- What Is Attack Surface Management?
- What Is Exposure Management?
- ASM Tools: How to Evaluate and Select the Best Option
- What Is Continuous Threat Exposure Management (CTEM)?
-
What Is External Attack Surface Management (EASM)?
- External Attack Surface Management Explained
- Internal vs. External Attack Surface Management
- How External Attack Surface Management Works
- Why EASM Is Important
- Use Cases for External Attack Surface Management
- Benefits of EASM
- Approaches to Attack Surface Management
- EASM Challenges
- How to Choose an Attack Surface Management Platform
- External Attack Surface Management FAQs
-
What Are Common Use Cases for Attack Surface Management?
- What Is the Purpose of Attack Surface Management?
- Decoding the Attack Surface: Ten Examples
- Understanding ASM from the Threat Actor’s Perspective
- Ethical Hackers and Attack Surface Management: A Unique Use Case
- Examples of Attack Surface Management Use Cases
- Common Use Cases for Attack Surface Management FAQ
- How Does a CISO Effectively Manage the Attack Surface?
- What Is the Attack Surface Management (ASM) Lifecycle?
- What is Attack Surface Assessment?
- What is the Difference Between Attack Surface and Threat Surface?
What Are the Types and Roles of Attack Surface Management (ASM)?
Attack surface management (ASM) involves identifying, monitoring, and reducing potential security vulnerabilities in an organization's IT infrastructure. ASM can be divided into several types, each playing a distinct role in creating a comprehensive security strategy.
This ensures that both external and internal threats are effectively managed, human factors are addressed, and third-party and digital risks are minimized. The roles involved in minimizing an organization's exposure to cyberattacks include continuous asset discovery, risk assessment, prioritization, remediation, and continuous monitoring.
The 4 Most Commonly Observed Security Attacks
Among the myriad of security threats, four types stand out due to their prevalence and impact: malware attacks, phishing attacks, denial of service (DoS) and distributed denial of service (DDoS) attacks, and man-in-the-middle (MitM) attacks.
Each of these attacks exploits different elements of an organization's attack surface, underscoring the need for a comprehensive and proactive ASM strategy. Understanding these common attack vectors is essential for developing robust defenses and ensuring the resilience of an organization's digital assets.
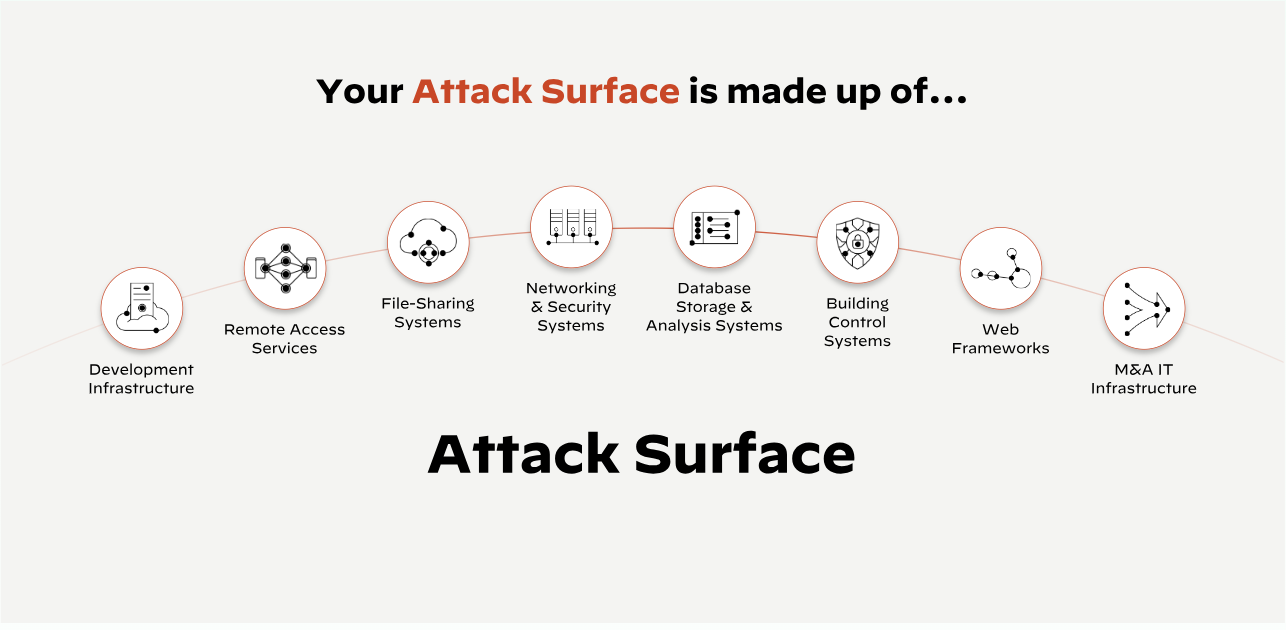
An attack surface is the total number of entry points, vulnerabilities and weaknesses an adversary can exploit to gain unauthorized access to a system or network
Types of Attack Surface Management
Under the umbrella of attack surface management, several specialized categories focus on specific types of assets and their related attack surfaces. All of these attack surface management solutions provide continuous monitoring, identify internal assets and their configurations, assess security controls, and ensure compliance with security policies (e.g., keeping systems up to date and supporting access controls). They include:
- External ASM (EASM)
- Internal ASM (IASM)
- Cyber Asset ASM (CAASM)
- Open Source ASM (OSASM)
External Attack Surface Management (EASM)
EASM solutions address attack surfaces in a network environment, providing continuous discovery and assessment of any internet-facing asset, such as public web servers, APIs, SSL certificates, and cloud services. They track changes and analyze vulnerabilities to deliver real-time insights into vast and dynamic surfaces.
