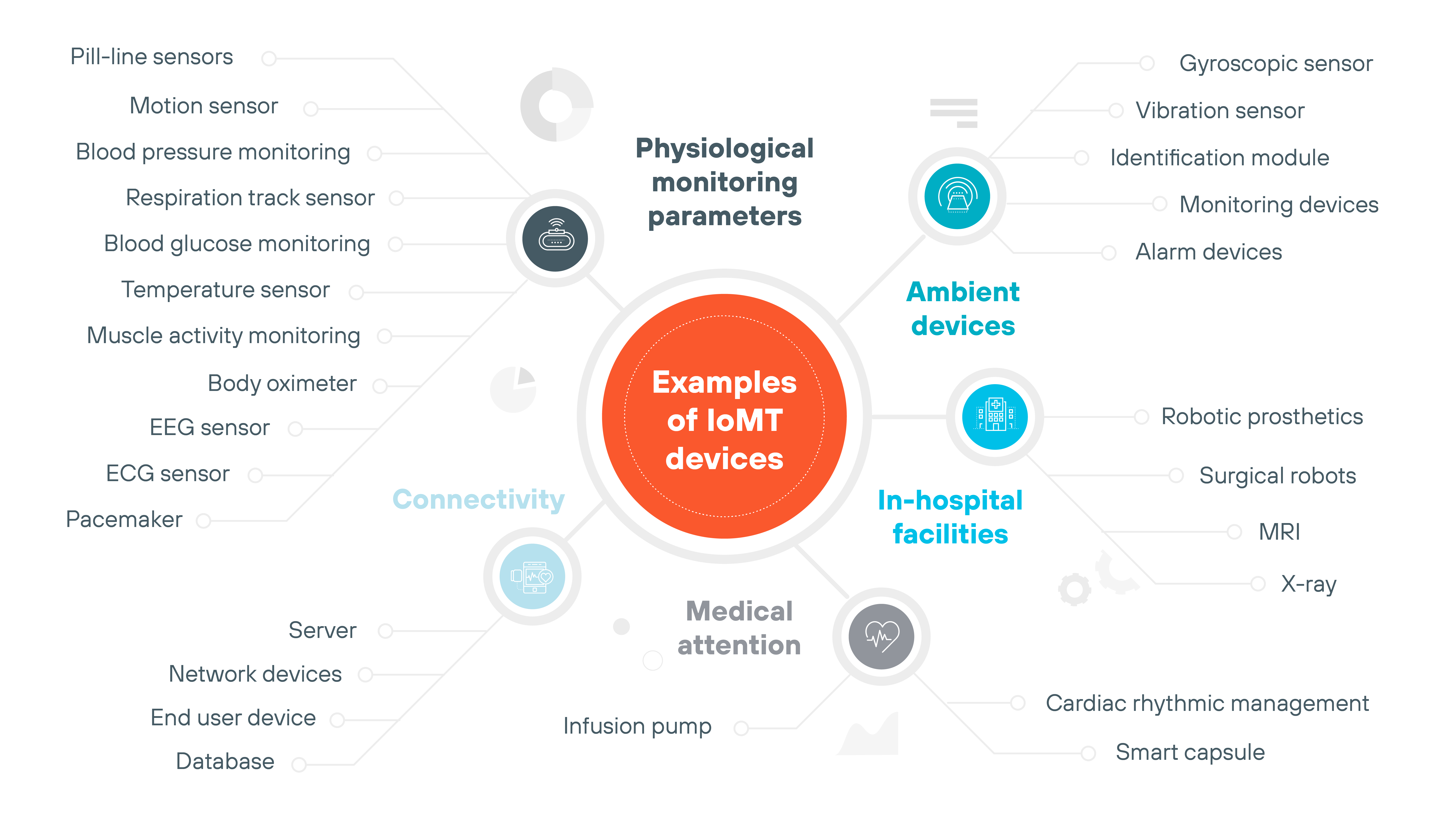
Connected medical devices come in many forms, ranging from wearable fitness trackers to surgical robotics.
Some operate outside the body. Others are embedded deep within it.
This section doesn't cover every type of device. Instead, it highlights a few representative examples to show how diverse the IoMT landscape is. And why security concerns can vary so widely depending on the function, location, and data flow of each one.
