- What Is Attack Surface Management?
- What Is Exposure Management?
- ASM Tools: How to Evaluate and Select the Best Option
- What Is Continuous Threat Exposure Management (CTEM)?
-
What Is External Attack Surface Management (EASM)?
- External Attack Surface Management Explained
- Internal vs. External Attack Surface Management
- How External Attack Surface Management Works
- Why EASM Is Important
- Use Cases for External Attack Surface Management
- Benefits of EASM
- Approaches to Attack Surface Management
- EASM Challenges
- How to Choose an Attack Surface Management Platform
- External Attack Surface Management FAQs
- What Are the Types and Roles of Attack Surface Management (ASM)?
-
What Are Common Use Cases for Attack Surface Management?
- What Is the Purpose of Attack Surface Management?
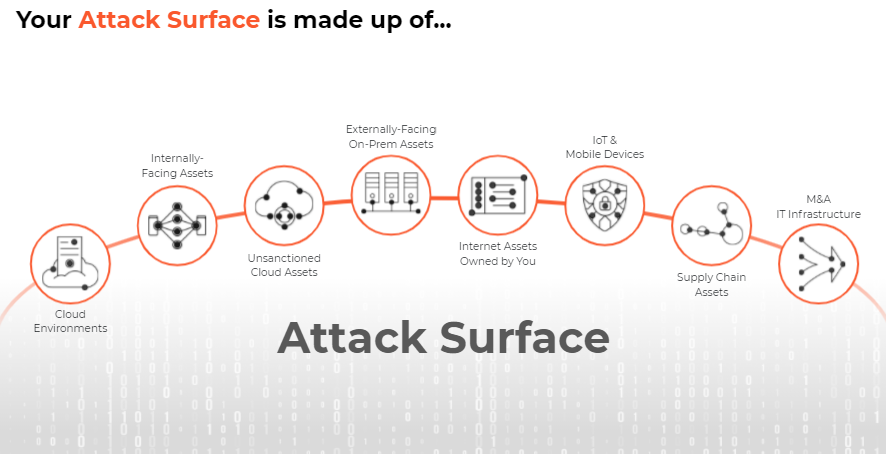
- Decoding the Attack Surface: Ten Examples
- Understanding ASM from the Threat Actor’s Perspective
- Ethical Hackers and Attack Surface Management: A Unique Use Case
- Examples of Attack Surface Management Use Cases
- Common Use Cases for Attack Surface Management FAQ
- How Does a CISO Effectively Manage the Attack Surface?
- What Is the Attack Surface Management (ASM) Lifecycle?
- What is Attack Surface Assessment?
What is the Difference Between Attack Surface and Threat Surface?
Distinguishing between threat surface and attack surface, two often interchanged terms is crucial in understanding cybersecurity dynamics. The threat surface encompasses all the potential threats that can exploit vulnerabilities in a system, including malware, phishing, and insider threats. It broadly reflects how a cyber attacker can harm an organization. A threat can be internal (e.g., a malicious insider) or external (e.g., a hacker).
The attack surface refers to the sum of all possible points where an unauthorized user can try to enter or extract data from an environment. This includes all exposed and vulnerable software, network, and hardware points. Key Differences are as follows:
- Threats are potential security risks, while attacks are exploitations of these risks; actual attempts to exploit vulnerabilities.
- Threats can be internal or external, while attacks are typically external.
- Threats can be prevented by implementing security measures, while attacks can only be detected and responded to.
Examples of threats and attacks include:
- Threat: A software vulnerability that could allow an attacker to gain unauthorized access to the system.
- Attack: A hacker exploiting the software vulnerability to gain unauthorized access to the system.
Defining the Attack Surface
As technology evolves, so does the complexity of attack surfaces, making it imperative for cybersecurity professionals to assess and mitigate risks continuously. Attack surfaces can be broadly categorized into digital, physical, and social engineering.
- Digital attack surfaces relate to software, networks, and systems where cyber threats like malware or hacking can occur.
- Physical attack surfaces involve tangible assets such as servers, computers, and physical infrastructure that can be accessed or manipulated.
- On the other hand, social engineering attack surfaces exploit human interaction and behavior to breach security protocols.
Identifying and securing these varied surfaces is a dynamic challenge that requires a comprehensive understanding of cybersecurity principles and practices.