Exposures detected with EASM include exposed servers, credentials, public cloud service misconfigurations, deep web and dark web disclosures, and third-party partner software code vulnerabilities.
Internal Attack Surface Management (IASM)
This attack surface management solution focuses on managing risks within an organization’s internal network. Issues addressed with internal attack surface management solutions include unauthorized access, privilege misappropriation, and service disruptions. IASM aims to reduce the risk of threats originating from within an organization.
Cyber Asset Attack Surface Management (CAASM)
CAASM centers around the comprehensive visibility of asset inventory, both internal and external. Essentially, CAASM combines the capabilities of IASM and EASM to provide a holistic view of an organization’s digital footprint, including endpoints, servers, devices, and applications.
Data is gathered from internal sources like asset discovery, IT asset management, endpoint security, vulnerability management, and patch management tools. External sources, such as ticketing systems, also provide data via API integrations. CAASM identifies vulnerabilities and gaps in security controls.
Open Source Attack Surface Management (OSASM)
This specialty area addresses a growing concern of CISOs—risks associated with open-source components, which can include issues related to maintenance, licensing, and dependencies. These tools help identify exposed assets, detect vulnerabilities, and monitor for changes that could increase risk for solutions that have open-source components.
Categories of Attack Surfaces
Understanding the different categories of attack surfaces ensures that cybersecurity measures adhere to acceptable security ratings. To do this, specific strategies and tools are required to protect the entire attack surface. Security teams must consider three categories of attack surfaces when using attack service management solutions.
Physical Attack Surface
The physical attack surface includes any physical access points into an organization's IT infrastructure. Examples of physical attack surfaces include:
- Discarded hardware—devices that contain user data or login credentials
- Endpoint devices—desktop systems, laptops, mobile devices, and USB ports
- Environmental controls—temperature and humidity controls; systems for air filtration systems, fire suppression, and water detection systems; redundant power supplies; and physical security measures, such as surveillance cameras, controlled access, and security personnel
- Network infrastructure—servers, ports, wiring, network cables, and data centers
- Physical security breaches—unauthorized personnel gaining access to secure locations or passwords being physically stolen or copied when passwords are written on physical materials (e.g., notepad, whiteboard, or sticky note)
Human Attack Surface
The behaviors and interactions of any person with access to an organization's systems, applications, or data can be considered a vulnerability or risk. Managing the human attack surface involves educating and training employees, implementing strong security policies, and fostering a culture of cybersecurity awareness to minimize the risk of human-related vulnerabilities.
The human attack surface includes these members whom cyber attackers can exploit in the following ways:
- Social Engineering: Techniques like phishing, pretexting, and baiting that manipulate individuals into divulging sensitive information or performing actions that compromise security.
- Insider Threats: Risks posed by employees, contractors, or other insiders who intentionally or unintentionally cause harm to the organization’s security, such as leaking information or mishandling sensitive data.
- Human Errors: Mistakes made by employees, such as misconfiguring systems, using weak passwords, or falling for phishing scams, that can lead to security breaches.
- Training and Awareness Gaps: Lack of proper cybersecurity training and awareness among staff, making them more susceptible to cyber threats and less likely to follow security protocols effectively.
Digital Attack Surface
The digital attack surface, considered the broadest, comprises all cyber assets, such as software, hardware, and cloud-based resources, that are internet-facing. Subcategories of the digital attack surface are:
- Cloud attack surface—vulnerabilities in cloud configurations, APIs, storage, services (e.g., IaaS, PaaS, and SaaS), containers, and microservices
- External attack surface—an internet-facing asset that is externally visible and accessible, such as public websites and web services
- Internal attack surface—vulnerabilities within an organization’s internal network, including applications, user privileges, and data storage
- Network attack surface—all points of interaction with an organization’s network, such as routers, firewalls, and network protocols
- Software attack surface—vulnerabilities within software applications, such as software bugs, insufficient input validation, and insecure APIs
The 5 Primary Roles of ASM
Attack surface management proactively plays five primary roles in supporting an organization’s overall security posture. Attack surface management solutions continuously poke and probe, just like an attacker would. The result is real-time insights that help security teams proactively remediate attack vectors that could be used for a cyber attack, such as data breaches or ransomware attacks.