Wearables
Wearable devices like fitness bands and mobility trackers monitor physical activity, posture, gait, and vitals. They are especially common in elder care and chronic disease management.
Risks: These devices often integrate with public networks or consumer devices. That opens the door to unauthorized access or unintended exposure of location, behavior, or health status.
Infusion pumps
Infusion pumps are connected devices that deliver fluids, nutrients, or medication directly into a patient's body in controlled doses. They're widely used in hospitals and increasingly managed through remote interfaces.
Risks: If compromised, infusion pumps can be tampered with to adjust dosage levels or delivery schedules. Many run outdated software and operate inside flat networks, making them vulnerable to unauthorized access or lateral attacks.
Imaging systems
CT, MRI, and ultrasound machines connect to healthcare networks for diagnostics, archiving, and AI-supported analysis.
Risks: These devices often run legacy software and rely on static network configurations. If exploited, they can be used to exfiltrate patient data or pivot laterally across clinical systems.
Implantable sensors
Implantables include cardiac monitors, neurostimulators, and glucose sensors that collect internal signals and transmit them externally.
Risks: Because of their inaccessibility and power constraints, many implantables can't be patched or reconfigured easily. This creates long-term exposure if vulnerabilities are discovered post-deployment.
What are the primary IoMT security risks and challenges?
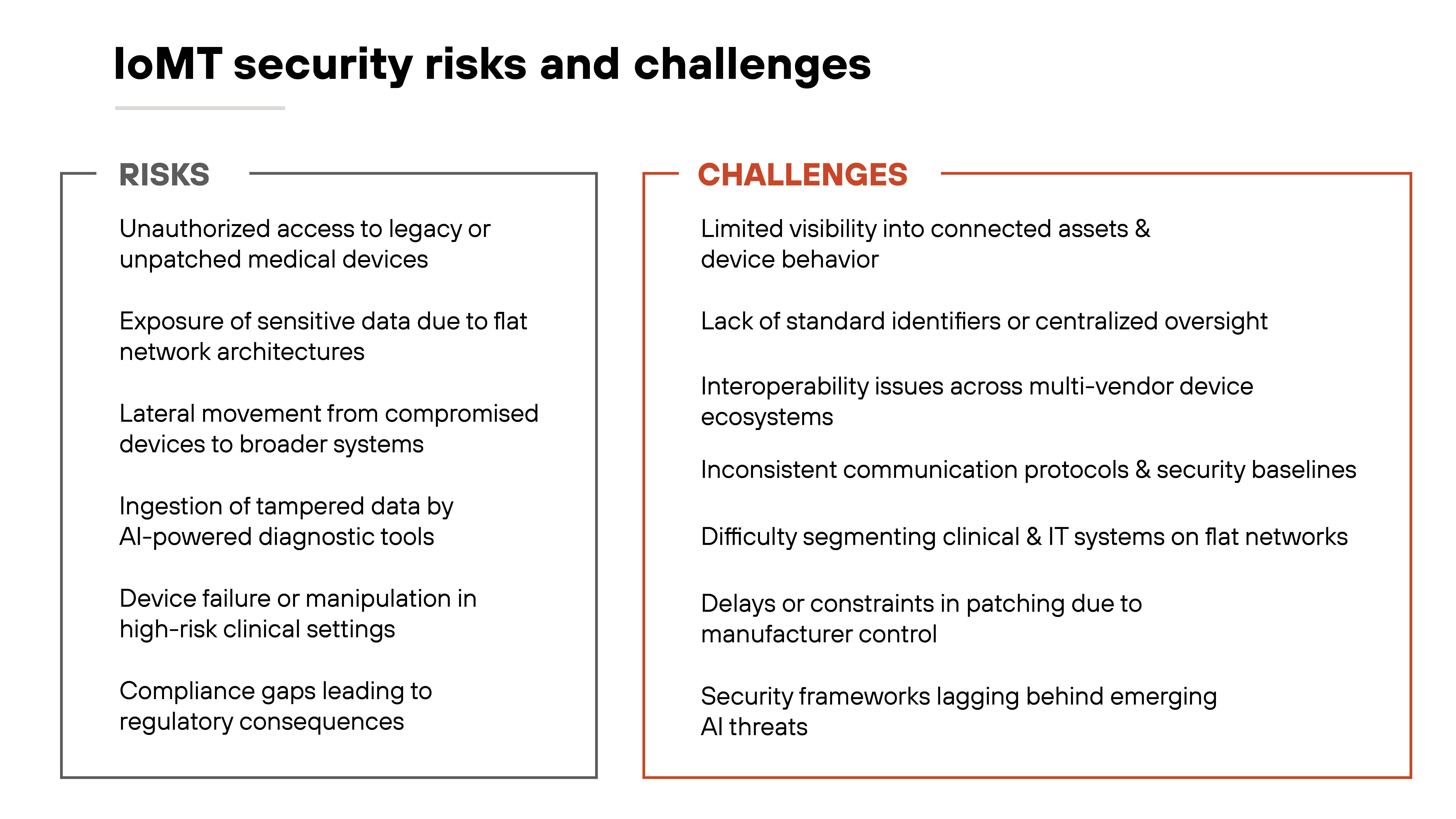
The rise of connected medical devices has expanded healthcare capabilities. But also created new exposure points.