Attack Vectors and Threat Vectors
Attack vectors are methods or pathways through which a hacker gains unauthorized access to a system to deliver a payload or malicious outcome. These vectors can range from phishing emails to exploiting software vulnerabilities. An attack is when the threat is realized or exploited, and actual harm is done.
This could be through various means, such as credential compromise, malware, cross-site scripting attacks, phishing, DDoS, social engineering, ransomware incidents, or zero-day attacks. Attacks are intentional and involve specific tactics, techniques, and procedures (TTPs) aimed at achieving a particular objective, such as a break-in by compromising entry points, stealing sensitive information, or disrupting services.
On the other hand, threat vectors are how potential attacks could be delivered or the source of a possible threat. While attack vectors focus on the method of attack, threat vectors emphasize the potential risk and source of that attack. Recognizing these two concepts' distinctions is vital for developing effective security strategies.
The key difference between a cybersecurity threat and an attack is that a threat could lead to an attack, which could cause harm, but an attack is an actual malicious event. The primary difference between the two is that a threat is potential, while an attack is actual.
Common Attack Vector Examples
Phishing scams stand out as a prevalent attack vector, tricking users into divulging sensitive information by mimicking legitimate communication channels. Cybercriminals craft emails or messages that appear to originate from trusted sources, urging recipients to click on malicious links or attachments, leading to data breaches or malware installation.
Another significant vector involves exploiting software vulnerabilities. Attackers identify and leverage weaknesses in software to initiate unauthorized actions. These vulnerabilities can range from unpatched software to outdated systems that lack the latest security features.
SQL injection attacks target web applications by inserting malicious SQL statements into input fields, aiming to manipulate databases to access or corrupt data. Meanwhile, cross-site scripting (XSS) attacks exploit web applications by injecting malicious scripts into content viewed by other users, potentially compromising sensitive information.
Difference Between Attack Vector and Threat Vector
Attack vectors are specific methods or pathways through which threat actors exploit vulnerabilities to launch attacks. As previously discussed, these include tactics like phishing scams, software exploits, and SQL injections. They are the actual means by which an attacker breaches a system, focusing on the technical aspect of the intrusion.
Threat vectors are broader in scope, encompassing not only the methods of attack but also the potential sources and motivations behind them. This can range from individual hackers seeking financial gain to state-sponsored entities aiming for espionage.
While attack vectors are the "how" of a cyber-attack, threat vectors consider the "who" and "why," providing a comprehensive view of the risk landscape. Understanding the distinction helps craft more effective security strategies, tailoring defenses against specific techniques, actors, and their intentions behind them.
Attack Surface Management and Analysis
Attack Surface Management and Analysis are critical components in cybersecurity. They focus on identifying, assessing, and mitigating vulnerabilities within an organization's digital and physical environment. This process thoroughly examines all points where an unauthorized user could enter or extract data from a system.
Effective attack surface management requires a comprehensive understanding of the surface's assets, including network interfaces, software applications, and even human elements. By continuously monitoring and analyzing these components, organizations can detect changes in their attack surface, enabling them to respond to new threats proactively.
Attack Surface Reduction Strategies
Embracing attack surface reduction strategies is akin to fortifying a fortress, which aims to minimize vulnerabilities and limit the avenues attackers can penetrate.
- One effective method involves the principle of least privilege, ensuring that individuals and systems have only the access necessary to perform their roles, thereby reducing potential entry points for attackers.
- Regularly updating and patching software also plays a crucial role in addressing security flaws that could be exploited.
- Segmenting networks can isolate critical systems and data, making it more challenging for attackers to move laterally across a network if they gain access.
- Employing comprehensive threat modeling to anticipate and prepare for potential attack scenarios allows organizations to tailor their defenses more effectively.
When implemented diligently, these strategies significantly shrink the attack surface, creating a more resilient security posture against evolving cyber threats.
Attack Surface Analysis vs Management
Attack surface analysis involves meticulously identifying and cataloging every potential entry point attackers could exploit, from unpatched software to misconfigured networks. This comprehensive inventory is the foundation for effective management, focusing on continuously monitoring and mitigating these vulnerabilities.
The various entry points and potential vulnerabilities an attacker may exploit include the following.
- Authentication mechanisms - Methods used to authenticate and verify the identity of users
- Configuration settings - A misconfiguration in a server, application, or network device that may lead to security weaknesses
- Data storage locations - Databases, file systems, and cloud storage where sensitive data is stored
- Exposed services and software interfaces - Web services, APIs, network services, software integration points, and other services accessible over a network.