Continuous Asset Discovery
An attack surface management solution adopts the perspective of an attacker. This approach focuses on identifying all digital assets and their associated cyber risk. Continuous asset discovery ensures that security teams know an organization’s attack surface.
The asset discovery process involves systematically scanning and cataloging every asset connected to the organization’s network. This includes discovering on-premise systems like servers and workstations and cloud-based assets such as instances and storage buckets, web applications, IoT devices, and any third-party services integrated into the organization’s ecosystem.
Asset discovery maintains a comprehensive, up-to-date inventory that includes not only known and managed assets but also unknown assets and potentially unauthorized (i.e., shadow IT) assets, whether on-premise, cloud-based, or hosted by a third party.
Risk Assessment
With attack surface management, the asset inventory (i.e., on-site or off-site) is analyzed. Context is provided for each asset’s vulnerability and potential severity impact. This contextual data includes risk scoring and security ratings for identified vulnerabilities based on usage, ownership, location, and network connections.
Prioritization
Based on the risk assessment, security teams can prioritize responses. Attack surface management evaluates and ranks vulnerabilities based on their potential impact and likelihood of exploitation.
This process starts with analyzing the vulnerabilities identified during the asset testing phase. Each vulnerability is assessed for its severity, the criticality of the affected asset, and the potential consequences of exploitation, such as data breaches or system downtime.
Factors like the complexity of the remediation and compliance requirements are also considered. This prioritization enables a fine-grained, data-driven remediation approach that sees the optimal balance between severity, incident likelihood, difficulty, and available resources.
Remediation
When a potential threat is detected, an attack management solution can be set to automate immediate remediation steps for high-risk threats. Prioritization analysis dictates the timing of responses to other threats to the asset inventory.
These can include anything from steps to prevent unpatched vulnerabilities from being exploited by keeping systems and software up to date to preparing incident response plans to expedite future remediation.
Continuous Monitoring
An organization’s attack surface requires continuous monitoring and testing due to the dynamic nature of IT environments where new tools and users are constantly added, and threat actors change and evolve attack vectors.
Continuous monitoring makes proactive security possible by regularly scanning and analyzing the entire network. It includes every endpoint, cloud service, web application, and other internet-facing asset to detect new devices, software updates, and configuration changes, identifying potential vulnerabilities as they arise.
This real time surveillance provides security teams with valuable threat intelligence that helps them promptly identify potential vulnerabilities caused by new assets being added, unauthorized changes, or signs of compromise.
Important Functions of Attack Surface Management
In addition to the primary roles of attack surface management, ASM encompasses a number of other core functions. These work in concert to provide a comprehensive view of cyber risk and enable a proactive approach to managing and securing an organization’s asset inventory against attack vectors exploitable by threat actors.
Addressing Misconfigurations
Attack surface management systematically scans and analyzes an organization’s asset inventory to identify misconfigured networks, servers, applications, and cloud services. Scans and analysis include checking for improper security settings, default credentials, unnecessary open ports, and incorrectly set permissions.
Once identified, these misconfigurations are reported for remediation. Attack surface management also supports implementing best practices and guidelines for configurations to prevent such issues from arising in the future.
Testing Assets
In attack surface management, identified assets are rigorously tested for vulnerabilities on an ongoing basis. This process involves various tools and techniques, such as vulnerability scanners, penetration testing, and security audits. The objective is to assess assets' resilience against potential cyber threats by uncovering attack vectors like software bugs, misconfigurations, outdated systems, and insecure APIs.
The test results provide insights into each asset's security posture to facilitate remediation prioritization. Regularly testing assets ensures an organization can proactively address security gaps and adapt to emerging threats.
Providing Asset Inventory Context
Contextualization takes ASM’s asset identification a step further, providing details about how, where, and by whom these assets are used, along with their connectivity to other systems. This insight allows security teams to deploy targeted security measures based on the role and importance of assets within the organization. Examples of ASM contextualization are identifying a server as a publicly facing web server or a database that stores sensitive data, such as protected health information (PHI), that requires heightened security to meet HIPAA compliance requirements.
Vulnerability Management
The vulnerability management component of attack surface management covers systematic processes that continuously identify, classify, remediate, and mitigate vulnerabilities within an organization's digital assets. This involves continuously scanning and assessing the network, applications, and systems to identify security weaknesses.
Each vulnerability is evaluated for its severity, potential impact, and susceptibility to exploit. This assessment helps prioritize which vulnerabilities require immediate attention and which can be scheduled for later remediation.
Types and Roles of Attack Surface Management FAQs
While these both protect against threats, they focus on different parts of the attack surface. Internal attack surface management (IASM) identifies vulnerabilities within an organization's internal network, including servers, databases, and user devices.
It detects vulnerabilities, such as misconfigurations, unpatched software, or rogue devices that could be exploited by an insider threat or a threat actor who has gained unauthorized access. External attack surface management (EASM) monitors an organization's public-facing digital presence, such as websites, cloud services, or exposed APIs.