IoMT devices are often deployed in high-risk environments with little room for failure. That makes security more complex than in traditional IT or even general IoT.
One major challenge is visibility. Many IoMT assets operate without centralized oversight. They may not show up in inventories, lack standard identifiers, or run on outdated software. Without full awareness of what's connected, healthcare providers can't assess risk or apply consistent policies.
Another issue is architecture. IoMT devices are frequently placed on flat networks, mingling clinical and IT systems without segmentation. That means a compromised imaging system or infusion pump can become a launchpad for broader attacks. The threat increases when these devices run legacy operating systems or can't be patched without manufacturer approval.
Interoperability and AI also complicate the picture. Devices come from many vendors and may not share communication protocols or security baselines. This inconsistency can obstruct integration and limit enforcement. Meanwhile, AI-enabled systems—especially those supporting diagnostics—can amplify the risks if they ingest tampered data from insecure sensors.
All of this plays out in a heavily regulated space. Compliance requirements may lag behind real-world threats.
And with sensitive data and patient safety on the line, even small gaps in protection can have outsized consequences.
What are the most common IoMT attack methods?
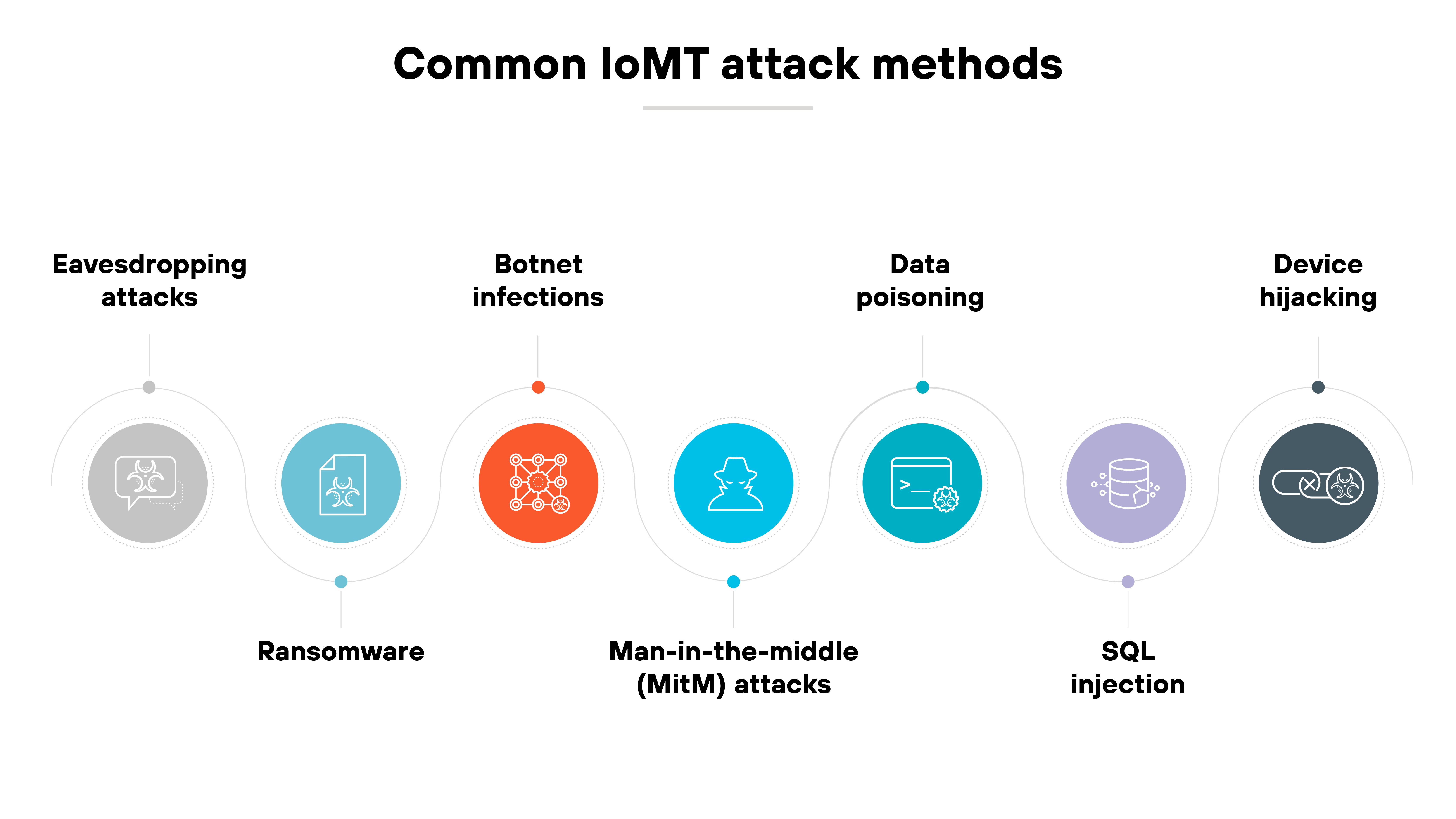
Cyberattacks targeting IoMT systems often exploit the same weak spots: wireless communications, legacy software, and a lack of authentication controls.
But the methods vary. Some go after data. Others try to take control. And many take advantage of the way AI and cloud tools now interact with medical devices.
Here are the most common attack methods you need to know about:
Eavesdropping attacks
These target unencrypted or poorly secured wireless transmissions—such as Bluetooth or Wi-Fi—between medical devices and monitoring systems. Attackers intercept sensitive data in transit, risking patient privacy and clinical integrity.
Ransomware