- Hardware devices - IoT devices, servers, routers, and other physical devices connected to a network
- Network interfaces - Physical and virtual network interfaces (e.g., wi-fi) that connect systems to networks
- Open ports - Ports that are open and listening for incoming connections on servers and network devices
- Software vulnerabilities - Weaknesses or flaws in software code that an attacker could exploit
- Third-party integrations - Connections and integrations with external systems, services, or partners
- User accounts and credentials - Accounts with access privileges and a user’s associated password or credential
- User input points - Web forms, input fields, and other user interaction points in applications
Unlike reduction strategies that minimize potential attack vectors, management adopts a dynamic approach, adapting to new threats as they arise. This includes deploying advanced security measures such as intrusion detection systems and conducting regular security audits to ensure that defenses remain robust.
This strategic blend of analysis and management enhances an organization's security posture and ensures a more agile response to potential breaches.
Real-World Examples of Attack Surface Exploits
Real-world examples of attack surface exploits vividly illustrate the vulnerabilities that attackers can exploit in both digital and physical realms. A digital attack surface breach might involve exploiting unpatched software vulnerabilities, leading to unauthorized access to sensitive data. Attackers often scan for open ports, outdated applications, or weak encryption to find a way into the system.
On the other hand, a physical attack surface breach could involve gaining physical access to a network through unlocked doors or unattended computers, allowing for direct data theft or the installation of malicious software.
Digital Attack Surface Breach Example
One notable instance of a digital attack surface breach occurred when hackers exploited a zero-day vulnerability in a widely used software. This vulnerability, previously unknown to the software developers, allowed attackers to bypass security measures and gain unauthorized access to confidential information.
The breach was orchestrated through a sophisticated phishing campaign targeting employees within the organization. Once an employee clicked on a malicious link, the attackers deployed ransomware across the network, encrypting data and demanding payment for its release.
This incident highlights the critical need for continuous monitoring and updating of digital infrastructures. It also emphasizes the importance of educating employees about the risks of phishing emails and other social engineering tactics that can serve as entry points for cyberattacks.
Physical Attack Surface Breach Example
A striking physical attack surface breach unfolded at a high-security data center. Intruders exploiting lax physical security measures impersonated maintenance staff and gained unfettered access to the facility. Armed with only counterfeit identification and a convincing guise, they bypassed biometric scanners and security checkpoints designed to thwart unauthorized entry.
Inside, they accessed critical servers and installed hardware-based keyloggers, capturing sensitive data directly from the source. This breach underscores the often-overlooked aspect of physical security in safeguarding against cyber threats. It is a stark reminder that robust cybersecurity measures must extend beyond the digital frontier, encompassing comprehensive physical security protocols to protect against all forms of intrusion.
Human Attack Surface
This involves exploiting a human vulnerability. Common attack vectors include tricking users into revealing their login credentials through phishing attacks, clicking a malicious link and unleashing ransomware, or using social engineering to manipulate employees into breaching security protocols.
Protecting Your Digital and Physical Assets
Protecting your digital and physical assets requires a multifaceted approach, blending cybersecurity measures with traditional security protocols.
Start by assessing your threat surface, identifying all possible points of vulnerability, from software and network infrastructure to physical devices and human elements. Equally, understanding the attack surface—those vulnerabilities exploitable by attackers—allows for prioritized defense strategies.
Implement consistent, resilient cybersecurity practices, including regular software updates, strong encryption methods, and comprehensive employee training against phishing and social engineering attacks. On the physical front, secure hardware access, employ surveillance systems and establish strict access controls.
Bridging the gap between digital and physical security ensures that IoT devices are also safeguarded, as these can serve as entry points for cyber threats. By adopting a holistic security posture that addresses both the threat and attack surfaces, organizations can fortify their defenses against the evolving landscape of cyber and physical threats.
Frequently Asked Questions
The three attack surface types are:
- Digital attack surface
- Human attack surface
- Physical attack surface
- Authentication mechanisms
- Configuration settings
- Data storage locations
- Exposed services and software interfaces
- Hardware devices
- Network interfaces
- Open ports
- Software vulnerabilities
- Third-party integrations
- User accounts and credentials
- User input points