Once inside the network, ransomware can encrypt files from connected medical devices or lock critical systems like infusion pumps. That disrupts care and can force delays until systems are restored, or payments made.
Botnet infections
Many IoMT devices run outdated firmware. That makes them easy targets for botnet malware, which turns them into tools for large-scale attacks like DDoS campaigns or lateral movement.
Meddler-in-the-middle (MitM) attacks
MitM attacks intercept communications between devices and backend systems. They can be used to alter readings, manipulate commands, or harvest credentials. Especially in AI-integrated monitoring systems.
Data poisoning
When IoMT data feeds AI models used for diagnostics or analytics, attackers may inject false data. The possible results: misinformed decisions, faulty treatment plans, or eroded trust in clinical tools.
SQL injection
If hospital systems connected to IoMT sensors don't validate user input, attackers can launch a SQL injection by manipulating backend SQL queries. This can expose patient records or disrupt device access.
Device hijacking
Attackers can remotely take over a vulnerable device—like a wearable, implantable, or imaging system—and use it to extract data, alter behavior, or pivot into the broader network.
How does IoMT security work?
IoMT security is a layered process that protects connected medical devices, the networks they run on, and the data they generate.
Each layer introduces different risks. So each requires specific controls.
It starts with device identification and network segmentation.
You need to know what's connected, what it's doing, and whether it should be there. Many healthcare environments use asset discovery tools and IoT-aware network monitoring to build and maintain this visibility.
From there, traffic must be controlled and inspected.
IoMT systems often operate in flat networks with little separation. But security frameworks recommend isolating critical devices, limiting east-west movement, and inspecting traffic with deep packet inspection or anomaly detection. This is where intrusion detection systems (IDS) or Zero Trust policies are often introduced.
Data protection is next.
That includes encrypting traffic, restricting access, and validating the integrity of transmitted health data. Many attacks—like spoofing, injection, or AI-generated impersonation—target this layer. So endpoint behavior, transmission protocols, and cloud sync processes all need scrutiny.
Finally, threat response and lifecycle oversight matter.
Devices need to be patched. Or isolated if they can't be. Logs must be reviewed. Events must be correlated. And the organization needs a plan for handling an alert, including how to contain an infected device or shut down a compromised system.
In short: IoMT security isn't a single tool or step. It's continuous monitoring and risk reduction across a fragmented and high-stakes environment.
How does IoMT security fit into a broader healthcare cybersecurity strategy?
IoMT security is not a separate track. It's part of the larger effort to secure clinical infrastructure, sensitive data, and patient safety.
In most healthcare environments, medical devices share the same networks, cloud integrations, and IT services as broader hospital systems. So IoMT risks don't stay isolated. They ripple outward.
Which means:
IoMT security needs to plug into a unified cybersecurity strategy that includes Zero Trust, strong identity management, continuous monitoring, and coordinated response.
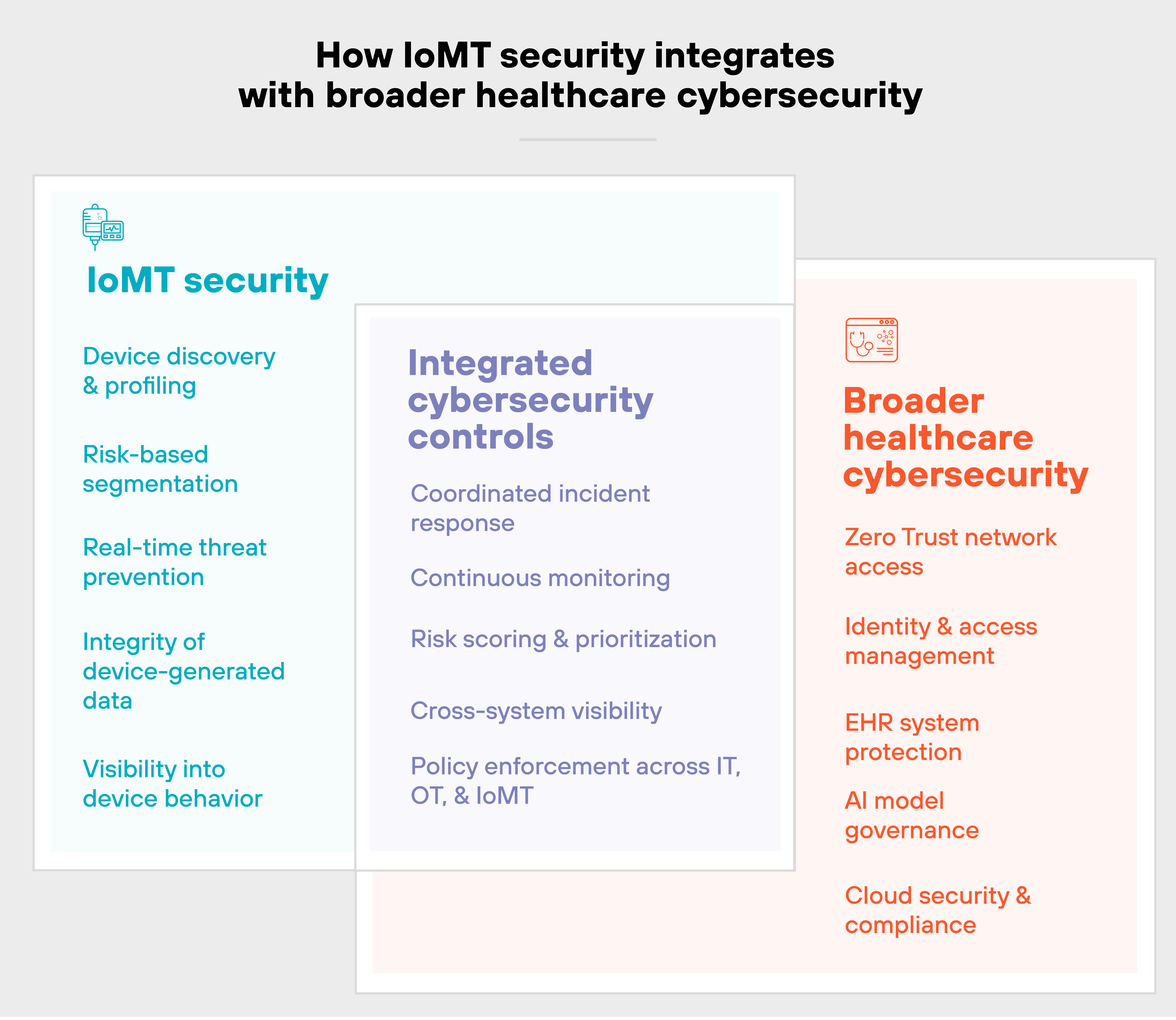
You can't just protect devices in a vacuum. You have to assess how they interact with other systems, like EHR platforms, AI diagnostics, and cloud-based care delivery.
That's especially true as AI becomes more common.
IoMT devices are increasingly feeding data into AI tools used for triage, imaging, or treatment recommendations. If those inputs are compromised, the downstream consequences can be serious.
So protecting IoMT data integrity is becoming just as important as securing the devices themselves.
In short:
Strong IoMT security should integrate with existing tools and teams. Not replace them.
It should complement your broader strategy, not compete with it. That's how you reduce fragmentation, avoid gaps, and build a more resilient healthcare environment.
What frameworks, standards, and regulations guide IoMT security?
There's no single rulebook for securing IoMT. Instead, organizations rely on a mix of security frameworks, technical standards, and regulatory requirements to guide their approach.
Some focus on managing cybersecurity risk. Others define safety requirements for medical devices. And a few provide tailored controls for specific environments, like cloud-based healthcare systems or AI-enabled diagnostics.
Here's a breakdown of the most relevant ones:
| IoMT security frameworks, standards, and regulations | |||
|---|---|---|---|
| Name | Type | Description | Applies to |
| NIST Cybersecurity Framework (CSF) | Framework | A voluntary framework that helps organizations assess and manage cybersecurity risk. Often used as a foundational model for healthcare cybersecurity programs. | All sectors |
| NIST SP 800-53 | Standard | Provides detailed controls for securing federal systems, including connected devices. Often used to benchmark device-level protections and system-level risk management. | Government and critical infrastructure |
| NIST SP 800-66 Rev. 2 | Guidance | Maps HIPAA Security Rule requirements to NIST cybersecurity controls. Useful for aligning IoMT security with U.S. regulatory expectations. | U.S. healthcare providers |
| ISO/IEC 80001-1 | Standard | Focuses on risk management for IT networks that incorporate medical devices. Offers principles for safety, effectiveness, and data security. | Clinical networks using IoMT |
| ISO/IEC 27001 | Standard | Provides a framework for building and managing an information security management system (ISMS). Often used to structure governance for IoMT systems. | Broadly applicable |
| MDCG Guidance (Medical Device Coordination Group) | Regulation guidance | Offers EU regulatory interpretation under the Medical Device Regulation (MDR). Includes security expectations for software and connected devices. | EU manufacturers and providers |
| FDA Premarket Guidance for Cybersecurity in Medical Devices (2023) | Regulatory guidance | Sets expectations for manufacturers on designing and documenting cybersecurity in medical devices. Includes requirements for SBOMs, threat modeling, and patching. | U.S. device manufacturers |
| Health Industry Cybersecurity Practices (HICP) | Framework | A voluntary U.S. framework outlining best practices for protecting patient data and connected systems. Includes specific IoT and medical device considerations. | U.S. healthcare sector |
| ENISA IoT and ICS Guidelines | Guidelines | Offers cybersecurity guidance for IoT and operational technology in Europe. Useful for IoMT implementations in hospitals and clinical environments. | EU healthcare and industrial sectors |
| ISO/IEC TR 24028 | Technical report | Describes AI-specific risks and trust considerations. Relevant for AI-enabled medical devices that rely on IoMT data streams. | AI-integrated healthcare systems |
